Android banking malware may start using adware tricks
Android banking and credential-stealing malware with screen overlay capabilities is on the rise, but for it to be effective, it must detect when banking, email, social media apps are opened, identify them, and show the appropriate pop up intended to harvest sensitive data.
That’s not a problem when the malware is installed on Android versions before 5.0 (Lollipop) – according to Google’s numbers, that’s nearly 57 percent of all Android devices out there – because the malware invokes the “getRunningTasks()” API to discover that information.
But with Lollipop, unveiled in June 2014, the getRunningTasks() API is no longer available to third-party apps (and in general returns a small part of the data it originally did). This is why the Bankosy banking Trojan has suffered a drop in effectiveness.
“From Lollipop onwards, attackers began using an undocumented variable to determine what app was running in the foreground,” Symantec researchers noted, but pointed out that Google eventually blocked it from working in Android 5.0 and later. “These methods no longer work on the recent Android versions, which account for about 40 percent of Android devices.”
The researchers believe that authors of these types of Android malware might soon turn to another trick for detecting and identifying running apps.
The trick, already used by Android adware and potentially unwanted apps (PUAs), takes advantage of the Android’s accessibility service.
“Android’s accessibility service is meant to help users with physical, visual, or age-related limitations use their device,” the researchers explain. “Some accessibility service features include text-to-speech, haptic feedback, and gesture navigation. Audio-based accessibility features need to know what app is currently running in the foreground so that it can tell a visually impaired user about it through the device’s speakers.”
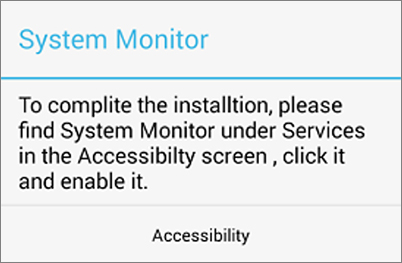
In order to exploit this capability to their advantage, adware authors need to prompt users to turn on the accessibility service when the appropriate pop up is shown by the adware, and then do the same in their device settings.
Compared to the exploitation of the getRunningTasks() API, the misuse of Android’s accessibility service is less convenient, as it requires user interaction.
It is expected that this approach is also less successful, and malware authors still prefer using getRunningTasks(). But, as the number of devices with Android versions 5.0 and later slowly rises, and especially in richer countries whose citizens are preferred victims of cyber crooks that are after banking info, they will have to switch to the newer trick – or find a new, better one.