Security researchers sinkholed EITest infection chain
Security researchers have managed to neutralize “EITest,” one of the oldest infection chains and thus preventing as many as two million potential malicious redirects a day.
About EITest
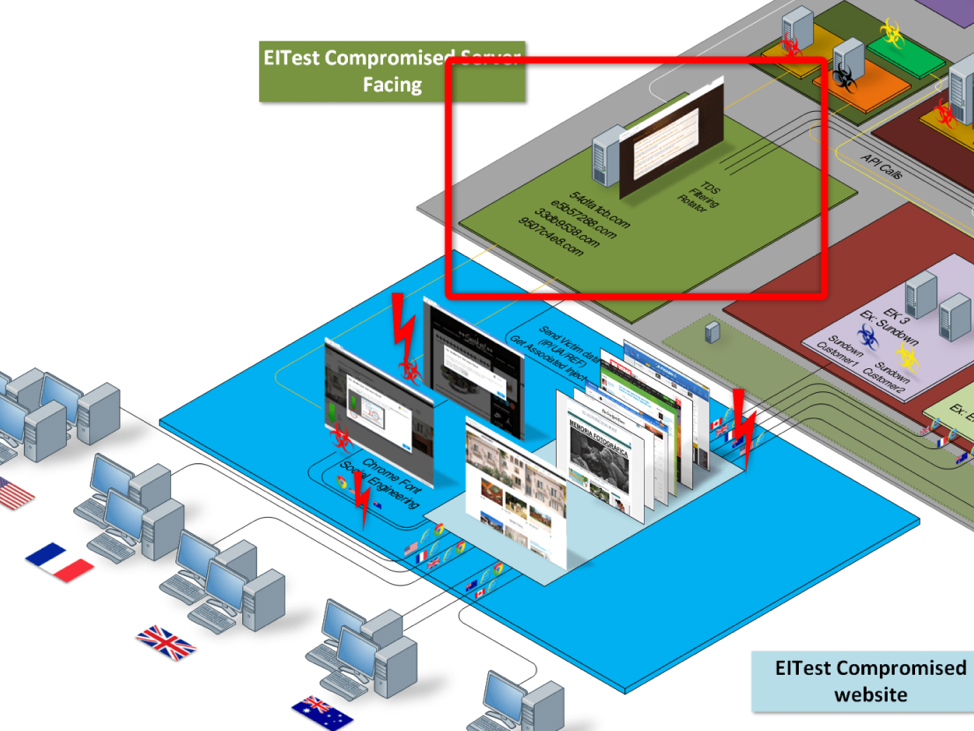
EITest relied on compromised websites – mostly WordPress-based, but also using other CMSes – to direct users to exploit kit landing pages and social engineering schemes, which then delivered a wide variety of malware.
It has been in use, on and off, since at least 2011.
“Shortly after EITest started to use social engineering schemes, researchers traced the chain via server side artifacts and some historical analysis of server side compromises to infections as early as 2011 when it was redirecting to a private EK known as Glazunov. The infection chain appears to have paused between the end of 2013 and the beginning of July 2014, when it began directing into Angler,” Proofpoint researcher Kafeine explained.
In July 2014, the chain reappeared with a new infection pattern spreading multiple payloads, and Kafeine says that the actor behind EITest was likely selling traffic to other actors, a load seller, or both.
“In 2014, we found that the actor was selling traffic in blocks of 50-70,000 visitors for US$20 per thousand, generating between $1,000 and $1,400 per block of traffic,” he noted.
Lately, though, EITest lead mostly to social engineering schemes and tech support scams.
EITest infection chain sinkholed
The operation that lead to the sinkholing of the chain has been mounted by Proofpoint, a Canadian researcher that goes by @Secu0133 on Twitter, and Swiss security activist Raymond Hussy, who’s behind the threat intelligence service Abuse.ch.
In March 2018, they took advantage of a failure in resolution of stat-dns.com, which was used to generate the EITest C&C domains, and took it over.
“Once seized, we pointed that domain to a new IP address to generate four new EITest C&C domains. These, in turn, were pointed to an abuse.ch sinkhole. As a result of generating those new domains, we were able to substitute the malicious server with a sinkhole. We are now receiving the traffic from the backdoors on the compromised websites, freeing them from the EITest C&Cs and their visitors from the resulting malicious traffic and injects,” Kafeine explained.
This also allowed them to see just how many compromised servers/websites are used by EITest (some 52,000), that most of them are WordPress-based, and that would-be victims came from all over the world.

He says that after the sinkholed EITest the operator reacted by shutting down the C&C proxies.
“Although we witnessed some encoded calls to the sinkhole that embedded commands we would associate with takeover attempts, we cannot verify whether they were initiated by the operator or other researchers or threat actors attempting to interact with the real EITest C&C. However, we will continue to monitor EITest activity as the EITest actor may attempt to regain control of a portion of the compromised websites involved in the infection chain,” he concluded.