
Russian hackers crack into officials’ Signal and WhatsApp accounts
Russian state hackers are trying to break into Signal and WhatsApp accounts used by diplomats, military staff, and government officials worldwide, Dutch intelligence agencies …

No more soft play, President Trump warns in new cyber strategy
The White House released “President Trump’s Cyber Strategy for America,” a policy framework outlining the administration’s priorities for maintaining U.S. leadership in …

OpenWrt 25.12.0 ships with new package manager, built-in upgrade tool, support for 2200+ devices
OpenWrt 25.12.0 is now available for download. The release incorporates over 4,700 commits since branching from OpenWrt 24.10. Package manager changes One of the most …

Fake Claude Code install pages highlight rise of “InstallFix” attacks
Users looking for Anthropic’s Claude Code agentic AI coding tool are being tricked via fake Claude Code install pages into running malware, Push Security researchers …

More AI tools, more burnout! New research explains why
Workflows built around multiple AI agents and constant tool switching are adding cognitive strain across large enterprises. A recent Harvard Business Review analysis describes …

OpenAI joins the race in AI-assisted code security
OpenAI introduced Codex Security, an AI agent that reviews codebases to find, verify, and help fix software vulnerabilities. The launch comes a few weeks after rival …

Decoding silence: How deaf and hard-of-hearing pros are breaking into cybersecurity
Stu Hirst was already a CISO when he started to go deaf. It was 2023, and the hearing loss crept in over months, enough for him to adapt, to lean on hearing aids and captions, …

Turning expertise into opportunity for women in cybersecurity
Speaker diversity in cybersecurity has been a talking point for over a decade, with panels, pledges, and dedicated conference tracks failing to produce change. Stages still …

Open-source tool Sage puts a security layer between AI agents and the OS
Autonomous AI agents running on developer workstations execute shell commands, fetch URLs, and write files with little or no inspection of what they are doing. Open-source …
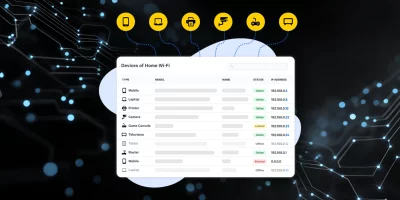
Product Showcase: Fing Desktop puts network visibility on your screen
Phones, laptops, smart TVs, cameras, and smart home equipment all use the same network. Knowing what’s connected helps users manage performance and security. Fing Desktop …

Submarine cables move to the center of critical infrastructure security debate
The cables running along the ocean floor carry the overwhelming majority of the world’s cross-border data traffic, and for most of their operational history they have …

Week in review: Weaponized OAuth redirection logic delivers malware, Patch Tuesday forecast
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: BlacksmithAI: Open-source AI-powered penetration testing framework …
Featured news
Resources
Don't miss
- Fake Claude Code install pages highlight rise of “InstallFix” attacks
- Decoding silence: How deaf and hard-of-hearing pros are breaking into cybersecurity
- Turning expertise into opportunity for women in cybersecurity
- Open-source tool Sage puts a security layer between AI agents and the OS
- Iran-linked APT targets US critical sectors with new backdoors