Keep remote workers and their devices secure with one click
In this interview for Help Net Security, Shailesh Athalye, VP Compliance at Qualys, discusses cloud-based Remote Endpoint Protection and illustrates how security teams can leverage its numerous features.

Qualys recently added malware detection to its cloud-based Remote Endpoint Protection offering. How does it work?
As you know because of the recent surge in the remote workforce, the security of the remote hosts is on top of the mind for the security teams. It became immediately apparent when majority of the hosts shifted remote, that traditional enterprise security solutions deployed inside the organization’s network were utterly ineffective in protecting these remote endpoints, due to the sheer volume of remote hosts connecting over VPNs. What would happen when those remote computers needed to be updated? It would be impractical to deliver thousands of security updates, malware updates via the VPN, over limited bandwidth.
Architecturally superior cloud security solutions like Qualys are well positioned to address the need for protecting remote computers as we could connect directly to the cloud over the internet without the need to route a large volume of traffic through the VPN gateways.
We’re pleased with the reception the offer has garnered, and we have had more than 700 companies registering for the offer. And we didn’t stop there – as we realized we could give customers additional protections by adding the ability to detect malware – and that is the piece that we’ve just announced.
Powered by the Qualys Platform and Cloud Agent, malware detection uses file reputation and threat classification to detect known malicious files on endpoints, servers, and cloud workloads. As a result, security practitioners can respond more quickly to malware on employees’ systems.
What makes Qualys Remote Endpoint Protection unique?
In general, cloud-based security services have an advantage as they connect directly to the cloud over the internet without routing a large volume of traffic through the VPN gateways for assessing vulnerabilities and for applying patches. What’s unique about the Remote Endpoint Protection Offering is that it gives companies:
1. Visibility into what devices are connecting inside their network and what resources the devices are connecting to.
2. It assesses vulnerabilities, malware and security configurations on remote hosts such as Microsoft Office, the Google Suite of products, VPN software and conferencing solutions such as Zoom or Webex.
3. Detects malicious files and processes often missed because a company’s anti-virus tools are only pushed to remote computers connected to the VPN.
4. Prioritizes patches by correlating them with vulnerabilities as well as applying patches directly from the solution vendor’s content delivery networks via the internet, without putting pressure on the VPN and available bandwidth due to the size of the patches.
Not only does Qualys address remote endpoint issues, but we do so with one solution providing a continuous and integrated view of remote endpoint inventory, critical vulnerabilities, misconfigurations and now malware to speed remediation while enabling remote patching. This functionality is seamlessly integrated into one solution.
This approach is a first in the industry as previously companies would cobble together a solution for detecting vulnerabilities, one for patching and another for malware detection. While it did the job, it was complicated, clunky and the data was not consolidated for a true picture of the risk.
What does the process of integrating Qualys Remote Endpoint Protection into an existing security architecture look like?
Remote Endpoint Protection is easily enabled through the Qualys Cloud Platform and Cloud Agent. And like all Qualys Apps, it is self-updating, centrally managed and tightly integrated with other apps in the platform. The Cloud Agent continuously communicates and syncs-up collected data with the Qualys platform including pushing the latest vulnerability signatures and vendor patches. All of which, it does without the need for a VPN and or internal network bandwidth.
Qualys applications cover a broad swath of functionality in areas such as IT asset management, IT security, web app security and compliance monitoring. All apps are based on the same platform, share a common UI, feed off of the same scanners and agents, access the same collected data, and leverage the same user permissions. This lowers the complexity of usage while maintaining a high level of access control throughout the organization.
How can security teams leverage the features of Qualys Remote Endpoint Protection?
The Qualys Remote Endpoint Protection service is extremely easy to enable for customers who already have deployed the lightweight Qualys Cloud Agents. Once the customer signs up for the service, their existing subscription will have workflows and capabilities enabled for remote endpoint security assessment and patching.
