Cyber threat analysis in complex adaptive systems
 The use of wartime analogies in cybersecurity is common in our industry. Sun Tzu is often quoted in presentations and papers to emphasize an author’s key point. I will spare you that in this article; however, I would like to introduce the idea of applying a rigorous framework derived from kinetic warfare to the cyber realm. The notion of complex adaptive systems (CAS) as introduced by Brigadier General Wayne Michael Hall and Dr. Gary Citrenbaum in their book on intelligence collection provides such a framework.
The use of wartime analogies in cybersecurity is common in our industry. Sun Tzu is often quoted in presentations and papers to emphasize an author’s key point. I will spare you that in this article; however, I would like to introduce the idea of applying a rigorous framework derived from kinetic warfare to the cyber realm. The notion of complex adaptive systems (CAS) as introduced by Brigadier General Wayne Michael Hall and Dr. Gary Citrenbaum in their book on intelligence collection provides such a framework.
The CAS is a constantly changing, self-revising, feedback-incorporating concept that is typical in modern urban warfare. Troops engaged in battles in this context must simultaneously collect and process information, then develop intelligence on the social, economic, political, geographic, and adversarial conditions. Hall and Citrenbaum argue that the norm in modern warfare is irregular warfare, where adversaries are unevenly matched and chaos, subterfuge, and obfuscation are the key modus operandi of small bands of fighting units pitted against more formal hierarchical military structures.
The cybersecurity industry’s notion of an advanced persistent threat (APT) also incorporates a concept that accounts for many of the constantly morphing conditions of CAS and, at the same time, the tactical nature of irregular warfare. In the APT context, the changing nature of malware and its malicious delivery infrastructure was illustrated a 2011 F-Secure white paper, a 2017 Dragos paper on threats to the electric grid, and many other APT reports.
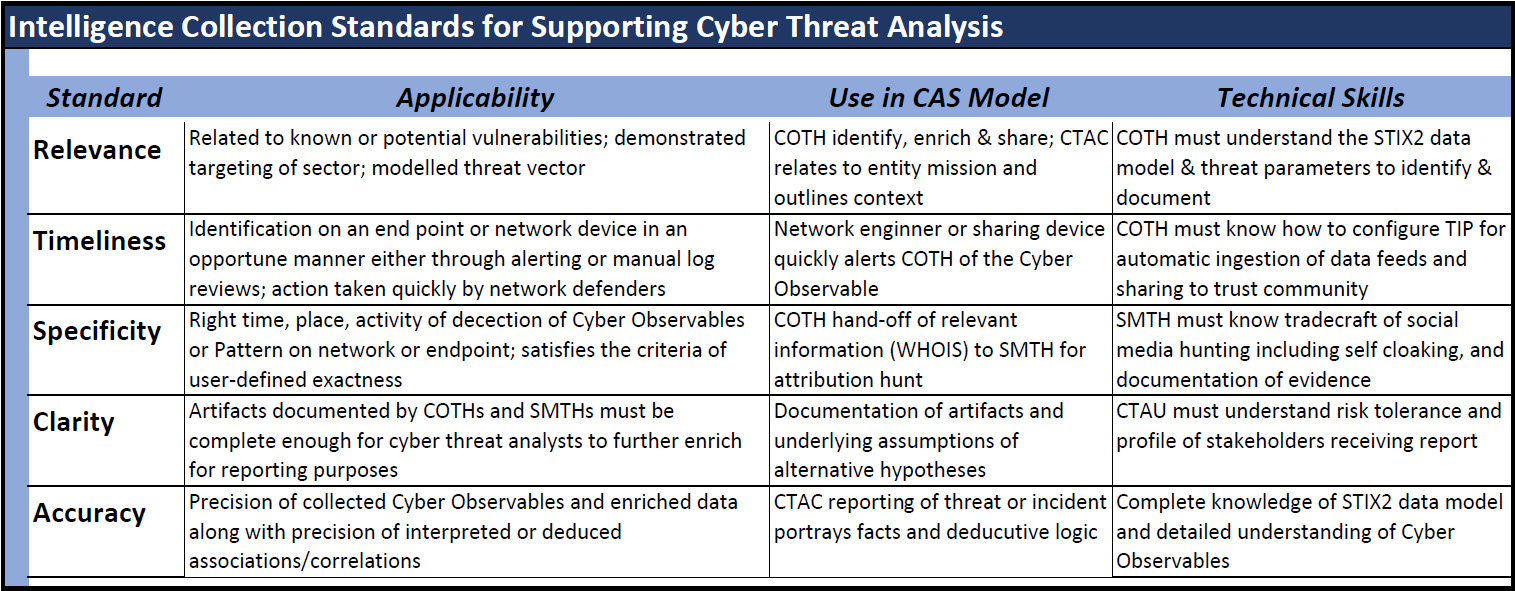
In the context of an operational cyber threat analysis cell (CTAC), as defined in 2014 by Zimmerman, a blending of skills and capabilities between traditional HUMINT intelligence collection practices (while incorporating social media threat hunting) could be one key unit of a CTAC. Another could be a unit for cyber observable (CO) threat hunting; the intelligence collection process that typically uses a threat intelligence platform (TIP) for feed aggregation and data enrichment. I have characterized these three separate units as SMTH, COTH, and CTAC respectively, as shown below.

Simplified diagram of a cyber threat analysis cell for complex adaptive systems
I am proposing that a stable and advanced cyber threat analysis methodology must be based on the reciprocal nature of these two hunting units and that their real-time support of higher-level analysts that synthesize the social media and CO data (along with the other situational awareness information) can help the analyst(s) put the threat into context for decision-makers and risk analysts.
