Troubles with Meltdown and Spectre security patches
During his CES keynote on Monday, Intel CEO Brian Krzanich said that updates for Meltdown and Spectre for more than 90 percent of the company’s processors introduced in the past five years will be released by the end of the week, and the rest by the end of January.

“We believe the performance impact of these updates is highly workload-dependent. As a result, we expect some workloads may have a larger impact than others, so we will continue working with the industry to minimize the impact on those workloads over time,” he noted.
“As of now, we have not received any information that these exploits have been used to obtain customer data. And we are working tirelessly on these issues to ensure it stays that way. The best thing you can do to make sure your data remains safe is to apply any updates from your operating system vendor and system manufacturer as soon as they become available.”
On the same day, via an internal memo, he also told employees that Intel will gain a new internal security group.
According to OregonLive, who got their hands on the memo, the Intel Product Assurance and Security group will be run by Intel human resources chief Leslie Culbertson. She will be joined by Josh Walden, the current head of Intel’s new technology group, and Steve Smith, Intel VP and general manager of its data center engineering group.
Krzanich continued to stress that the Meltdown and Spectre vulnerability were not just an Intel issue, but affected the whole chip-making industry. Nevertheless, the company has been hit with class-action lawsuits over the processor vulnerabilities in several US states.
Problems with patch implementation
Apple issued patched for Meltdown last week, and then on Monday it pushed out Spectre-mitigation patches via security updates for iOS 11, macOS High Sierra, Sierra, and OS X El Capitan (the patches contain security improvements to Safari and WebKit). For now, they seem stable.
Microsoft users, on the other hand, encountered some problems with the implementation of patches: namely, those who have incompatible antivirus software have not been offered the security update.
“The compatibility issue arises when antivirus applications make unsupported calls into Windows kernel memory. These calls may cause stop errors (also known as blue screen errors) that make the device unable to boot,” the company explained.
“To help prevent stop errors that are caused by incompatible antivirus applications, Microsoft is only offering the Windows security updates that were released on January 3, 2018, to devices that are running antivirus software that is from partners who have confirmed that their software is compatible with the January 2018 Windows operating system security update.”
In order to receive the update, their AV must set up a specific registry key:
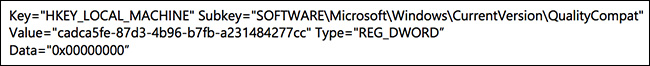
Customers will not receive the January 2018 security updates (or any subsequent security updates) and will not be protected from security vulnerabilities unless their antivirus software vendor sets the key or they do it themselves.
Vulnerability manager Kevin Beaumont has compiled and keeps updating a list of compatible AV solutions.
“For information about how to edit the registry, view the ‘Changing keys and values’ help topic in Registry Editor (Regedit.exe) or view the ‘Add and delete information in the registry’ and ‘Edit registry data’ help topics in Regedt32.exe,” Microsoft instructed, but also advised users to be careful when editing the registry.
Whether these and other security updates result in the slowdown of your computers and devices will depend on the machines and what you use them for. The Register has compiled a helpful overview of the consequences experienced by some services and users who implemented the Meltdown patches, but it will take some time to gauge the effect of Spectre patches.
UPDATE:
Microsoft has temporarily paused the rollout of Windows updates to devices with AMD processors.
“Microsoft has reports of customers with some AMD devices getting into an unbootable state after installing recent Windows operating system security updates. After investigating, Microsoft has determined that some AMD chipsets do not conform to the documentation previously provided to Microsoft to develop the Windows operating system mitigations to protect against the chipset vulnerabilities known as Spectre and Meltdown,” the company explained.
“Microsoft is working with AMD to resolve this issue and resume Windows OS security updates to the affected AMD devices via Windows Update and WSUS as soon as possible.”