PHP, Python still fail to spot revoked TLS certificates
In 2012, a group of researchers demonstrated that SSL certificate validation is broken in many applications and libraries, and pointed out the root causes for that situation: badly designed APIs of SSL implementations and data-transport libraries.
Four years later, Sucuri Security researchers wanted to check what’s the current situation, and discovered that there have been some improvements, but that PHP, Python and Google Go still fail to check if a TLS certificate has been revoked.
Why is that important?
“Web developers today rely on various third-party APIs. For example, these APIs allow you to accept credit card payments, integrate a social network with your website, or clear your CDN’s cache. The HTTPS protocol is used to secure the connection with the API server. However, if your web app doesn’t verify the TLS certificate, a malicious person can steal your passwords or your customers’ credit card numbers,” Sucuri researcher Peter Kankowski explained.
“If you don’t verify the certificate, the attacker can masquerade as the API server, intercept data sent in both directions, or even return false messages that the API server never sent to you.”
Sucuri’s testing revealed the following results for the various versions of the languages used to program APIs:
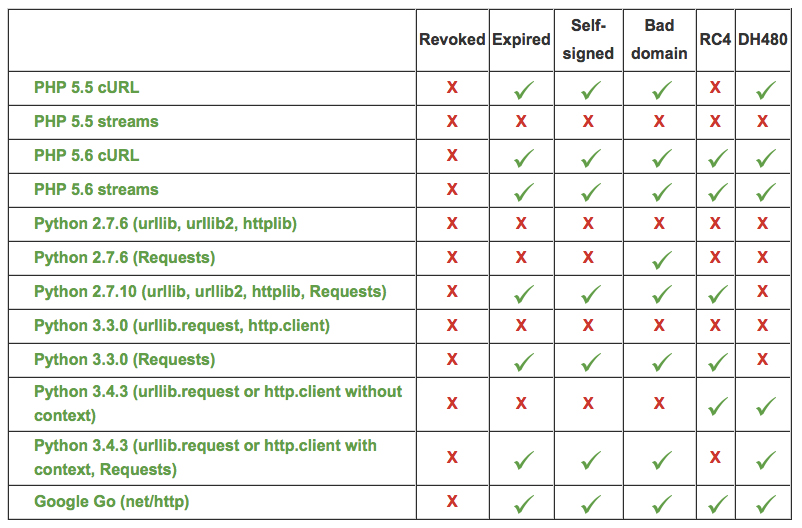
What can you do about it?
“TLS implementation in PHP 5.5 and below is broken when you use stream functions (fsockopen, fopen, stream_socket_client, stream_socket_enable_crypto, or file_get_contents). You should use cURL functions instead and upgrade to PHP 5.6 whenever possible,” Kankowski advised.
“For Python, the situation is even more complicated and badly documented. The best solution is upgrading to the versions 3.4.3 and 2.7.9 or higher and always using the context parameter.”
More details about the recommended TLS configuration for the various language version can be found in the blog post, but when it comes to certificate revocation checks, there isn’t much one can do, he says.
“Writing your own revocation check code is hardly realistic; you would need a skilled cryptographer for this task. PHP has the CURLOPT_CRLFILE option, but you would have to download the CRL file and verify its signature yourself. OCSP stapling is not supported in PHP. Google Go only returns a raw stapled OCSP response in Response.TLS.OCSPResponse. A lot of work would be needed to build a revocation check function from these primitives.”