Fugue open sources Regula to evaluate Terraform for security misconfigurations and compliance violations
Fugue has open sourced Regula, a tool that evaluates Terraform infrastructure-as-code for security misconfigurations and compliance violations prior to deployment.
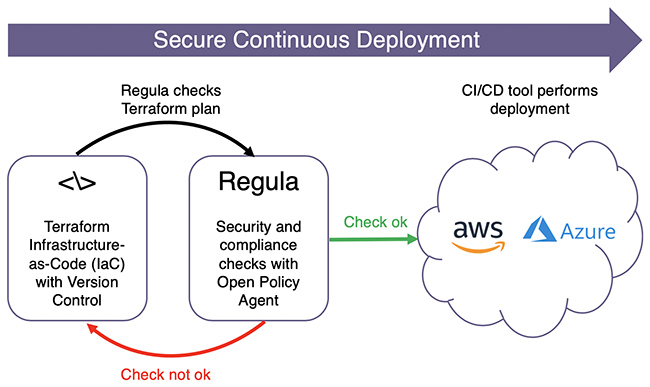
Regula rules are written in Rego, the open source policy language employed by the Open Policy Agent project and can be integrated into CI/CD pipelines to prevent cloud infrastructure deployments that may violate security and compliance best practices.
“Developers design, build, and modify their own cloud infrastructure environments, and they increasingly own the security and compliance of that infrastructure,” said Josh Stella, co-founder and CTO of Fugue.
“Fugue builds solutions that empower engineers operating in secure and regulated cloud environments, and Regula quickly and easily checks that their Terraform scripts don’t violate policy—before they deploy infrastructure.”
Regula initially supports rules that validate Terraform scripts written for AWS infrastructure, and includes mapping to CIS AWS Foundations Benchmark controls where relevant. Regula also includes helper libraries that enable users to easily build their own rules that conform to enterprise policies.
At launch, Fugue has provided examples of Regula working with GitHub Actions for CI/CD, and with Fregot, a tool that enables developers to easily evaluate Rego expressions, debug code, and test policies. Fugue open sourced Fregot in November 2019.
Regula can identify serious cloud misconfiguration risk contained in Terraform scripts, many of which may not be flagged by common compliance standards. The initial release of Regula includes rules that can identify dangerously permissive IAM policies and security group rules, VPCs with flow logs disabled, EBS volumes with encryption disabled, and untagged cloud resources.
Regula works independently of Fugue, but can be integrated with Fugue for end-to-end cloud infrastructure security and compliance. The Fugue SaaS product integrates cloud security into each stage of the software development life cycle.
Fugue enables users to visualize cloud infrastructure environments, detect post-deployment misconfigurations and automatically enforce critical resource configurations through self-healing.
Both Regula and Fugue utilize the open-source Rego policy language, and developers can easily create their own rules for Regula and Fugue using a similar syntax. In addition to Fugue Enterprise, Fugue offers Developer, a free tier available to individual engineers who need to ensure continuous security and compliance of their cloud infrastructure environments.