Detecting malicious behavior blended with business-justified activity
With organizations moving to the cloud and remote workers becoming the rule rather than the exception, the definition of the network is changing. Add to this the increasing use of IoT devices, encryption and engagement in shadow IT practices, and it’s easy to see why organizations have trouble keeping their network and systems secure.
What’s more, attackers are changing tactics: they are relying less and less on malware and shifting their focus to stealing legitimate credentials and living off the land by using tools that are already deployed in the environment: scripting languages like Python, system utilities like PowerShell, WMI or PsExec, or Microsoft Office’s macros.
Detecting malicious behavior blended so well with business-justified activity is a challenge. Organizations have tried to address this challenge with solutions ranging from the traditional network forensic vendors like RSA NetWitness as well some of the first-generation network traffic analysis (NTA) tools like Darktrace. The buyer trend is moving towards a combination of these two technologies and that is where Awake Security comes in.
Tracking entities across the network
The Awake Security Platform is focused on analyzing communications, whether those are traditional network packets, traffic crossing a vSwitch, traffic from and within cloud workloads and API calls to SaaS applications or serverless computing instances. It also focuses on operational technology networks that are otherwise completely invisible to the security team.
“The platform connects via traditional network SPAN or TAP / cloud TAP / virtual switch TAP / SaaS APIs to get access to data — packets, communications, and so on. We then construct a security knowledge graph (called EntityIQ) by analyzing all these communications in real-time and discovering the business assets — devices, users and applications — in the organization as well as the destinations and domains on the other end of the communications,” Rahul Kashyap, CEO at Awake, explains.

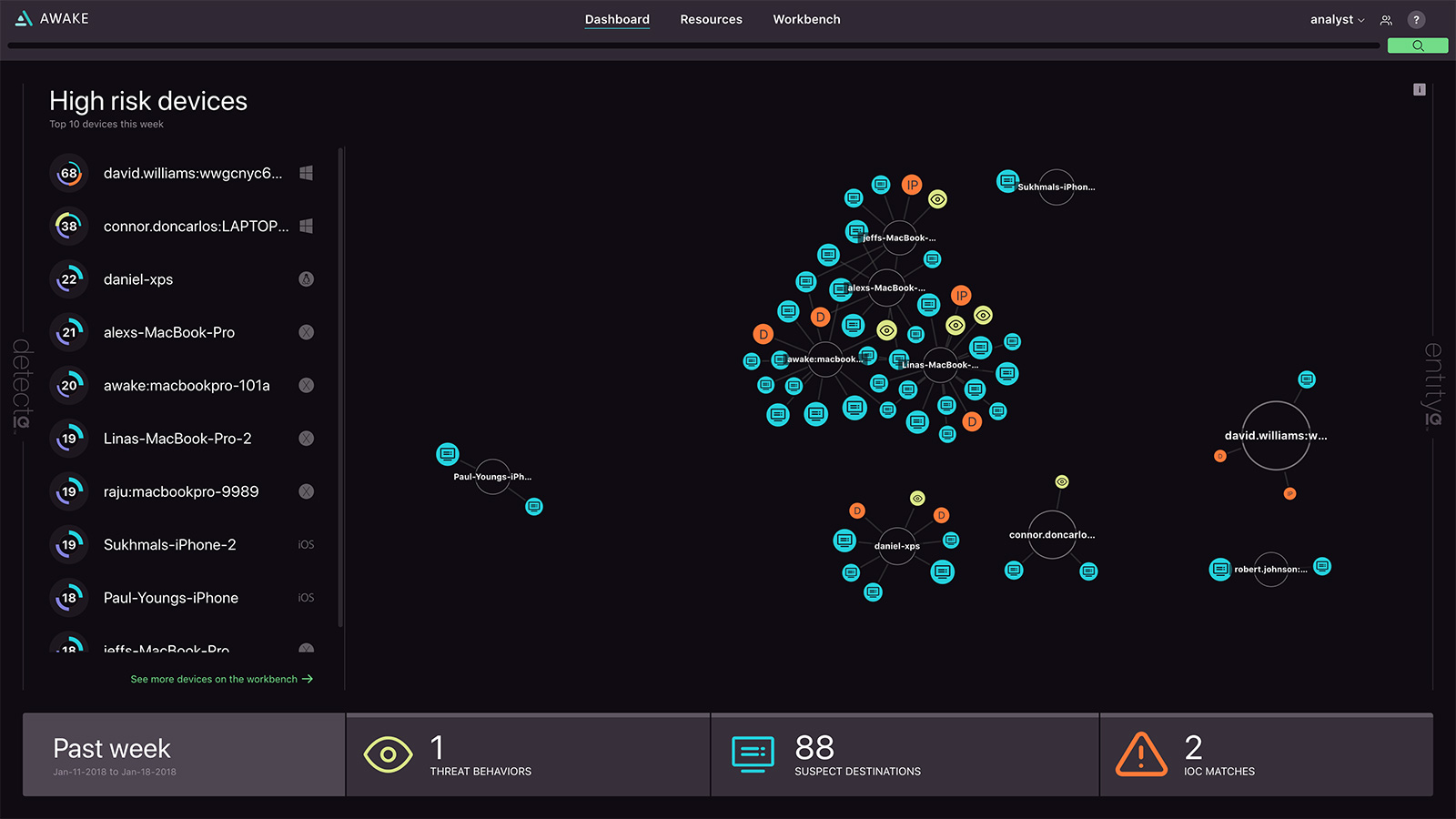
The Awake Security Platform automatically identifies and tracks business assets
The discovery and profiling of the entities on the network is done autonomously. The platform performs full-packet and encrypted traffic analysis and does not rely on (changeable) IP addresses to keep track of devices.
Detecting malicious behavior and intent
Once entities on the network are profiled, the platform attributes behaviors and the relationships to them. The company’s solution then detects new attacker tactics by extracting millions of signals drawn from these entity attributes and behaviors as well as the raw communication and network data, threat intelligence and user behavior analytics. These signals are analyzed by Awake’s neural networks and machine learning models. Among other things this process clusters the entities using similarity analytics and can thus spot outliers exhibiting malicious intent.
This approach efficiently finds attacker tactics, techniques and procedures (TTPs) that span time, multiple network protocols and flows. The company’s research team focuses on ensuring broad coverage of TTPs by aligning with the MITRE ATT&CK framework.

