Qualys CISO on making everything visibile and secure
 In this podcast recorded at Black Hat USA 2017, Mark Butler, CISO at Qualys, talks about his role, streamlining security and compliance solutions, building security into digital transformation initiatives, end-to-end IT security, keeping your teams in sync, and compliance for all your assets.
In this podcast recorded at Black Hat USA 2017, Mark Butler, CISO at Qualys, talks about his role, streamlining security and compliance solutions, building security into digital transformation initiatives, end-to-end IT security, keeping your teams in sync, and compliance for all your assets.

Here’s a transcript of the podcast for your convenience.
Hi, my name is Mark Butler, I’m the Chief Information Security Officer at Qualys, and I want to tell you a little bit about why I’m here and what we’re trying to accomplish at Qualys. The reason I’m here at Qualys is to help with messaging, with the clarity of the messaging, with the consistency of the messaging. Qualys is known for vulnerability scanning, and we’re obviously very effective with that and have been for quite a few years. Starting in 1999, Qualys has been a SaaS provider or a cloud provider of vulnerability scanning services and we’ve done a very good job and excellent job with that at scale. But Qualys also offers a lot of other products and services that not a lot of people are aware of, and not a lot of customers have leveraged yet.
What we want to do is help get the word out from a messaging and a clarity and an understanding standpoint of not only leveraging that foundation of vulnerability management and understanding what people have, where is it in the environment, and what kind of security posture it has, but also how we can move beyond the detection and data analysis standpoint to move toward a response capability as well.
When you look at the Qualys Platform, it’s focused on vulnerability analysis, it’s focused on threat prioritization, it’s focused on policy compliance. We have web application, scanning, and firewall capabilities but we’re also developing new capabilities in the inventory of assets, inventory of software, inventory of certificates, and the ability to take that information into a response function and make sure that the teams that are looking at the data, and looking at the solutions, and looking at the security dashboards can take action based on what they see and they have confidence that they are looking at accurate data.
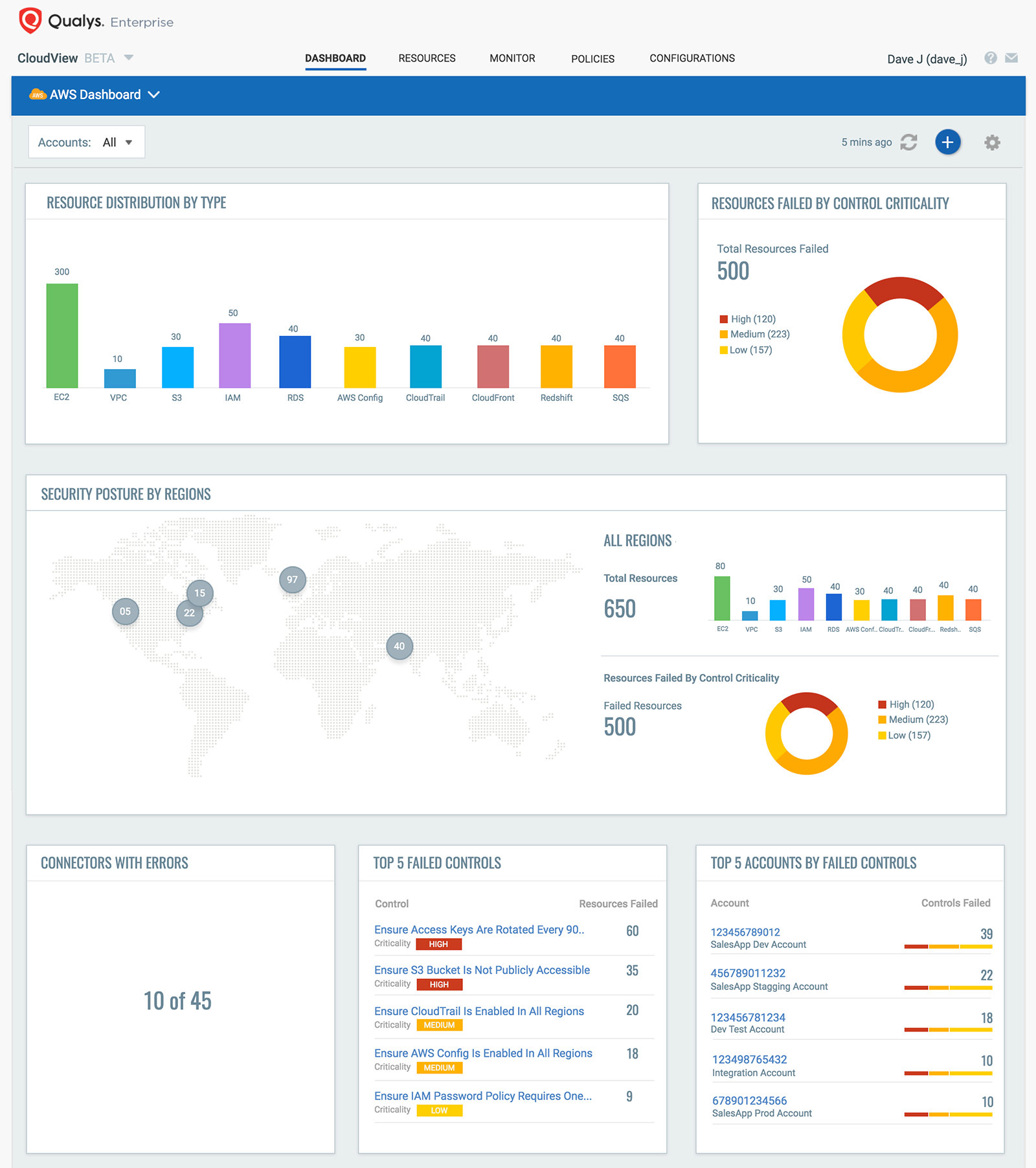
From a platform standpoint, we’re continuing to invest in new capabilities. We just announced CloudView, which is ability to get a security posture view on Azure, Google Cloud, AWS – across containers, as well as instances and workloads within those containers. So, the digital transformation efforts of CIOs and business leaders are mandated with, is really challenging the security teams to figure out, “How do I secure this workload in the cloud?”, “How do I make sure it’s built properly?”, “How do I make sure the data’s protected on it?”, and “How do I do that in a matter of minutes, and hours, and days versus months and years from a traditional technology deployment standpoint?”
