Oracle customers targeted with emails claiming E-Business Suite breach, data theft
Unknown attackers claiming affiliation with the Cl0p extortion gang are hitting business and IT executives at various companies with emails claiming that they have exfiltrated sensitive data from the firms’ Oracle E-Business Suite (EBS).
The email campaign
According to Google, this high-volume email campaign has been launched from hundreds of compromised accounts in late September 2025.
“Our initial analysis confirms that at least one of these accounts has been previously associated with activity from FIN11, a long-running financially motivated threat group known for deploying ransomware and engaging in extortion,” says Charles Carmakal, CTO at Mandiant – Google Cloud.
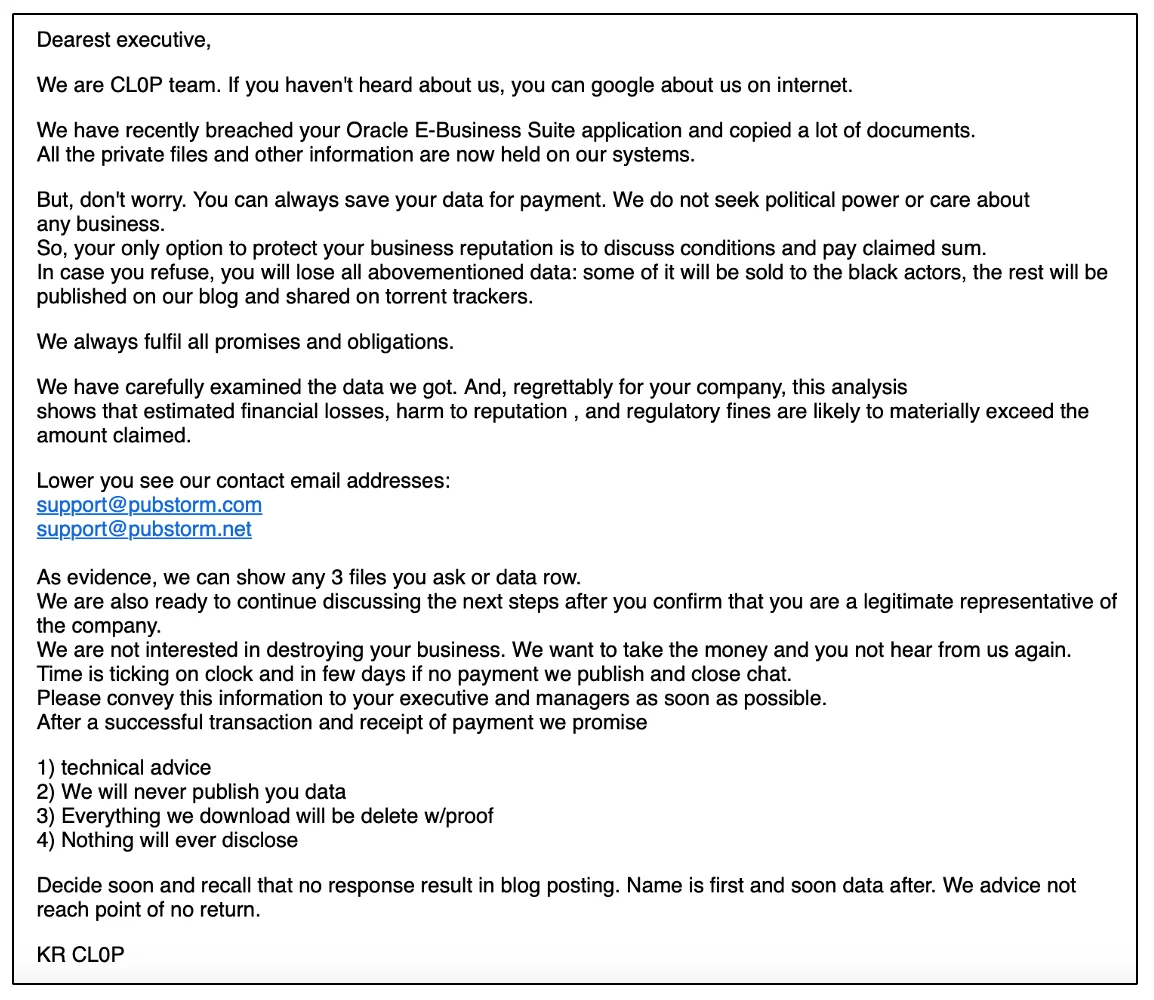
The threat actor is claiming to be affiliated with the Cl0p extortion group, and the emails contain two contact addresses publicly listed on the Cl0p data leak site (DLS). But whether the claims of a data breach or Cl0p involvement are true is currently unknown.
“[Google Threat Intelligence Group] does not currently have sufficient evidence to definitively assess the veracity of these claims,” Carmakal added.
“Attribution in the financially motivated cybercrime space is often complex, and actors frequently mimic established groups like Clop to increase leverage and pressure on victims.”
Citing security firm Halcyon, Bloomberg says the ransom demands are huge, reaching seven and eight figures, and that the attackers shared screenshots and file trees as proof of compromise. (The “proof” has not been independently validated.)
The extortion email (Source: Mandiant)
The Cl0p ransomware / extortion operation surfaced in 2019 and initially targeted victims with ransomware.
But for the last five years, its name has become well known due to attacks exploiting zero-day vulnerabilities in enterprise file transfer solutions such as Accellion FTA and MOVEit. Cl0p attackers abused these flaws to exfiltrate corporate data and demanded that victim organizations pay to prevent the data from being publicly released or sold.
What should targeted organizations do?
Oracle has not yet commented on the situation.
Carmakal advised targeted organizations to investigate their environments for evidence of threat actor activity.
“Alongside our industry partners, we have not yet been able to validate whether the claims made by the threat actor are accurate,” Richard Berkahn, a partner at Atmos First Response Australia & New Zealand, shared on LinkedIn, and noted there have previously been instances of fraudsters impersonating the Cl0p gang.
“There is every possibility that this is a hoax, although we are treating it as an unvalidated threat at this stage. We are not aware of any validated data exfiltration by entities involved,” he added, and advised organisations that use the Oracle E-Business Suite to check their email filter for any extortion emails that may have been quarantined.
“While the email addresses of the threat actor vary, you can also search for ‘pubstorm.com/pubstorm.net’ which should pick up the contents of the email from the threat actor (if you have received them),” he noted.
“While this may be another impersonation event, we are advising organisations who have received any emails from the threat actor to prepare as if the threat actor’s claims are legitimate and mobilise their response team (including cyber insurance support if available), to be on the ready to respond as more information becomes known.”

UPDATE (October 3, 2025, 07:50 a.m. ET):
“Oracle is aware that some Oracle E-Business Suite (EBS) customers have received extortion emails. Our ongoing investigation has found the potential use of previously identified vulnerabilities that are addressed in the July 2025 Critical Patch Update,” Rob Duhart, Chief Security Officer at Oracle Security, has confirmed.
“Oracle reaffirms its strong recommendation that customers apply the latest Critical Patch Updates.”
UPDATE (October 6, 2025, 07:40 a.m. ET):
Cl0p involvement has been confirmed, as well as the fact that they exploited a previously unknown Oracle ESB vulnerability (CVE-2025-61882) in these attacks.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!