The free, updated, Qualys Remote Endpoint Protection offer allows security teams to leverage the lightweight Qualys Cloud Agent to:
- Identify and inventory all remote endpoints including hardware and the applications they are running in real time
- Ensure remote systems are secure with a real-time view of all critical vulnerabilities, malware and misconfigurations impacting the OS and applications
- Decrease remediation response time by automatically correlating required patches with identified vulnerabilities, and prioritizing detected malware
- Deliver patches and respond to malware from the cloud within hours with one click, and all without using the limited bandwidth available on VPN gateways
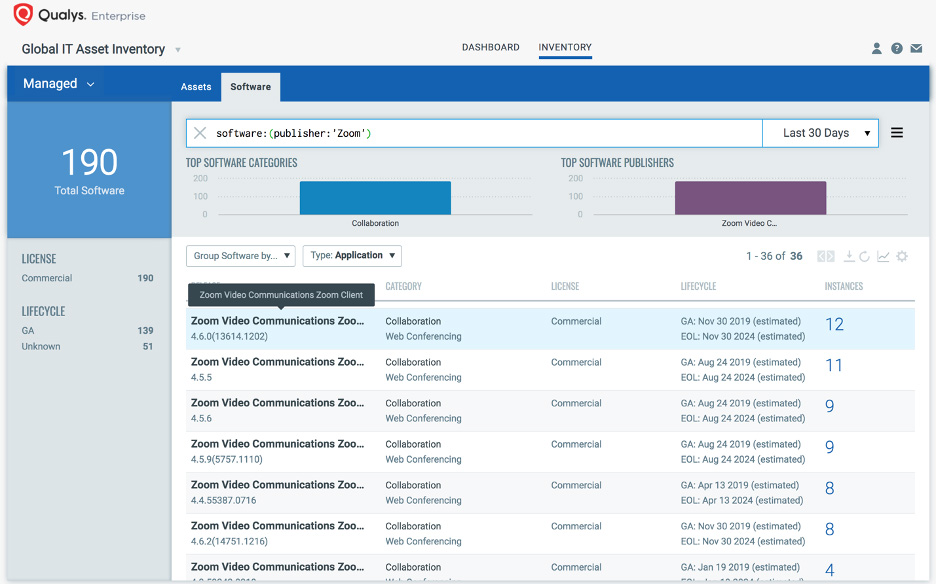
Inventory of collaboration tools across remote endpoints
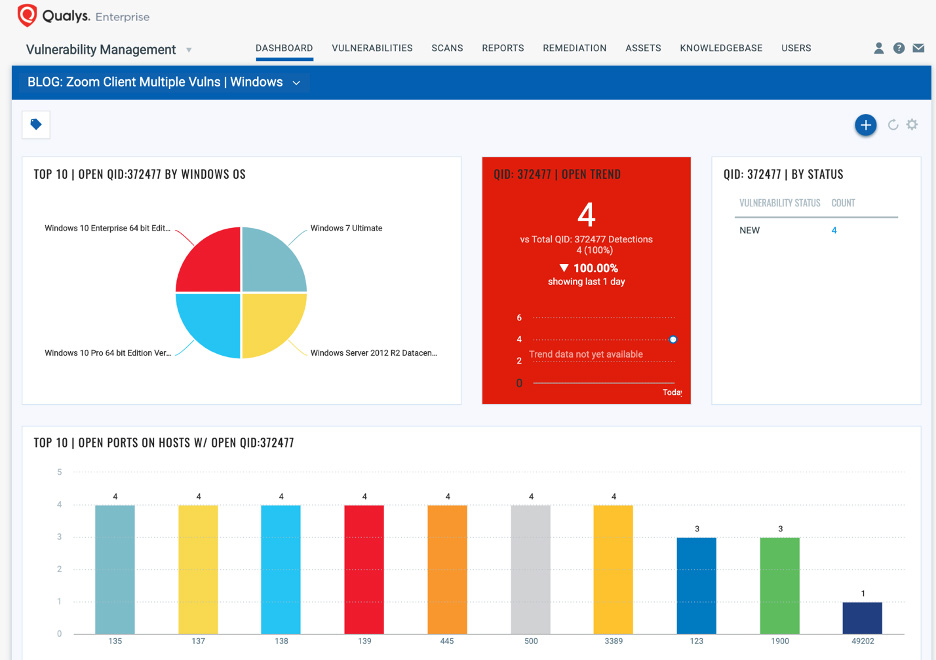
A simple query tags impacted remote hosts with the “CollaborationTools” asset tag for Zoom vulnerabilities:
To help prioritize patching effort, users are provided with a complete view of all vulnerabilities in collaboration and productivity applications across your remote endpoints.
Enabling trending via the dashboard widgets allows user to track specific trends, such as the Zoom vulnerability in the example, in your environment by importing pre-configured Zoom Vulnerabilities Dashboard.
