
Mobile privacy audits are getting harder
Mobile apps routinely collect and transmit personal data in ways that are difficult for users, developers, and regulators to verify. Permissions can reveal what an app can …

Smart glasses are back, privacy issues included
AI smart glasses are the latest addition to fashion, and they include a camera, a microphone, AI, and privacy risks. After Google Glass failed to gain traction more than a …

EFF calls out major tech companies on encryption promises
The Electronic Frontier Foundation (EFF) has introduced a new campaign called Encrypt It Already, focused on expanding the use of end-to-end encryption in consumer technology …

Apple’s new privacy feature limits how precisely carriers track your location
Apple users are already accustomed to managing app-level location permissions, and a new privacy feature in iOS 26.3 extends that control to cellular networks. Called Limit …

Wearable tech adoption continues as privacy worries grow
Over 1 billion users wear devices for tracking steps, sleep, heart rate, and other personal metrics. These devices collect a continuous stream of sensitive data, often tied to …

France Travail fined €5 million for failing to protect job seeker data
France data protection authority CNIL has fined public employment agency France Travail €5 million for failing to ensure the security of personal data of job seekers. …

Google agrees to pay $135 million over Android data harvesting claims
Google agrees to pay $135 million to settle a proposed class action lawsuit brought by Android smartphone users over alleged unauthorized cellular data transmissions. After …

Samsung tackles shoulder surfing on Galaxy devices
Our phones hold our most personal details, and we use them everywhere. On the bus, in elevators, and while waiting in line, screens are often visible to people nearby. The …
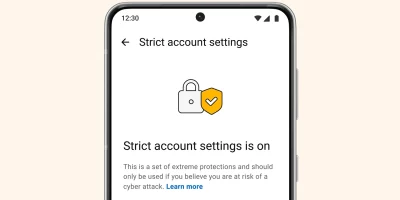
WhatsApp rolls out new security feature to protect users from sophisticated attacks
To add an extra layer of protection to its end-to-end encryption, WhatsApp has begun rolling out a new privacy and security feature called Strict Account Settings. It is …

Grammarly and QuillBot are among widely used Chrome extensions facing serious privacy questions
A new study shows that some of the most widely used AI-powered browser extensions are a privacy risk. They collect lots of data and require a high level of browser access. The …

AI’s appetite for data is testing enterprise guardrails
Privacy programs are taking on more operational responsibility across the enterprise. A new Cisco global benchmark study shows expanding mandates, rising investment, and …

One-time SMS links that never expire can expose personal data for years
Online services often treat one-time links sent by text message as low-risk conveniences. A new study shows that these links can expose large amounts of personal data for …