Facebook bug allows user data theft via specially crafted websites
A proof-of-concept attack page that exploits a Facebook vulnerability to access a user’s private data has been devised by two students who shared the information with the social network’s security team and Sophos‘ Graham Cluley.
To demonstrate their claims, they offered Cluley to test the page against a test Facebook account he set up for this purpose.
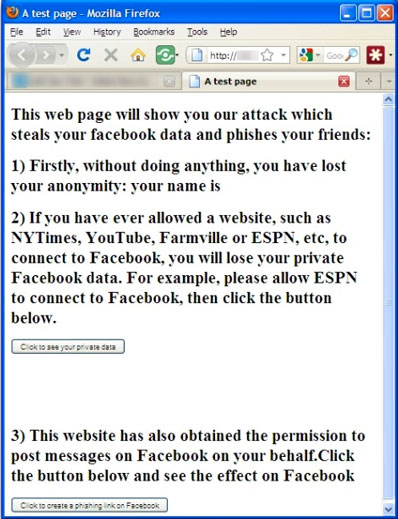
Details about what happens in the background have not, of course, been exposed, but the vulnerability works like this: the malicious website impersonates a site that is allowed to access user’s data in order to harvest it and can also post content on the user’s Wall – a capability that can be misused to spread malicious links and malware.
After a first failed attempt, Cluley has been able to mimic the attack by directly installing the ESPN Facebook application on the account. Using the test site, he harvested the name and e-mail address contained in the account, and posted a message on the Wall that looked like it was published via the ESPN application.
Facebook reacted promptly upon receiving the information about the bug, and the vulnerability has already been patched, but this occurrence points once again to the fact that mammoth-sized and ever-changing sites like Facebook can never be completely bug-free.