How often are users’ DNS queries intercepted?
A group of Chinese researchers wanted to find out just how widespread DNS interception is and has presented the result of their large-scale study to the audience at the Usenix Security Symposium last week.
The problem
Most Internet connections are preceded by a DNS address lookup request, as the Domain Name System (DNS) “translates” human-readable web addresses to IP addresses.
DNS queries from clients are handled by recursive nameservers and, usually, users’ recursive nameservers are pointed to the ones operated by ISPs. Users can choose their own DNS servers or public recursive nameservers, but there is no guarantee that their requests won’t be intercepted.
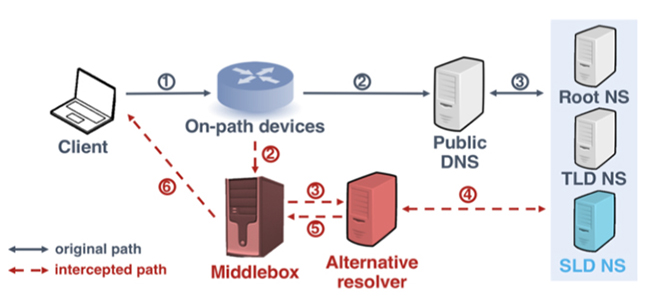
According to the researchers, there are many on-path devices that intercept DNS queries sent to public DNS and respond with DNS answers resolved by alternative recursive nameservers.
These interceptions can be made for various purposes: censorship, displaying ads, collecting statistics, blocking malware connections, etc. But they are not authorized by users and are difficult for them to spot.
“The on-path devices either redirect or replicate the requests to alternative resolvers (typically, local DNS resolvers), which perform the standard resolution process. Finally, before responses are sent from alternative resolvers back to clients, the sources are replaced with addresses of the original resolvers. Therefore, from a client’s perspective, DNS responses appear to come from the original DNS resolvers according to their source addresses, making the actual interception behaviors difficult to be discerned,” the researchers explained.
The findings
The researchers have devised new approaches to detect DNS interception and have leveraged 148,478 residential and cellular IP addresses around the world for analysis.
They found that:
- 259 of the inspected 3,047 ASes 3,047 exhibit DNS interception behavior. (The AS represents a connected group of one or more blocks of IP addresses that have been assigned to an ISP or another organization.)
- Interception behaviors exist in both reputable ASes and those with a lower ranking.
- 27.9% DNS requests over UDP from China to Google Public DNS are intercepted.
- DNS queries over UDP and those for A-type records sent to well-known public DNS services are more likely to be intercepted.
- The DNS servers used by interceptors may use outdated, vulnerable software and lack security-related functionality (57% of the DNS servers do not accept DNSSEC requests).
Surreptitious interception of DNS queries is problematic from the ethical and privacy standpoint.
“Firstly, when DNS requests from clients are handled by alternative resolvers, previous studies have proved it is possible to illegally monetize from traffic. Secondly, as it is difficult for Internet users to detect DNSIntercept merely from clients, public DNS resolvers can be wrongly blamed when undesired results (e.g., advertisement sites or even malware) are returned. Finally, it is possible for intercepted DNS requests to be snooped by untrusted third parties, leading to the leak of privacy data,” the researchers explained.
In addition to this, popular public DNS servers are often deployed with full DNSSEC support and up-to-date DNS software and these alternative resolvers used by intercepters are often not.
The solution for these problems is to encrypt DNS traffic. It can be done but not quickly or easily.
“The deployment of DNS over TLS is sophisticated and needs changes from the client side. As such, the wide deployment of this initiative could take a long time,” they concluded.