The Awake Security Platform identifies 4 IP phones exfiltrating voice call information
“By attributing and tracking behaviors for each of these entities over time, we can detect behavioral threats, mal-intent, as well as known indicators of compromise. The security team can also enrich the autonomously generated context with institutional knowledge about the entity. The platform delivers a credit-score like risk rating for every entity and detailed behavioral / forensic timelines that show you why we believe that is a high risk,” Kashyap notes.
The Awake Security Platform scores entities in the environment based on risk
The results can be accessed via the product, but can also be consumed with the organization’s SIEM, orchestration platform, with integrations into EDR, etc. Mitigation actions can be performed through integrations with the orchestration platforms, quarantine through EDR, connections to firewalls / proxies, etc.
Adding capabilities to the platform
The Awake platform is also able to evolve as the attackers evolve.
Much like the platform approach Amazon has taken with Alexa, Awake offers an open platform that stays relevant by allowing of-the-moment skills to tackle new security problems as they emerge, rather than forcing customers to overhaul their entire solution to chase the latest threat.
“Awake exposes the knowledge graph and analysts can access it through a language called QueryIQ. That language provides a vocabulary to add new detection and response skills to the platform. Specifically, Awake allows security analysts to easily express attacker tactics using this language,” Kashyap explains.
Skills in Awake take the form of questions security teams can ask of the data and the real-time answers the platform provides. The learning is automated and the new “skills” are pushed down to the platform by the company’s Research Team, but customers and partners can also use the platform to build their own pretty easily.
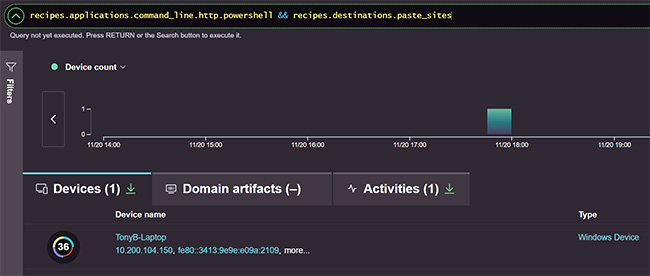
Awake enables easy creation of new detection skills for evolving attacker tactics, techniques and procedures
“For instance, a common attacker TTP is using tools like PowerShell to connect to a known website like Twitter for command and control—detecting that kind of communication is an example of a skill that can be easily added with one line, instead of requiring manual and time-consuming threat hunting expeditions by highly skilled individuals,” he notes.
“Similarly, consider a customer that is concerned about their employees being spear-phished by email appearing to come from a supplier domain. With one line they can build a skill the identifies typosquatted domains that are intended to look like that supplier domain.”

Awake makes detecting targeted typosquatting attacks accessible to any analyst
In short, the company has managed to deliver an advanced network traffic analysis solution that can serve the needs of tier 1 analyst, the threat hunter, as well as the Chief Information Security Officer.