Russian hacktivists hit Ukrainian orgs with ransomware – but no ransom demands
The Ukrainian CERT (CERT-UA) has uncovered an attack campaign aimed at compromising Ukrainian organizations and irretrievably encrypting their files. To do that, they are leveraging a specific version of the Somnia ransomware that, “according to the attackers’ theoretical plan, does not provide for the possibility of data decryption.”
How the attacks unfolded
The Ukrainian cyber experts believe that the attack was effected by Russian hacktivists that go by FRwL (From Russia with Love), with help from an initial access broker (IAB).
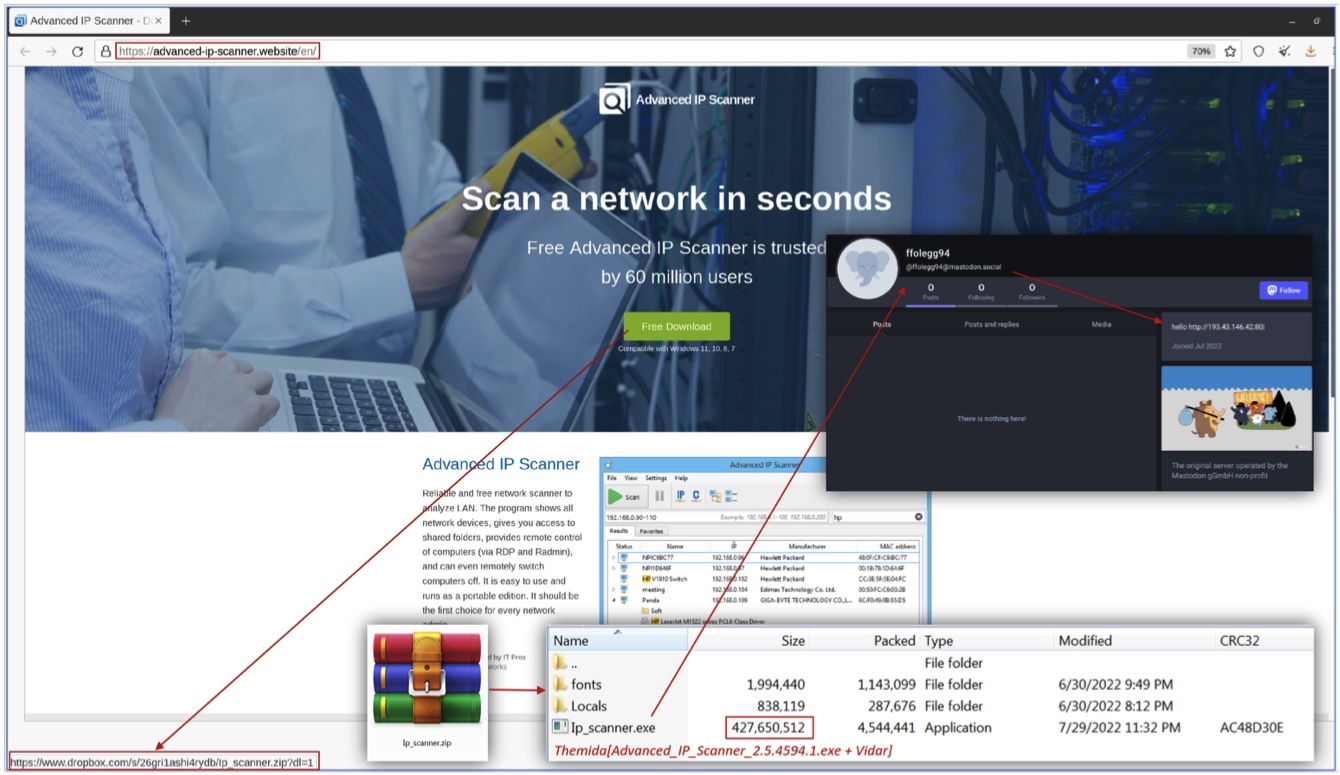
The IAB spoofed the website of Famatech’s Advanced IP Scanner software and pointed the “Free Download” button to a Dropbox account hosting what looks like the scanner but is actually the Vidar infostealer.
Once installed, the infostealer connects to a predefined Mastodon user to get its configuration file (a long-standing tactic, it seems).
“It should be noted that the Vidar stealer, among other things, steals Telegram session data, which, in the absence of configured two-factor authentication and a passcode, allows unauthorized access to the victim’s account,” CERT-UA explained.
“As it turned out, the victim’s Telegram was used to transfer VPN connection configuration files (including certificates and authentication data) to users. Given the lack of two-factor authentication when establishing a VPN connection, attackers were able to gain an unauthorized connection to the corporate network.”
The team does not specify at which point the hacktivists took the attack over from the IAB, but say that, “Having gained remote access to the organization’s computer network using a VPN, the attackers conducted reconnaissance (in particular, used Netscan), launched the Cobalt Strike Beacon program, and also exfiltrated data, as evidenced by the use of the Rсlone program.”
They also used the Anydesk remote access software and the Ngrok reverse proxy.
Hacktivist continue to wage war
“FRwL (aka Z-Team), whose activity is monitored by CERT-UA under the identifier UAC-0118, took responsibility for the unauthorized intervention in the operation of automated systems and electronic computing machines of the target of the attack,” the Ukrainians say.
FRwL have been launching similar attacks against Ukrainian targets since the spring of 2022, but this time the ransomware used is different, as it uses a different algorithm (AES instead of 3DES) to encrypt files with a variety of extensions.
And, as mentioned before, this time they are apparently doing it not to “earn” money, but to disrupt the work at the target organizations.
More information and IoCs related to the attach campaing can be accessed here .