How to gain visibility with global IT asset inventory

In this podcast recorded at Black Hat USA 2018, Pablo Quiroga, Director of Product Management at Qualys, talks about how to gain unprecedented visibility with global IT asset inventory.
Here’s a transcript of the podcast for your convenience.
My name is Pablo Quiroga. I’m the Director of Product Management at Qualys, and today I’m going to be speaking about how to gain unprecedented visibility with global IT asset inventory.
A complete visibility of your IT environment is the foundation for effective cybersecurity. Without the full, detailed inventory of your assets your infosec team won’t be able to properly protect your organization because the things that possess the highest risk here are the ones that you don’t know about.
Can you answer critical questions?
Gartner predicts that by 2020, a third of successful attacks experienced by enterprises will be on their shadow IT. A complete global IT asset inventory should help answer the following questions:
- What IT assets you have in your environment?
- Who owns them and who is using them?
- How are they related to each other?
- Is there any unauthorized device or another software in your environment?
- How does the vendor lifecycle impact your environment?
Some of the common challenges when building this inventory are the lack of visibility across hybrid environments. Many disparate point tools provide partial information and the gaps that leap between them are critical. IT asset data is a classic example of the three Vs of Big Data, High Volume, High Velocity and High Variance.

In the IT market today, there is acquisitions happening every day. There is product rebranding done by marketing and engineering teams. In a typical environment, you will see that a vendor is represented in different ways, and a product can be represented in 20 different ways.
Qualys Asset Inventory
A word of advice – aimed for the cloud. Organizations have hybrid environments with IT assets on-premise, in public and private clouds, and with mobile workforces. Legacy tools lack the capability to detect assets in these heterogeneous IT environments. On the other hand, Qualys Asset Inventory can discover all assets in the global hybrid infrastructure, automatically normalize and categorize every hardware and software to our technology catalog which is continuously curated by our team of experts.
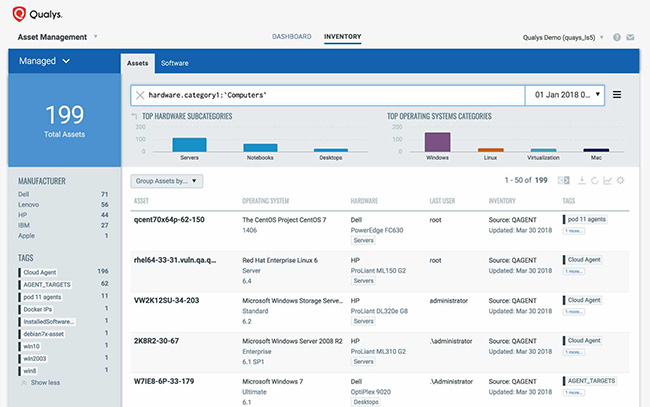
Asset data is enriched with non-discoverable metadata, and indexed for 2-second visibility across your entire environment.
Key capabilities
Let me expand on 6 key capabilities. First, complete visibility of your IT environment. Qualys gives you far and wide horizontal visibility across all IT assets, continuously collects and feed systems, compliance and security data into the central Qualys platform for aggregation, correlation, and analysis. Our family of self-updating centrally managed sensors; including network scanners and lightweight agents collect asset telemetry across legacy data centers, corporate infrastructure, private and commercial clouds, as well remote endpoints and mobile workforce.
Qualys Passive Network Sensor
Our latest addition, a Passive Network Sensor, analyzes network traffic in real time, discovers and profiles every asset as soon as it connects to the network, helping you eliminate blind spots introduced by shadow IT or known IT systems such as industrial, medical devices, or IoT.
Qualys Cloud Platform
Second – scale. As of today the Qualys Cloud Platform does more than a 3 billion device assessments per year, 1 trillion change events per year, and is currently indexing more than 250 billion data points in our Elastic search clusters.
Third – deep visibility into assets. The Qualys Cloud Platform lets you see hardware specs, install software, network connections, approve users, install patches, open vulnerabilities, indications of compromise, and also monitor file changes and more.
It indexes all of these data points giving you the ability to craft queries combining any of them, and get getting any answer to specific questions.
Number four is the ability to add business context and being able to prioritize your assets. Our platform supports static and dynamic tagging, helping you slice-and-dice and prioritize your assets with your business context.
Fifth is automated classification and normalization. Every asset is classified in meaningful, functional categories. For example, devices such as computing, networking and storage, but also into detailed subcategories such as notebooks, servers, and so on. Applications such as databases would be also broken down into relational or relational or NoSQL databases.
CMDB Sync

Final point – integration with your CMDB. Our certified ServiceNow application syncs asset data in both directions. It enables CMDB to better illustrate and map the relationships, connections, hierarchies, and dependencies among IT assets. It helps IT departments to be more effective at a variety of critical tasks including change management and service requests.