Global Threat Map: Open-source real-time situational awareness platform
Global Threat Map is an open-source project offering security teams a live view of reported cyber activity across the globe, pulling together open data feeds into a single interactive map. It visualizes indicators such as malware distribution, phishing activity, and attack traffic by geographic region.
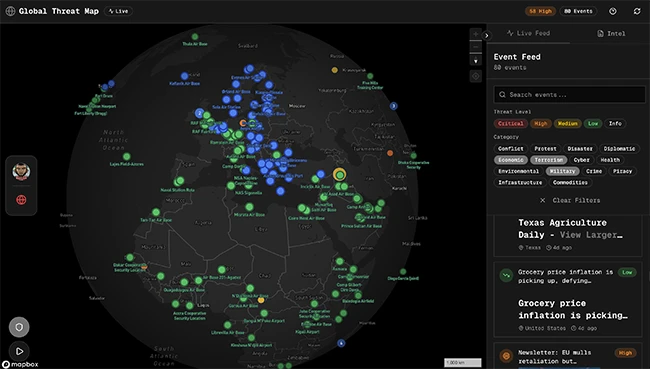
Global threat maps have long been used by security vendors to illustrate attack volumes and regional trends. This project takes a different path by relying on open feeds and community-maintained code, making its data sources and logic visible to users.
What the map shows
The Global Threat Map displays animated arcs between countries and regions to represent observed attack traffic. Data points are grouped by category, including malware, phishing, botnet activity, and suspicious network behavior. The map updates continuously as new data is pulled from upstream sources.
It draws from multiple threat intelligence feeds that publish indicators such as malicious IP addresses and domains. These feeds include community-run sources and security research projects that make their data available for reuse.
“What makes my tool unique is the depth of intelligence it brings together. It goes beyond traditional network threats and attack vectors to include detailed insights into current and historical nation-state conflicts, along with aggregated and pinpointed data on U.S. and NATO military bases worldwide. It also enables deep, in-context research on terrorist groups and other entities, all in one place,” Prosper Otemuyiwa, the creator of Global Threat Map, told Help Net Security.
Intended audience and use
The project is aimed at developers, students, and security professionals who want a visual overview of global threat patterns without relying on proprietary platforms.
Because the project is open source, users can review the code to understand how data is collected, processed, and displayed. They can also modify the map to add new data sources or adjust how events are visualized.
The map should not be used as a sole source for incident response or threat validation. The data reflects what upstream feeds report, which can vary in accuracy and scope.
Open data and transparency
One of the distinguishing aspects of the Global Threat Map is its transparency. Commercial threat maps often provide limited detail about their data sources or filtering logic. This project lists its feeds and processing steps in the repository, allowing users to assess coverage and limitations.
That transparency can help security teams explain what the map does and does not represent. It also allows researchers to experiment with combining threat feeds and visual analytics without licensing restrictions.
Global Threat Map is available for free download on GitHub.

Must read:
- 40 open-source tools redefining how security teams secure the stack
- Firmware scanning time, cost, and where teams run EMBA

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
