Review: Pwnie Express Pulse
Pwnie Express Pulse is a SaaS offering that uses custom hardware sensors to provide continuous network discovery, threat detection, risk assessment, and critical information about all security issues that should be resolved.
After seeing Pulse in action, I can say that Pwnie Express came a long way from being a crowd pleaser at security conferences where people were obsessing over PwnPhone or PwnPlug, a penetration testing device that mimicked a surge protector. In case you are interested in the early days of Pwnie Express, do check out a podcast I’ve recorded with them at InfoSec World 2014 Conference & Expo.
Connecting the sensor
To set up Pwnie Express Pulse, you first have to place a sensor into the company network. There are two types of sensor available: Standard and Professional. I got the Standard sensor, which is, in fact, a Pwn Plug R3 device. The hardware specifications are as follows:
- Processor: 1.1GHz dual-core Intel Celeron (2 threads, 64-bit)
- Memory: 2GB 1600MHz DDR3
- Disk Storage: 32GB mSATA SSD
- Onboard I/O: 1x Gigabit Ethernet, 3x USB ports, HDMI
- USB-Ethernet adapter for second Ethernet interface
- Onboard high-gain dual-band 802.11a/b/g/n wireless supporting
- Packet injection & monitor mode (internal antenna)
- Onboard Bluetooth supporting device scanning & monitor

FYI, the Professional variant of the sensor features a 1.8GHz Intel i3 processor, 4GB DDR3 of memory, detachable WLAN antennas and an accompanying 4G GSM cellular USB adapter.
