Nearly 3 million undetected “Hot Video” pages pushing fake AV
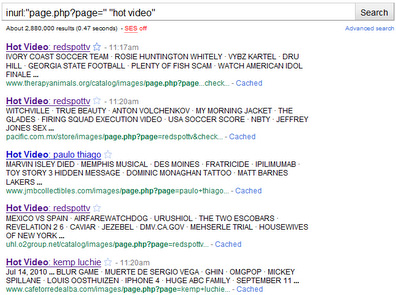
We’ve seen many fake YouTube pages redirecting to fake antivirus software downloads in the past. However, we’re now seeing this same phenomenon with a new twist: Google has indexed nearly 3 million “Hot Video” pages – all pushing fake AV. Yandex, a Russian search engine, also returns numerous links to these pages for random searches. Try the following Google search: inurl:”page.php?page=” “hot video”:
The fake Youtube video page is covered by an invisible Flash layer and the Flash object automatically redirects the user to a fake AV page. If the user has Flash disabled, the page becomes harmless. The URL of the Flash file, hosted on a different domain, is obfuscated with Javascript.

The spam content, which is used to ensure that the page is indexed by search engines, includes an invisible DIV element pushed out of the screen. It contains links to other fake Youtube pages on the same site. To make the content look more legitimate, the page includes links to legitimate sites (e.g. flickr.com, nasa.gov, etc.) and images from external sites.

The fake YouTube page redirects to a fake AV page. Several domains are used to host the fake AV software, including www2.soft-analysis79.co.cc, www1.selfprotection20.co.cc, etc. There are different variations of the fake AV page.
Besides the huge numbers of such malicious pages indexed, and the fact that they show up in many search results, the main problem here is that the pages and their malicious payloads are virtually undetected by regular security tools:
- Google Safe Browsing does not block most of these pages (90% I’ve tried where not blocked in Firefox), and the fake AV domains were not detected either.
- The detection rate amongst anitivrus vendors is only 11%!
This type of threat is different from the usual Balckhat spam SEO: the same content is shown to the user and to the search engine, therefore the page can be accessed directly, without clicking on search engine results.
Because the “Hot Video” page uses both obfuscated Javascript and Flash, it is harder for security scanners to detect them. Zscaler has protection in place for our customers.

Author: Julien Sobrier, Zscaler.