DDoS attacks double, old web application attack vectors still active
Akamai Technologies analyzed thousands of DDoS attacks as well as nearly millions of web application attack triggers across the Akamai Edge network.
A surge in DDoS attack activity
Q1 2015 set a record for the number of DDoS attacks – more than double the number recorded in Q1 2014 – and a jump of more than 35 percent compared to last quarter. However, the attack profile has changed. Last year, high bandwidth and short duration attacks were the norm. But in Q1 2015, the typical DDoS attack was less than 10 Gbps and endured for more than 24 hours.
There were eight mega-attacks in Q1, each exceeding 100 Gbps. While that was one fewer mega-attack than in Q4 2014, such large attacks were rarely seen a year ago. The largest DDoS attack observed in Q1 2015 peaked at 170 Gbps.
Raj Samani, VP and CTO EMEA at Intel Security, finds that the growth of the as-a-service model for DDoS may be one explanation why the number of attacks have increased. “The number of attacks aside, the amount of traffic these services can generate will pose a significant issue for organizations of every size pointing to the need to have some form of mitigation service by default.”
During the past year, DDoS attack vectors have also shifted. This quarter, Simple Service Discovery Protocol (SSDP) attacks accounted for more than 20 percent of the attack vectors, while SSDP attacks were not observed at all in Q1 or Q2 2014. SSDP comes enabled by default on millions of home and office devices—including routers, media servers, web cams, smart TVs and printers—to allow them to discover each other on a network, establish communication and coordinate activities. If left unsecured and/or misconfigured, these home-based, Internet-connected devices can be harnessed for use as reflectors.
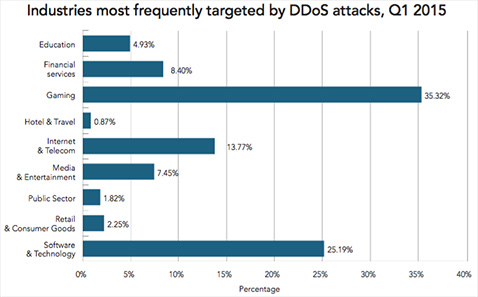
During Q1 2015, the gaming sector was once again hit with more DDoS attacks than any other industry. Gaming has remained the most targeted industry since Q2 2014, consistently being targeted in 35 percent of DDoS attacks. The software and technology sector was the second most targeted industry in Q1 2015, with 25 percent of the attacks.
Web application attacks
For the purpose of this report, Akamai concentrated its analysis on seven common web application attack vectors, which ultimately accounted for 178.85 million web application attacks. These vectors included SQL injection (SQLi), local file inclusion (LFI), remote file inclusion (RFI), PHP injection (PHPi), command injection (CMDi), OGNL Java injection (JAVAi) and malicious file upload (MFU).

During Q1 2015, more than 66 percent of the web application attacks were attributed to LFI attacks. This was fueled by a massive campaign against two large retailers in March, targeting the WordPress RevSlider plugin.
SQLi attacks made up more than 29 percent of web application attacks. A substantial portion of these was related to attack campaigns against two companies in the travel and hospitality industry. The other five attack vectors collectively made up the remaining five percent of attacks.
Accordingly, the retail sector was the hardest hit by web application attacks, followed by the media and entertainment and hotel and travel sectors.
Many of the most common attack vectors detailed in this report, including SQLi, have been around for a long time, in some cases for about 15 years, according to Lee Weiner, Rapid7’s Senior VP of Products & Engineering. “Despite the familiarity of these vulnerabilities and vectors of attack, security programs continue to find discovery and remediation challenging. Security teams need a simple way to test for known risks and vulnerabilities, and communicate to IT about how to address them.”
The complete report is available here (registration required).