REMnux v8 brings AI integration to the Linux malware analysis toolkit
REMnux, a specialized Linux distribution for malware analysis, has released version 8 with a rebuilt platform based on Ubuntu 24.04 and a new capability aimed at connecting AI agents directly to its toolset.
REMnux is designed for analyzing malicious software, phishing artifacts, suspicious documents, and related forensic data. The project includes more than 200 preconfigured tools commonly used in malware analysis workflows.
The REMnux v8 release arrived as Ubuntu 20.04 approached end-of-life, creating a deadline for projects built on that base. According to REMnux creator Lenny Zeltser, the update required a deeper overhaul than a typical refresh.
“The biggest challenge of releasing v8 was finding the time,” Zeltser told Help Net Security. “REMnux isn’t a commercial project, so work priorities and other commitments always compete. But Ubuntu 20.04 reaching end-of-life forced a ground-up rebuild, not just an incremental update. That external pressure, combined with the energy of my collaborator Corey Forman, who has contributed behind the scenes for many years, pushed the release forward,” he said.
New installer supports upgrades and deployment flexibility
REMnux v8 includes a new Cast-based installer, replacing the previous installation approach. The installer supports initial deployments, upgrades, and installing REMnux tools on an existing Ubuntu system.
The project continues to support multiple deployment methods, including virtual machine images and container-based use of specific utilities.
REMnux MCP server connects AI agents to analysis tools
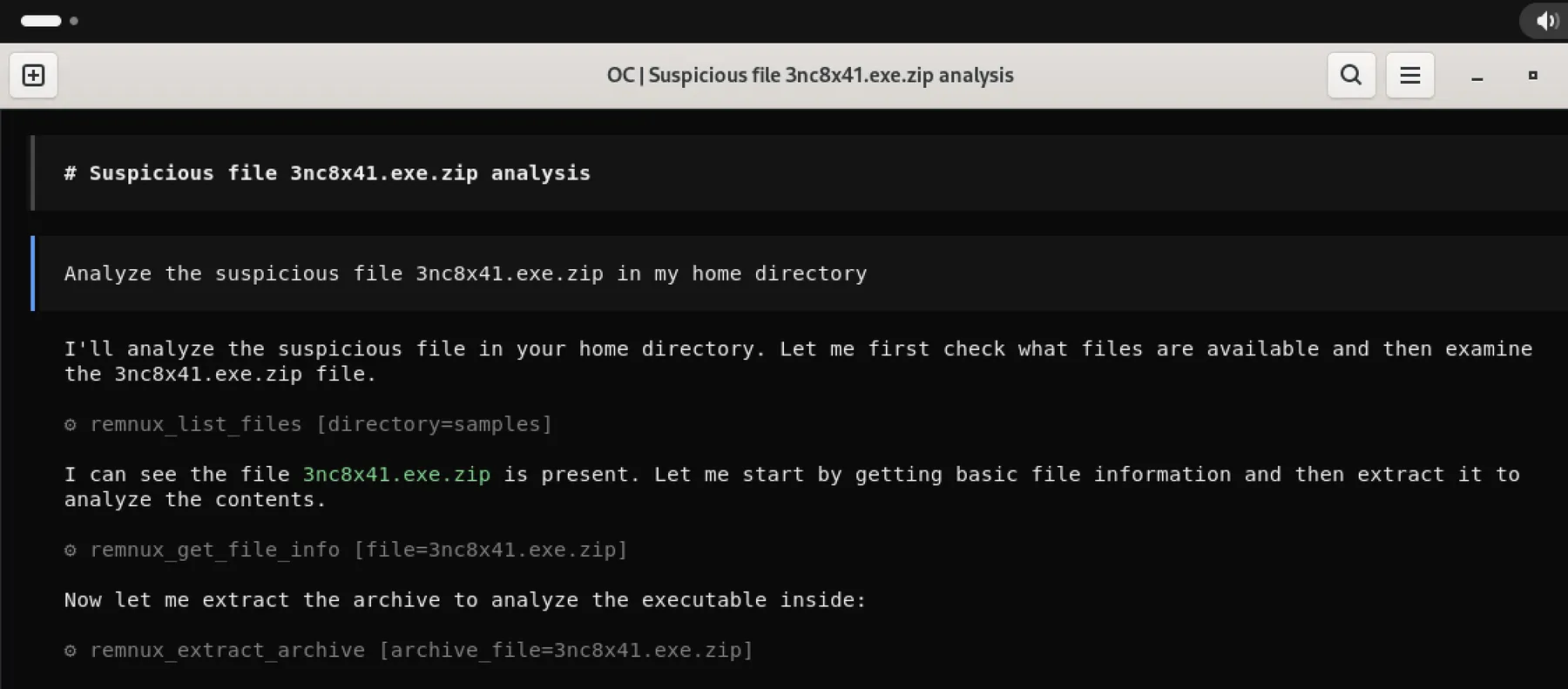
One of the largest additions in version 8 is the REMnux MCP server, which implements the Model Context Protocol (MCP) to connect AI agents to REMnux tools.
“A major new capability is the REMnux MCP server, which connects AI agents to the toolkit’s 200+ tools with practitioner knowledge built in,” Zeltser said. “It knows which tools apply to each file type, how to invoke them, and how to interpret their output.”
Zeltser said the MCP server was designed to compensate for common weaknesses in general-purpose AI systems used in technical investigations.
“It also counteracts AI confirmation bias: when a tool flags something like GetProcAddress, the server reminds the AI that this API import appears in most Windows programs, not just malware,” he said.
“The hardest design challenge was providing enough guidance for the AI to use REMnux tools effectively while leaving it free to think creatively about the analysis,” Zeltser said.
AI workflows built around practitioner knowledge
The release expands REMnux documentation and tooling around AI-assisted workflows, including integrations with reverse engineering environments and command-line AI assistants. The goal is to allow analysts to pair human decision-making with automated execution and interpretation of tool output.
Zeltser described the approach as a structured workflow that divides responsibilities between the analyst, the AI system, and REMnux itself.
“The result is a four-part workflow: the analyst provides judgment, the AI agent executes and interprets, the MCP server supplies domain expertise, and REMnux provides the analysis environment,” he said.
Tool updates and continued focus on malware analysis
REMnux v8 refreshes many existing utilities and adds new tools for file format analysis and malware unpacking workflows. The release also incorporates YARA-X, a Rust-based implementation of YARA, along with additional supporting utilities and updated tool packaging.
“REMnux is unique in its longevity as a Linux toolkit focused specifically on malware analysis: 15 years and eight major releases,” he said. “Its command-line tools make it inherently AI-friendly. The MCP serve adds the practitioner knowledge that generic AI models lack.”
REMnux v8 is available for free here.

Must read:
- 40 open-source tools redefining how security teams secure the stack
- Firmware scanning time, cost, and where teams run EMBA

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
