Malicious Chrome update actively targeting Android users
A fake malicious Chrome update is being actively pushed onto Android users, saddling them with information-stealing malware that can be uninstalled only by restoring the device to factory settings – and losing data in the process.
The malicious file – Update_chrome.apk – is hosted on a continually changing list of pages whose URLs sport variations on expressions like “Google”, “Google apps”, “Google market”, “Android update”.
Once victims are tricked into downloading and installing the fake update, the malware asks for administrative access to the device. When that access is granted, it:
- Checks for installed security applications and terminates them
- Registers the device with the C&C server
- Monitors SMS and call operations, collects SMSes and call logs and sends them to the C&C server
- Shows a fake payment page for harvesting payment card details each time the user tries to access the Google Play store (via the dedicated app), and send the collected info directly to a Russian phone number.
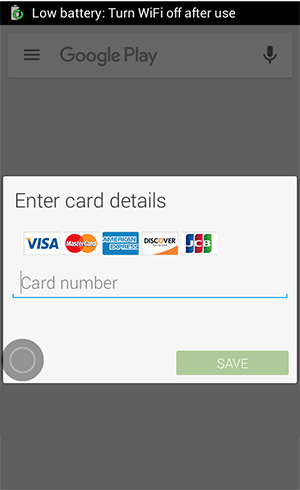
“Once installed, this infostealer cannot be removed from the phone as the malware does not allow the user to deactivate it’s administrative access. The only option to remove this malware is a factory reset which leads to further data loss,” Zscaler researchers have discovered.
Regularly backing up the content of their mobile devices will help users prevent such data loss (and also comes handy when they get infected with ransomware), but being extra careful when downloading updates is also a good idea.