Before the company ships you the sensors, you may choose to use their preauthorization and configuration service. This will pre-program your device according to the specifications you’ve provided, so you’ll just need to plug the device in your network and you are ready to roll. If you don’t choose to use this service (I didn’t), it is still a rather straightforward process to set up the sensor to connect to Pulse. Once you do that, you won’t need to interact directly with the sensor again, as everything is done from the cloud-based management console.
With Pulse, Pwn Plug’s functionality is absolutely transparent. It lays there and does the work you command it to do from the management console. Apart from that, you can always use the device as a very robust pentesting box. By connecting it to the computer monitor via HDMI and plugging in a USB keyboard, you can login into the custom Pwnie Express Kali distribution and harness its power for any type of manual testing. Pulse also enables on-demand access to a sensor through a reverse SSH connection.
Pwnie Management Console
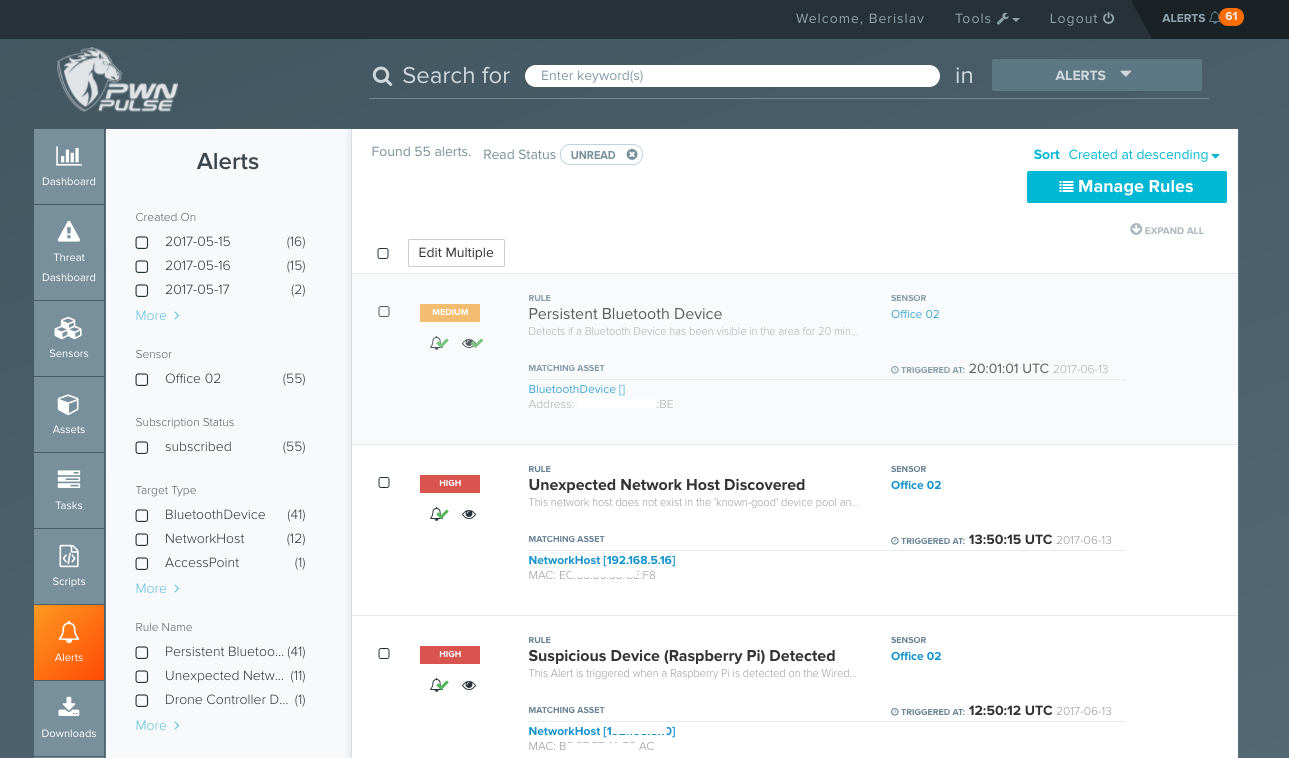
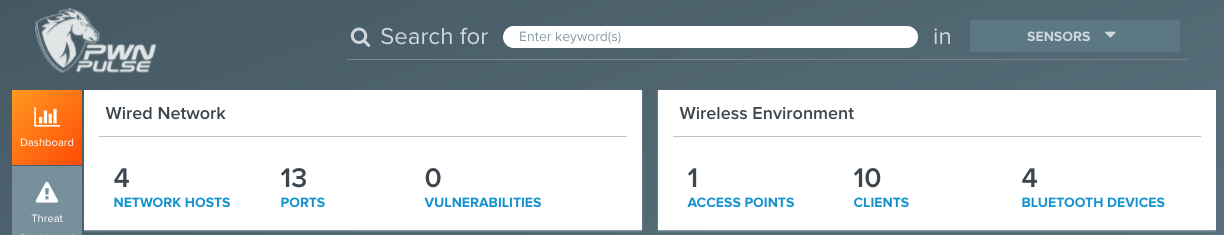
As soon as the sensor is connected to Pulse, all the details regarding the discovered assets start showing up in the web interface. Each sensor can be named accordingly to the branch of your organization it is installed into. The dashboard will show a list of discovered network hosts, ports, vulnerabilities, wireless access points/clients, as well as Bluetooth devices roaming around the sensor.
The user interface is easy to use and provides detailed insight into the network, as well as vulnerabilities and potential threats.
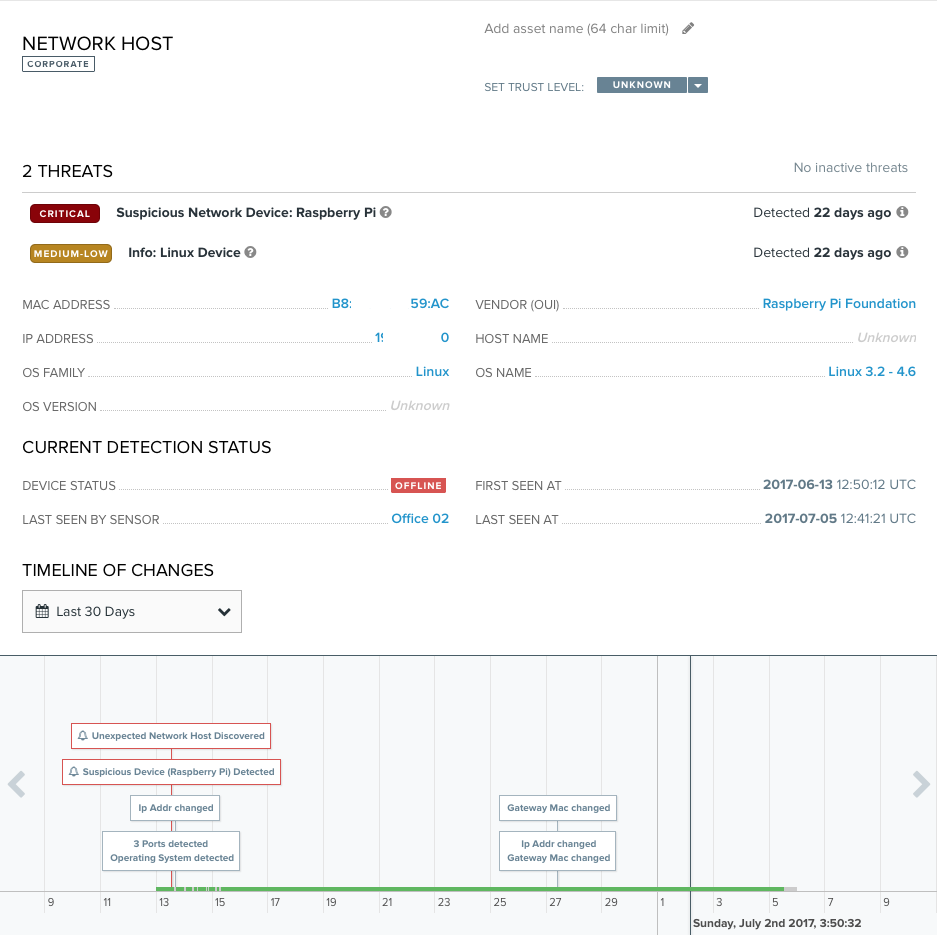
The Assets section of the interface is a good place to start. Depending on the size of your network, it could show quite a long list of every object the scanner came across. As you can see from the screenshot below, there is much information on every discovered network host, as well as wireless and bluetooth clients. Every object has a trust level: “Unknown,” “Known Bad,” “Known Good,” “Suspicious,” or “Acceptable.”
