Crypt0L0cker ransomware avoids US computers
“Yet another piece of ransomware has surfaced, and this one has several interesting things about it: it expressly avoids targeting US users, and it has a hardcoded list of file types it avoids encrypting.
It’s called Crypt0L0cker – the letter “o” has been replaced by zeroes – and, despite the name, the malware has much more in common with TorrentLocker that CryptoLocker.
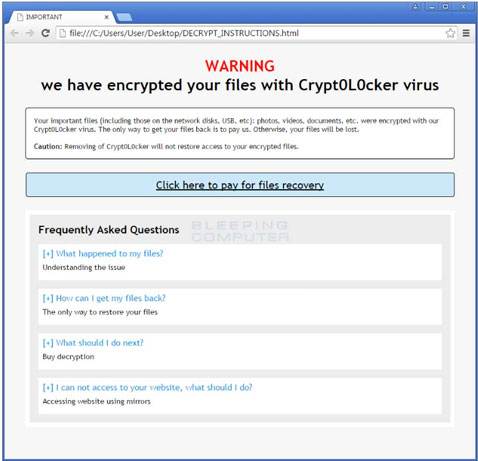
According to a Bleeping Computer admin, this ransomware is currently being distributed through emails that pretend to be traffic violations or other government notices, and targets users in Europe, Asia and Australia.
“When first installed, Crypt0L0cker will connect to a C&C server and send the victim’s unique identifier as well as the campaign ID. The C&C server will then send back the HTML ransom note and the name of the file it should be saved as,” he explained.
The ransomware scans all hard drive letters and encrypts all files that don’t have the following extensions: avi, wav, mp3, gif, ico, png, bmp, txt, html, inf, manifest, chm, ini, tmp, log, url, lnk, cmd, bat, scr, msi, sys, dll, exe. While doing this, it also delete the Shadow Volume Copies of the files so they can’t be recovered by the user.
The ransom amount is currently set at 2.2 Bitcoins (around 450 euros).
“At this time there is no known way to decrypt your files for free,” says the admin, and advises restoring the files from backup. If you haven’t backed them up, you can always try to use recovery software.”