Meetup vulnerabilities enabled group takeovers, payment redirections
Two high-risk vulnerabilities in Meetup, a popular online service that’s used to create groups that host local in-person events, allowed attackers to easily take over any Meetup group, access all group functions and assets, and redirect all Meetup payments/financial transactions to their PayPal account (some Meetup events are free, but some are not).
What’s more, attackers could create a worm to take over all meetings on the site – including private ones – and do all of these things.
About the Meetup vulnerabilities
Checkmarx researchers, who were searching for API security issues in high-profile web applications, discovered two privacy-busting API flaws on Meetup.com, but also unearthed:
- A stored XSS affecting Meetup Discussion (and discussion capabilities are enabled by default in all Meetups)
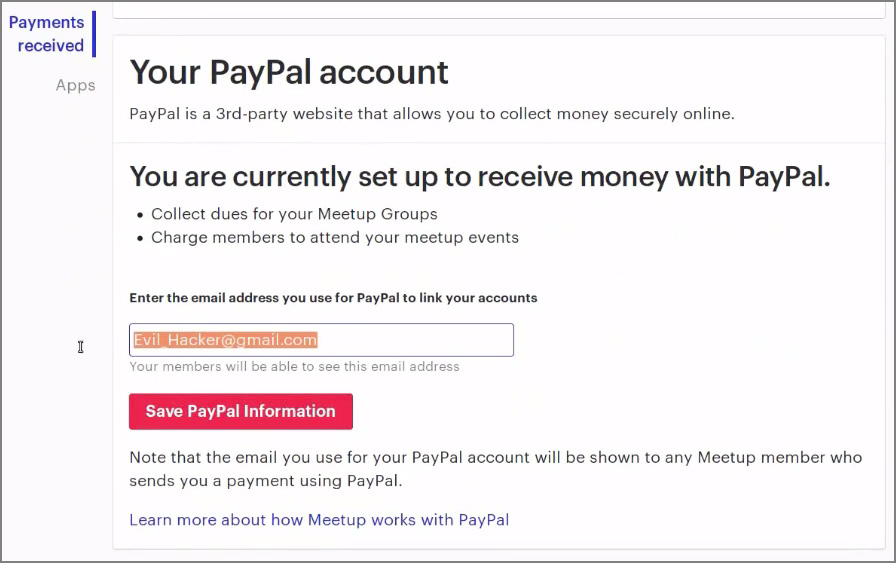
- A CSRF bug in the form used to change the PayPal recipient’s email address in Settings > Payments received.
Both can be exploited by sending a request that includes a malicious JavaScript to the Meetup API, and in both cases the script will not show in the discussion (i.e., the attacker’s reply in the discussion will show up empty.)
By chaining the the XSS and CSRF vulnerabilities together, an attacker could steal the organizer’s cookie and use it to change their status to co-organizer of the Meetup group, meaning they can access members’ details, contact all members, edit group settings, create events, and so on:

The attacker could also forge a request to change the PayPal account email address stored in Meetup -> Manage Money, effectively directing all payments to the attacker’s address.
The original organizer could, of course, notice they change if they check the setting, but it could also go unnoticed for hours or days, as they would not receive a notification of it.
Here’s a demo of the attacks:
The good news
Meetup has been appraised of the findings and has fixed all the flaws discovered by Checkmarx researchers, including the two flaws that could allow attackers to enumerate Meetup users and retrieve sensitive information about them.
They did not mention, though, whether they spotted attackers exploiting those flaws before the fixes were implemented.