Now, I’d like to take this concept a step further; that is, show how the use of the newly published protocols from the international standards body for structured information systems supports the build-out of a rigorous theory for cyber threat analysis within CAS and subsequently supports the emerging ecosystem for threat intelligence sharing.
The Cyber Threat Intelligence Technical Committee (CTI TC) of the Organization for the Advancement of Structured Information Systems (OASIS) has recently published the revised 2.0 versions of the Structured Threat Information Expression (STIX) and the Trusted Automated Exchange for Indicator Information (TAXII). These standards, written in JSON, are backward breaking from earlier versions of STIX; and for good reason. The experience of the global community in implementing earlier versions has been brought to bear on refining these standards in a way that will meet performance requirements for big data, cloud-based services, and trust-based sharing communities. The JSON-based serialization is more lightweight, preferred by more developers, and easier to understand, while being sufficient to express the semantics of STIX 2.x.
My assertion in this article is that the STIX 2.x data model, as it is evolving, provides a stable framework for an organizational infrastructure such as a CTAC. It incorporates and extends the original CybOX framework (now known as COs within STIX 2.x, defined above), streamlines and syncs with the important open source community known as MISP, incorporates commonly accepted frameworks such as the intrusion kill chain, and can easily express parameters reflecting the five standards of intelligence collection as outlined by Hall and Citrenbaum, as given below.
I further assert that this proposed theory for standardizing CTACs provides a framework that can be used for organizing the workforce enhancement and training needs for skills upgrades to match the conditions of irregular warfare within a CAS.
In the post-Shadow Brokers world the rules of engagement in cyberspace have changed. The powerful surveillance and reconnaissance tools that were once used by nation-state espionage teams are now in the hands of thieves, criminals, corporate espionage crews, and hostile country military crews.
We all see it; there is a significant up-tick in cyber-criminal and state-sponsored activity. This constitutes a CAS that irregular warfare CTACs, even in the private sector or within managed security services providers (MSSPs) serving that market, must be prepared for. The targets are the civil society institutions that nurture and maintain the economy, freedom and vitality of Western traditions. The hacking tools are being weaponized to take ultimate advantage of the companies and organizations that sustain modern society.
A stable theoretical framework like the CAS that has the intellectual and experiential buy-in from a wide swath of the cybersecurity community and is built on the protocols and rigor that STIX 2.x offers can provide an institutional and organizational defense tactic to counter the threats that are evolving from the Shadow Brokers public releases.