Which cybersecurity failures cost companies the most and which defenses have the highest ROI?
Massachusetts Institute of Technology (MIT) scientists have created a cryptographic platform that allows companies to securely share data on cyber attacks they suffered and the monetary cost of their cybersecurity failures without worrying about revealing sensitive information to their competitors or damaging their own reputation.
The SCRAM platform allows defenders to learn from past attacks and provides insight into which cyber-risk control areas require additional scrutiny or investment.
Privacy-preserving platform offers answers
“In the past, the only way to aggregate and share information about cyber attacks was through a trusted third party,” explained the students, economists, cryptography and internet policy experts who worked on this project under the auspices of MIT’s Computer Science and Artificial Intelligence Lab (CSAIL).
But that third party could be breached, the data stolen and disclosed. The data could also be accidentally disclosed. For these reasons, companies often refused to participate in such schemes and share information about their losses.
SCRAM (Secure Cyber Risk Aggregation and Measurement) has, according to its creators, solved that longstanding cyber-security problem.
“SCRAM mimics the traditional aggregation technique, but works exclusively on encrypted data that it cannot see. The system takes in encrypted data from the participants, runs a blind computation on it, and returns an encrypted result that must be unlocked by each participant separately before anyone can see the answer,” they explained.
“The security of the system comes from the requirement that the keys from all the participants are needed in order to unlock any of the data. Participants guarantee their own security by agreeing to unlock only the result using their privately held key.”
More technical details about the process and the platform, which consists of a central server, software clients, and a communication network to pass encrypted data between the clients and the server, can be found in this paper.
The cost of cybersecurity failures
The researchers recruited seven large companies that had a high level of security sophistication and a CISO to test out the platform, i.e., to contribute encrypted information about their network defenses and a list of all monetary losses from cyber attacks and their associated defensive failures over a two-year period.
“Firms of this size would have the technological expertise and resources to nominate people on their team to work with us to design the appropriate questions and to perform the internal data collection,” the scientists explained the rationale behind their decision to focus on larger companies.
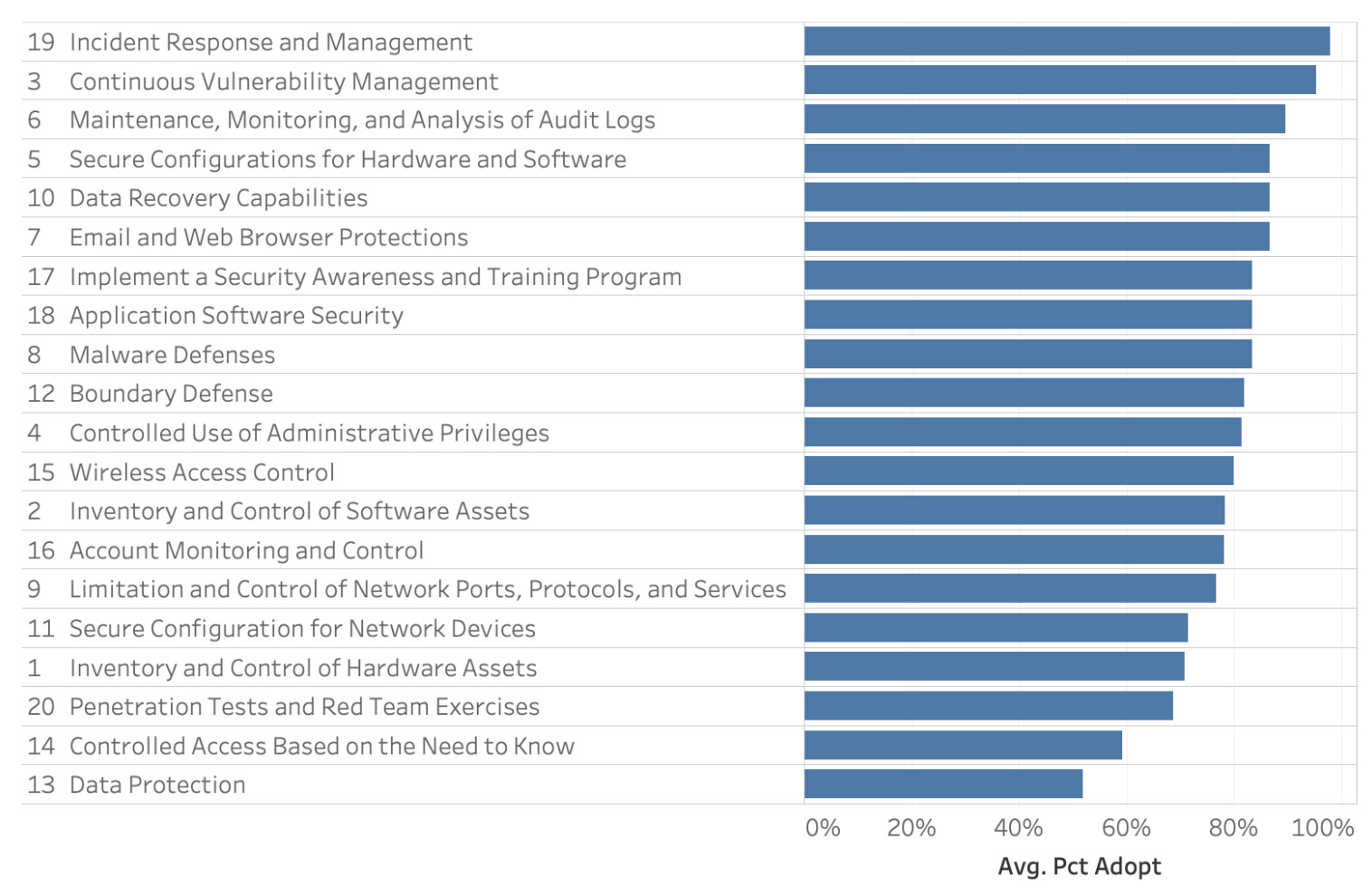
SCRAM returned information about adopted defenses and pointed out which security failures cost companies the most money:
- Failure to prevent malware (and especially ransomware) attacks by relying mostly on anti-malware software, regular backups and reminding employees not to click on suspicious emails
- Despite all of the companies saying that they blocked access to unauthorized ports, attacks involving attackers accessing and communicating over these ports brought about high losses, meaning those defenses weren’t air-tight or were being neglected
- Failure to perform inventory and control of hardware assets
- Failure to perform effective log management and implement ML/AI-powered automated analysis to identify security incidents as they happen (or even to predict and prevent them)

Plans for the future
“These results provide a compelling proof-of-concept for how cyber intrusion data can be shared. Our next step will be to increase the number of incidents in future rounds to produce more robust estimates, more complex analyses, and more generalizable results,” the scientists noted.
“With a larger data sample, we will also be able to explore loss distribution approaches that cover both the frequency and severity of losses. A larger sample size will also reduce the chance of outliers or single incidents leaking the magnitude of an individual event.”
In the meantime, though, they’ve been able to demonstrate to companies that sensitive cyber attack data can be shared and used without being actually being disclosed.
“What this effectively means is that new cryptographic platforms such as SCRAM can gain access to previously ‘untouchable’ data that can then be used to inform market participants and meet important challenges,” they added.
“Many of the target firms for this multi-party computation were interested in participating, but they wanted to see the results of the first computation before contributing their own data. From a cybersecurity standpoint, this represents a new opportunity to create new cybersecurity aggregation pools with greater reach and precision than ever before.”