The digital transformation effort is a huge paradigm shift. The security teams are coming up to speed slowly on containers, virtual networks, the ability to manage either what we call ephemeral or very short-lived systems, and the DevOps communities are building software differently where they may not run a service on a system for a long period of time. They may only instantiate that service for the period that they need it, and it may shut down after it’s utilized and may spin back up later.
So, the DevOps communities and the DevSecOps efforts are gaining traction, and the ability for the security teams to secure that system, that service, that capability from a product standpoint – however long it lives – is really where we need to go to from a shift where we’ve traditionally looked at static systems, static networks, status, static applications. The dynamic capabilities of the DevOps cycles the instantiation of services as needed and then the tearing down of those services when they’re no longer needed is really a totally different paradigm than most security people have in their minds from how do I build, deploy, implement, and audit systems.
What we’re here to do is regardless of where that workload is, regardless of where that system is, regardless of whether it’s a server running in a data center, whether it’s an endpoint running in a corporate network, whether it’s a cloud container that has a hundred websters in one hour and 500 websters in the next hour – you have the same level of this ability from a security standpoint across those ecosystems. And then you can turn around to your management, you can turn around to your auditing community, and say, “I understand what I have. I understand where it is. I understand the volume varies of system counts and number of systems supporting business products and services. But regardless of how long that system lived, it was in a secure state. And I have confidence that I can tell you that based on how it was built, how it was deployed, even if that deployment is a script within a provisioning process that is entirely automated or there’s no manual processes involved.
What we’re focused on is not only the integration into the containers, integration into the cloud service providers, but making sure that everything that we do is as automated as possible ‘coz we don’t want to introduce opportunity for failure, opportunity for issues, opportunity for misconfigurations. And then if there is some type of inadvertent misconfiguration, we will also get visibility to it based on the agents that get deployed on those virtual systems.
So, we’re focused on visibility, we’re focused on speed and enabling the business, we’re focused on efficiency making sure that we can automate whatever possible. But at the end of the day, it’s understanding your security posture, being able to represent it to others in an accurate and immediate fashion. And then over time, proving that we’re getting better, proving that we’re making the right investments from a security stack in a security solution standpoint, and then also making sure that we’re partnering with the right go-forward vendors to collapse and simplify and make sure that our limited time and resources and money are being spent in the most effective manner possible.
My CISO role is focused on getting input from other CIOs, other CISOs, other business and technology leaders, and security leaders within enterprises of all sizes of where they are headed, what they are thinking about, what are they prioritizing, and how are they going about their rationalizing their security programs, and their security solutions, and their security capabilities, as they get more and more pressure to prove that they’re being effective, they’re doing what they need to protect the business, but they’re also spending in an optimized way and not adding additional layers of complexity or staff or capital investments or run costs, when there’s not a clear benefit to doing that.
That’s why I’m here, that’s what we’re trying to do from a Qualys standpoint, and we will continue to invest in additional visibility tools, additional risk analysis tools, additional response capabilities, helping those security teams that are already overburdened with, “I have too many alerts”, “I have too many dashboards”, and “I have too many places to go to figure out how to respond effectively” and prioritizing all of that in as few places as possible in as few dashboards as possible and ultimately one dashboard and it’s what we’re driving towards. But there’s a lot of layers of data analysis, data prioritization, data sorting, and the ability to provide some context around “Which systems are the most important?”, “Which systems are supporting my critical revenue producing transaction flows, and our business processes, and our services as digital transformation efforts occur.”