What I like about the trust levels in Pulse is that, by default, the majority of the discovered devices are labeled as suspicious. When you connect a Raspbery Pi or some not-so-typical device to the network, it will be labeled with a lesser trust level. At any time, the administrator can go to Tools > Manage Threat Severity Levels and fully customize the default threats for any asset type or a threat name. There is also the Active Directory Pulse integration feature, which fetches a list of network hosts from the AD and matches it against the list of detected hosts. Devices found on both lists get the “Known Good” trust level applied to them.
Users and roles
The system supports two types of Pulse user accounts – Admin and Tester. Admin has all the permissions, and Tester can view asset data, view reports, export CSV, schedule tasks and manage sensor services. Two factor authentication is enabled for all accounts and users can use the Google Authenticator app to receive the second factor.
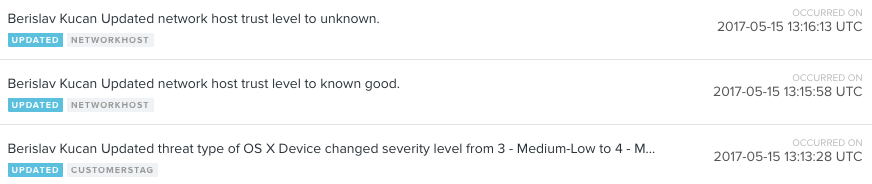
Admin users can access a full audit log, which outlines all the major changes done via the management console.
Scripting
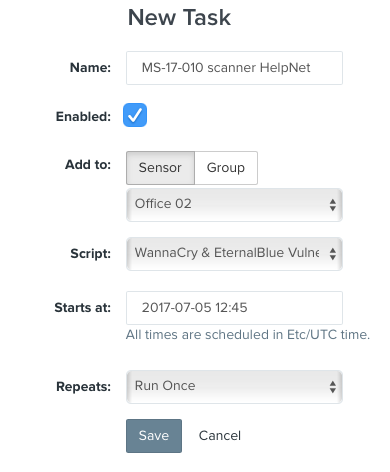
One of the interesting things about Pulse is its ability to run custom scripts. These scripts can be created and used to for various purposes: diagnostics, identification of specific services, customized scans, as well as taking action against new high-risk threats. As MS17-010 was publicly revealed and threat actors started exploiting it heavily, Pwnie Express created a custom script that detected vulnerable hosts and immediately shipped it to its users.
