Blocking compromised passwords: How and why to do it
Passwords are beginning to feel like the zombie that just won’t die. Even after Bill Gates famously called for their demise in 2004, this antiquated form of user verification is still alive and kicking.
Yet, many remain hopeful that passwords will slowly be phased out as the world move towards stronger authentication. That is not the case with corporate America – more than half of U.S. organizations use only passwords to protect their financial information, according to 2017 State of Authentication report. What makes matters worse is that 25% of the U.S. employees reuse their password across personal and business accounts. This poses a significant problem. Cybercriminals can use a compromised personal account password to gain access to business accounts and potentially an entire business network. With 1.4 billion leaked passwords circulating the Dark Web, organizations that allow these passwords in their environments are asking for a breach.
NIST has spoken – death to compromised passwords
With the current threat landscape in mind, the National Institute of Standards and Technology (NIST) recently updated their Digital Identity Guidelines. Their recommendation urged all applications with user accounts “compare the prospective secrets against a list that contains values known to be commonly-used, expected, or compromised.” The challenge with blocking compromised passwords is that you need a continuously updated list of vulnerable passwords to compare user passwords against, which NIST does not provide.
Is Azure AD password protection the answer?
Azure recently introduced the Azure AD password protection feature. Now in public review, Azure AD password protection allows administrators to prevent users from using 500 commonly used passwords (for example, password), plus over 1 million single-character variants such as p@ssword. The list alone does not satisfy NIST’s new rule to block compromised passwords. Premium customers have the ability to block additional passwords beyond the ones Microsoft provides. However, the list is limited to 1000 words and it is unclear if Microsoft has plans to increase the limit. Considering the amount of leaked passwords that are readily available, blocking 1000 leaked passwords barely creates a hurdle for attackers.
Here is how you block a billion compromised passwords
With Specops Password Blacklist you can block over 1 billion leaked passwords. Specops Password Blacklist is a hosted service, which features a continuously updated and comprehensive leaked password list, including HaveIBeenPwned and more. When this service is enabled, passwords are checked during an Active Directory password change and users are informed to change it at next login if detected on the Blacklist. This capability not only prevents users from using leaked passwords but also informs them as to why they cannot use the password.
Beyond blocking leaked passwords, you also need to prevent users from selecting predictable passwords that are susceptible to dictionary attacks. During a dictionary attack, a hacker uses a dictionary composed of common names, passwords with predictable character substitutions (i.e. P@ssw0rd2017!), foreign words and compromised passwords obtained from data breaches such as LinkedIn, Yahoo, and Adobe.
Specops Password Policy’s dictionary capability allows IT admins to create their own custom dictionary list or download any of the Specops provided lists.

A few more tips
What else can you do to improve password security? Here are a few tips:
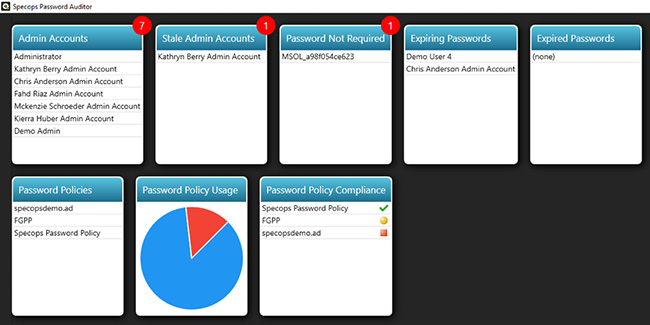
- Scan Active Directory to measure password policy strength and compliance on a continuous basis.
Having too many administrator accounts, inactive accounts and weak password policies can create security gaps in your environment. This free tool scans Active Directory for various security-related weaknesses specifically related to password policies. The collected information is used to generate multiple interactive reports containing user and password policy information. The tool is especially helpful for those organizations bound to compliance requirements as the password settings in your organization are measured against industry standards such as NIST, PCI, Microsoft and SANS.
- Encourage password length
Passwords such as geylmups are not on the leaked list but only take a few minutes to crack because a short password is a weak password. The length of the password is the most effective defense against a brute-force attack. Consider a basic password with only one lowercase letter “a,” the attacker would have 26 possibilities to guess from A to Z. Now increase the password length to two characters, the attacker would have to go through 676 possibilities. You cannot argue with math – the longer the password is, the harder it is to crack.

- Don’t let passwords live forever but don’t set them to expire too frequently either
NIST discourages regular password expiration but requires a password change if there is evidence of compromise. However, removing password expirations entirely is not advised without a stronger authentication method in place, such as multi-factor authentication. A better approach is to base password expiration on the user’s role in the organization. The more access to sensitive information, for example IT administrators, the more likely you want to continue to use password expiration as a way of ensuring a compromised account doesn’t go unnoticed.
Final thoughts
With password security best practices in constant flux, our effectiveness in safeguarding our organization requires scrutiny. Sometimes the regulatory bodies send conflicting messages, but today it is clear that password blacklisting is an effective way to shift the burden from users to authenticators and prevent dictionary attacks. There is no “set it and forget it” when it comes to password policies. It is a continuous process that must respond to user behavioral patterns, and the emergence of new threats.