Thousands of QNAP NAS devices hit by DeadBolt ransomware (CVE-2022-27593)
QNAP Systems has provided more information about the latest DeadBolt ransomware campaign targeting users of its network-attached storage (NAS) devices and the vulnerability the attackers are exploiting (CVE-2022-27593).
About CVE-2022-27593
CVE-2022-27593 exists because of an externally controlled reference that resolves to a resource that is outside of the intended control sphere, and affects the widely used Photo Station application.
The vulnerability allows attackers to modify system files and, ultimately, install and deploy ransomware.
According to its entry in the National Vulnerability Database, the flaw can be exploited by remote, unauthenticated attackers without any user interaction. Also, the attack complexity is low.
Security researcher Jacob Baines published an entry on the AttackerKB database/public forum, detailing their analysis of the Photo Station patch provided by QNAP and giving insight in some of the particularities of CVE-2022-27593.
“No public exploit code exists, although this write up will introduce, what we believe to be, the basis of the exploit,” he wrote, and noted that the published information is likely enough to write signatures and detections against its exploitation.
QNAP’s advice
As QNAP tells it, their Product Security Incident Response Team (PSIRT) received the first reports about the attacks on September 3, 2022. The company released a patch on the same day and published the security advisory urging users to implement the patch and take defensive actions.
“QNAP’s security team determined that the source of the DeadBolt malware attack is via The Onion Routing (Tor), an anonymous connection,” the company shared.
“QNAP has collected a list of malicious hosts and preloaded the blacklist to the QuFirewall application. QuFirewall will block suspicious packets that are suspected to be sent by onion routing to prevent NAS hosts from being attacked. It detects onion routing and malicious bots every day, and dynamically updates the blocking list of malicious packets. Since most malware is routed through anonymous onions routing to avoid being traced, QNAP urges all QNAP NAS users to install QuFirewall immediately to work with us to block malware attacks.”
QNAP also said that:
- By them pushing out cloud-based malware definition updates based on the identified attack patterns, NAS devices were protected from the ransomware threat without users having to install the patched app, and
- Automatic installation of app updates via the QTS App Center helped protect some internet-connected QNAP NAS devices from attack.
The company has urged users to take advantage of the Snapshots feature to prevent future ransomware campaigns to end up badly for them.
“QNAP amended NAS snapshots in 2021, preventing snapshots from being deleted by ransomware. In QTS 5.0.0, snapshots are enabled by default in Thin/Thick Volume. Users who create snapshots regularly can restore full NAS data to a specific point of time using snapshots,” they explained.
A spike in DeadBolt infections
The company did not say how many devices ended up being affected in this latest DeadBolt campaign, but Censys detected a dramatic jump in infections in early September:
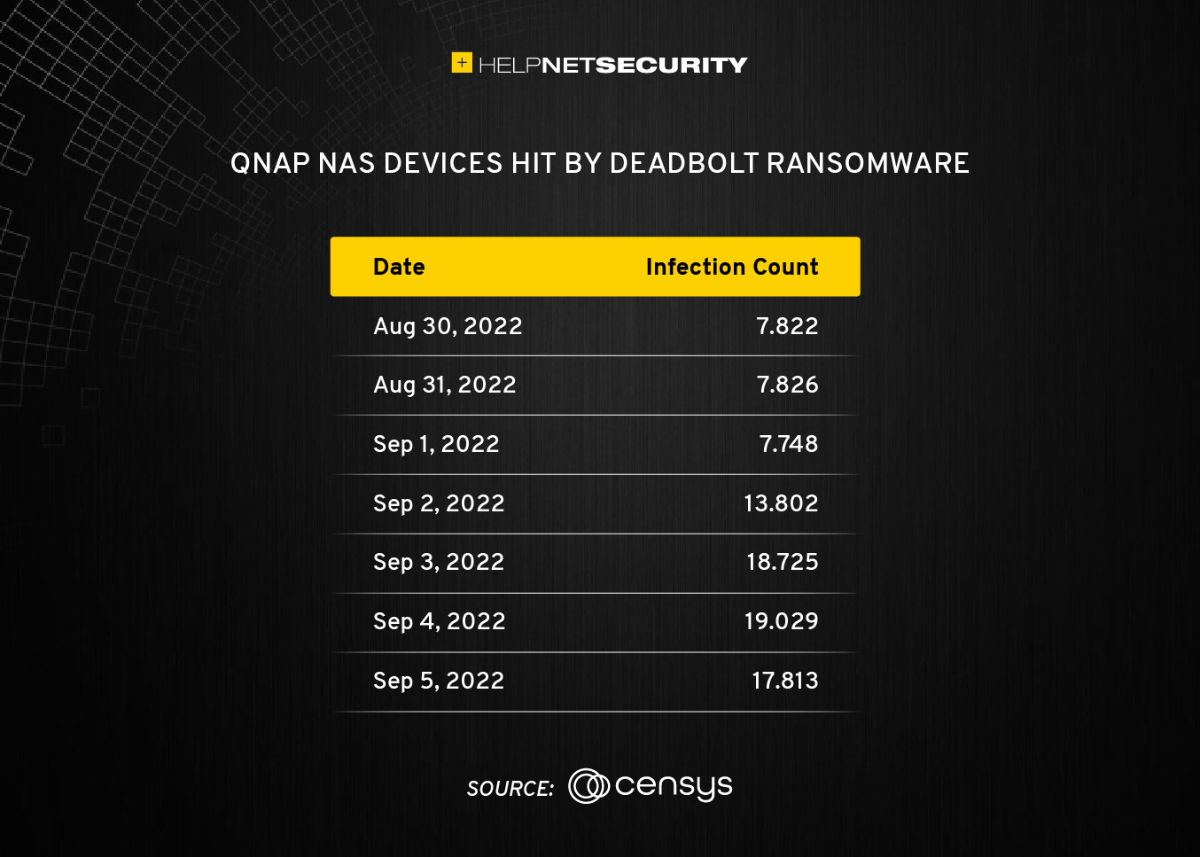
“Deadbolt seems to have a relatively common cadence of new infections. On average, there seem to be seven to twelve days between each campain,” Censys senior security researcher Mark Ellzey explained.
“Instead of encrypting the entire device, which effectively takes the device offline (and out of the purview of Censys), the ransomware only targets specific backup directories for encryption and vandalizes the web administration interface with an informational message explaining how to remove the infection.”