Similarly, here you can see a sample Pulse script-based scanner for identifying hosts vulnerable to the recently unearthed escalation of privilege vulnerability that could allow an unprivileged attacker to gain control of the manageability features provided by various Intel products:
Any script can be used as a part of a newly created task that you can run immediately or schedule for a future date and time.
Device risk scorecard and reporting
The Reports section of the management console features a scorecard (see screenshot below), and by clicking on the colored circle for any day that did not get an A+ grade you can peruse the “headlines” for that day and dig deeper into the threat that caused the drop in ratings.
Aside from the scorecard, the system also generates a daily report with the following table of contents:
- Scope
- Summary of findings
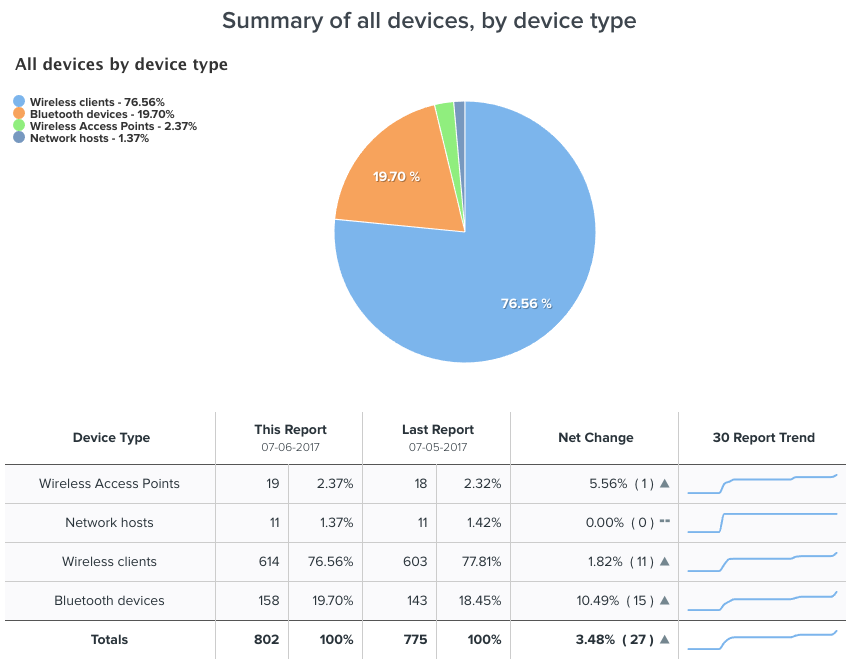
- Summary of all devices, by device type
- Summary of corporate devices, by device type
- Summary of device threats, by severity level
- Critical-severity device threats
- Open default-state Access Points, by SSID
- Summary of open (unencrypted) Access Points, by SSID
- Device threats by severity level
- Wireless/Mobile device statistics
Documentation
Pulse documentation is available online. With every sensor you’ll get a quick installation sheet detailing the actions required for connecting it to the Pulse network. The product user guide is 48 pages long, and is spread into 13 thematical sections dealing with all aspects of service installation and usage. A troubleshooting “one pager” is included at the end of the document. Support is available over email and phone, 9am to 5pm, Monday to Friday.
In my experience, Pwnie Express usually sends a couple of emails per month. These are solely focused on giving the users information on new add-ons for Pulse, as well as providing scripts for some very hot issues (such as the MS17-010 I’ve mentioned earlier).
Pricing
Enterprise pricing for Pulse includes an annual service charge, with a sensor and connection fee per sensor. No up-front hardware purchase is required and buying the service includes full access to updates, helpdesk support and unlimited IP scanning. Sample deployment prices are not disclosed, so check with Pwnie Express for more information.
Final thoughts
Pulse is a versatile solution that is optimized for the ever-rising number of highly distributed organizations. It excells in centralized management of multiple locations, by running continuous network asset discovery, vulnerability assesment and threat intelligence management. It is also important to highlight the capabilities of detecting rogue devices, with a strict focus on taking care of potential BYOD issues.