Innovative techniques allow malvertising campaigns to run for years
A threat actor dubbed AdGholas has been mounting successful malvertising campaigns by using innovative targeting and obfuscation techniques, and has been infecting thousands of victims every day since 2015 – and possibly even earlier.
The discovery of the massive malvertising network was made by Proofpoint researchers, and Trend Micro’s researchers helped with some aspects. Their efforts, along with those of advertising network operators, resulted in the suspension of all AdGholas campaigns on July 20, 2016. Whether AdGholas has been stymied for good or only temporarily, only time will tell.
AdGholas malvertising campaigns: Stealthy and successful
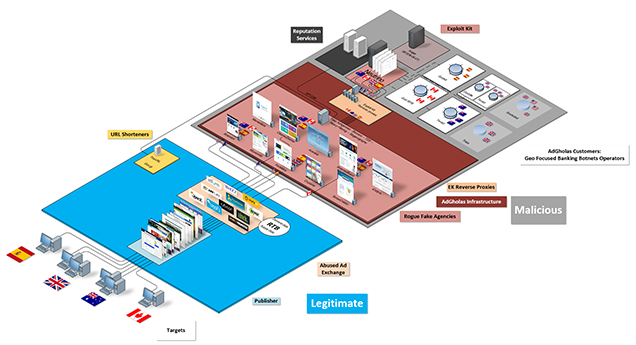
The AdGholas threat actor managed to deliver malicious ads to visitors of over a hundred high profile websites – the NYT, the Daily Mail, Ars Technica, MSN.com, CBS Sports, DailyMotion, ViaMichelin, and so on – through 22 ad platforms.
The researchers estimate that as many as 1 million users were successfully redirected to sites hosting an exploit kit (first Angler, then Neutrino), and thousands of them were infected each day with malware.
Such a success of the campaigns is partly down to the sheer size of the malvertising network, and partly to the threat actor’s efforts to target the right users with the right malware.
Also, not all users were ultimately targeted. Their machines had to have specific combinations of language settings, time zone, browser configuration, files and installed software to be redirected towards the exploit kit.
For example, machines that had software like GeoEdge, Geosurf, AdClarity ToolBar and certain drivers installed on them were targeted, as well as those that hosted certain logo files in their hard drives. It seems that the threat actor intentionally targeted “branded” (OEM) computers and their “average users” who likely don’t known much about computer security in general.

After more than the usual amount of time setting up virtual machines that would trigger all steps of the attack chain, the researchers also saw that some banners were “different.” Trend Micro researchers discovered why: the ads contained malicious JavaScripts and additional hidden data with the help of steganography.
Then, different malware was delivered to different users. “Before AdGholas suspended operation, we witnessed geo-focused banking Trojans being dropped on the compromised computers upon successful infection. For example, Gozi ISFB was dropped in Canada, Terdot.A (aka DELoader) in Australia, Godzilla loaded Terdot. A in Great Britain, and Gootkit was dropped in Spain,” Proofpoint researchers shared.
And finally, the malvertisers used very convincing redirect sites, that closely mimicked legitimate ones and did not trigger suspicion with the ad agencies.