New Reveal platform shines a light on post-login identity behavior
Reveal Security released the Reveal Platform, a solution to deliver preemptive identity security across SaaS, cloud, and custom applications. Designed for modern hybrid enterprises, the platform provides end-to-end visibility into both human and non-human identity behaviors.
“Credentials are compromised all the time; it’s a reality in how we have to defend, and now we’re seeing insider and non-human identity threats increasing,” said Kevin Hanes, CEO, Reveal Security. “The problem is once the identity is authenticated and now inside the applications, conventional detection methods which rely on signature and rule-based methods leveraging known Indicators of Compromise become far less effective, as they often struggle to differentiate between legitimate and malicious activity executed by a seemingly “trusted” identity.”
According to Gartner Research, “Without preemptive cybersecurity, no organization is safe. The increasing speed, sophistication and scope of AI-enabled threats is destroying the reliability of existing stand-alone detection and response (DR) cybersecurity methods.”
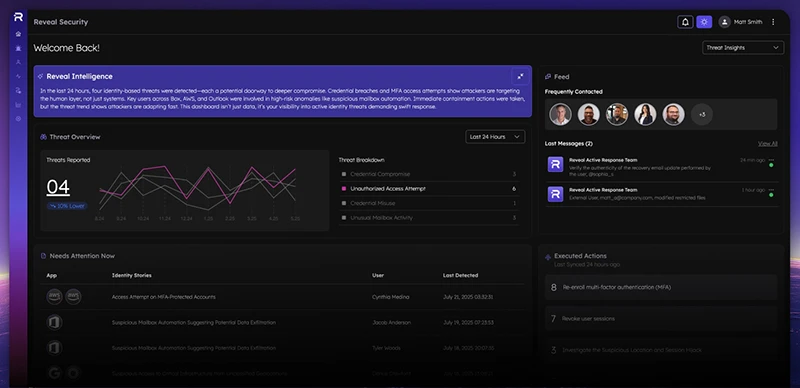
But most security tools monitor identity at the point of login. Reveal goes further – tracking identity behavior across applications and clouds, correlating signals, and detecting anomalies both at and after authentication. With identity attribution, stories of identity behavior, and one-shot response automations, security teams can act quickly and preempt threats.
With its innovative core technology, including rich data, application threat modeling, ML, and AI, Reveal simultaneously protects against account takeover attacks and insider threats in a single platform without overwhelming the SOC with alerts or the need to write detection rules.
- Post-Authentication Visibility: Uncovers what identities do after login across applications like Box, Salesforce, Okta, Microsoft 365, Google Workspace, AWS, Azure, and more.
- Cross-App Behavioral Analytics: Provides the full picture of what identities are doing across the many enterprise applications they use daily.
- Credential Abuse Detection: Identifies unauthorized access and post-login activity resulting from stolen or exploited credentials.
- Insider Threat Protection: Monitors risky users and detects malicious or negligent insider activity.
- Human and Non-Human Behavior Monitoring: Profiles bots, APIs, and GenAI agents just like human users.
- Preemptive Identity Security: Through identity attribution and predictive intelligence, Reveal determines who is acting and why, so security teams can take action before damage occurs.
- One-Shot Response Automations: Instantly suspends accounts, revokes sessions, or updates risk scores based on policy.
- Seamless SOC Integration: Works with SIEM, SOAR, and Slack for contextual alerting and streamlined response. No endpoint agents required.
Reveal’s high-fidelity behavioral intelligence prioritizes alerts by severity and confidence, reducing noise while increasing precision. The platform supports hybrid identity environments, flags risky behavior across user and service accounts, and arms security teams with actionable context.
Real-world examples of Reveal’s behavior-based detections, without rule creation, include:
Detect recon of threat actor using stolen credentials
Reveal detected a coordinated series of suspicious actions across multiple applications affecting cloud file-sharing (BOX) and identity access (OKTA) systems, indicating reconnaissance. Showing deviation from normal identity behavior, these anomalies included account deletions, unauthorized collaboration removals, and unexpected identity verification attempts from the Southern Asia subcontinent. The threat was contained.
Privilege abuse in Microsoft 365
The Reveal Platform detected a coordinated series of mailbox-related administrative operations within Microsoft 365. This activity was immediately flagged due to the identity’s atypical behavior and the security-sensitive nature of the actions, consistent with potential data exfiltration. While each operation was individually valid, their combination exhibited a high-risk pattern, indicative of either an insider threat or the malicious exploitation of elevated privileges, potentially stemming from a compromised administrator account. The account was immediately suspended, and the security team launched an investigation.
Suspicious insider activity in a custom application
Legacy and custom applications are often not well protected by organizations and usually have minimal controls in place. Reveal detected a highly trusted identity logging into a “crown jewel” critical business application and accessing confidential data abnormally. The SOC investigated and determined that a company leader was being specifically targeted by a financially motivated cybercrime group.
CEO impersonation using legitimate credentials
Reveal detected that a company’s top executive was accessing Confluence and browsing content on critical information and business systems. Reveal detected the identity performing anomalous behaviors involving this proprietary information and notified the security team. The information security analysts revoked sessions for that identity to protect the data and to stop the attacker. The executive’s laptop had been stolen while he was already logged into multiple applications.