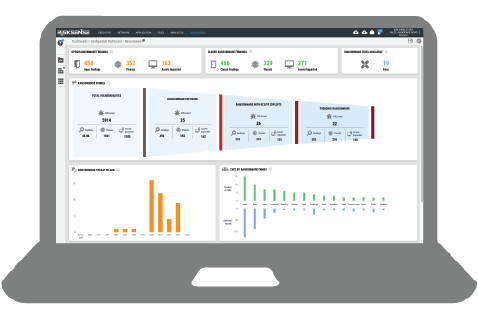
RiskSense Ransomware Dashboard automatically reveals exposure to specific attacks
RiskSense, pioneering risk-based vulnerability management and prioritization, announced a Ransomware Dashboard that automatically reveals an organization’s exposure to specific attacks including the ransomware family name, vulnerabilities they exploit, the assets at risk and remediation steps to prevent an infection.
According to one report, more than 103 state and municipal governments and agencies, 759 healthcare providers and 86 universities, colleges and school districts nationwide were victimized by ransomware in 2019. Meanwhile, two Florida cities, Lake City and Riviera Beach, acknowledged making a combined $1 million in ransom payments to hackers.
“Almost every analysis of a business-damaging ransomware attack points out the criminals exploited well-known vulnerabilities or failures of basic security hygiene” said John Pescatore, Director of Emerging Security Trends at the SANS Institute.
“The government agencies and businesses that have been successful in avoiding or mitigating ransomware impact have the same staffing difficulties as everyone else but have focused on enhancing staff skills for effective security operations and the integration of security tools to act as ‘force multipliers’ to increase efficiency.
“Damage from ransomware and data theft attacks can be minimized by making sure vulnerability and risk status is accurate and current, critical patches are applied as a priority and that critical functions like backup and restore are available and tested.”
To enable organizations to go on the offensive and fix the very vulnerabilities that make ransomware attacks possible, the RiskSense Ransomware Dashboard reveals all assets, including workstations, servers, storage devices and more, at risk from active exploits used by ransomware in the wild.
The analytics-driven RiskSense platform funnels vulnerabilities used by ransomware based on risk factors including the presence of dangerous remote code execution (RCE) and privilege escalation (PE) capabilities, as well as vulnerabilities that are “trending” to narrow and identify which should be prioritized for immediate remediation.
Trending as defined by RiskSense, are vulnerabilities that are being actively exploited by attackers in the wild based on the analysis of 3rd party threat intelligence and vulnerability data sources, changes in exploit state, activity in hacker forums, and social media feeds.
With a single click a project can be created from RiskSense Ransomware Dashboard data to plan, track and verify that remediation actions have been performed and successfully eliminated exposures on at risk assets.
In addition, the RiskSense Ransomware Dashboard enables business and technology executives to easily and consistently provide evidence on what is being done to identify and mitigate the threat of ransomware to the organization through automated and configurable reporting.
“In most cases, lack of IT resources and visibility make organizations vulnerable to ransomware attacks. For example, over two-thirds of U.S. state entities, critical infrastructure and managed service providers have suffered a ransomware attack in the past 18 months,” said Dr. Srinivas Mukkamala, CEO of RiskSense.
“The RiskSense Ransomware Dashboard eliminates the manual work associated with identifying assets that are vulnerable to ransomware and at imminent risk. We also offer ransomware-specific validation services that make it possible for any size IT department to immunize their organizations from ransomware.”