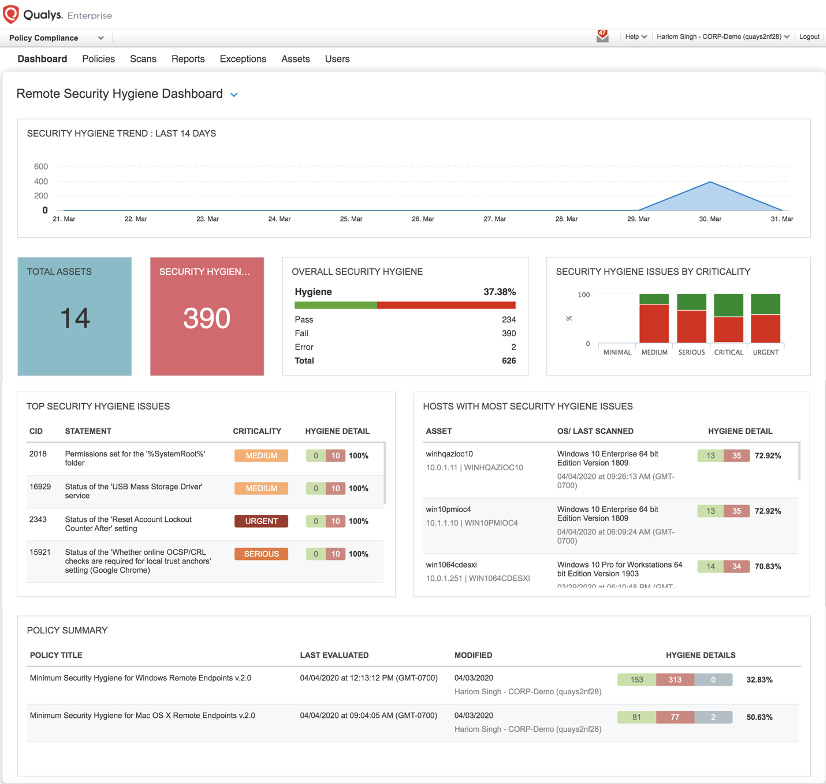
One of the other key aspects of securing remote computers is their configuration hygiene and that you harden security settings of the technologies you are using on the remote computers. You can easily manage your security hygiene and configurations with the Remote Endpoint Protection service.
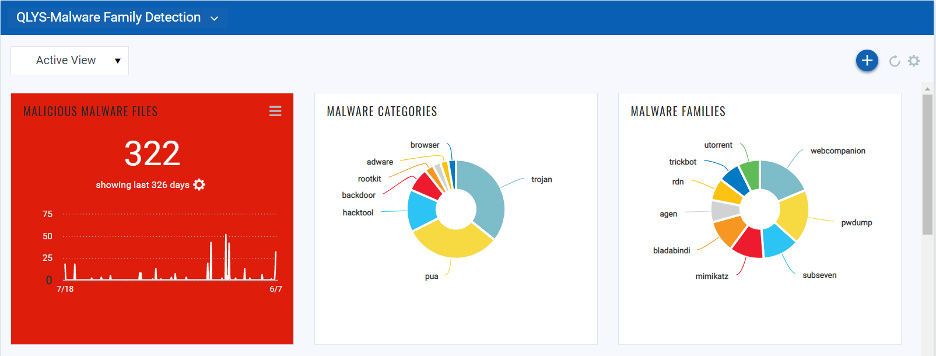
Qualys Malware Detection, integrated with the Remote Endpoint Protection offering and powered by the Qualys Platform and Cloud Agent, uses file reputation and threat classification to detect known malicious files on remote endpoints. As a result, organizations can respond more quickly to malware ultimately increasing their overall security posture.
In summary, with recent remote endpoint surge, attack surface of the organizations has expanded beyond just ‘crown jewels’, as weak remote hosts can compromise the security of the organizations and could result in a data breach.
Qualys Remote Endpoint Protection allows security teams to gain instant and continuous visibility of remote hosts in terms of their vulnerabilities, correlated patches, malware, security hygiene issues. Security teams will be able to prioritize missing patches for critical vulnerabilities and deploy them directly from the cloud.
The patches are delivered securely and directly from vendors’ websites and content delivery networks to ensure there is little to no impact on internet connectivity or the bandwidth of the organization.
The Malware Detection capability integrated in remote endpoint protection detects malware missed by anti-virus and classifies malware into threat categories and malware families to prioritize incident response. We encourage companies to sign up for the free 60-day trial.