Bug in Symantec’s anti-virus engine can lead to system compromise
Google Project Zero researcher Tavis Ormandy has unearthed a critical remote code execution vulnerability in the anti-virus engine powering Symantec’s endpoint security products (including Norton-branded ones).
The flaw (CVE-2016-2208) has been responsibly disclosed to the company, and it released a new version of its Anti-Virus Engine (v20151.1.1.4) with the fix incorporated. It will delivered to customers via LiveUpdate along with the usual definition and signature updates, Symantec reassured.
In the security advisory accompanying the security update, Symantec noted twice that “the most common symptom of successful exploitation resulted in an immediate system crash,” aka the “Blue Screen of Death.”
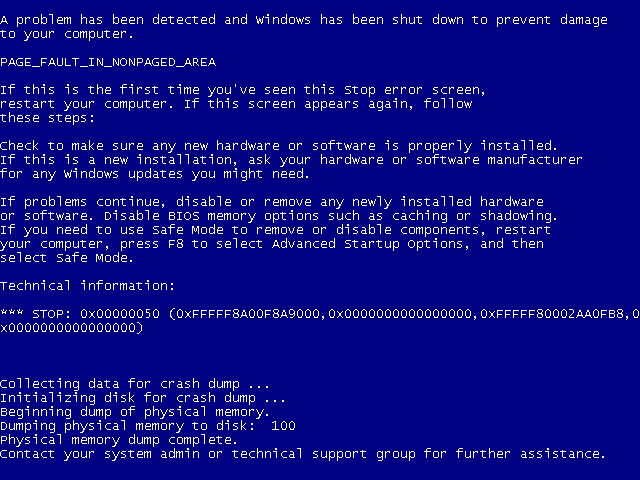
There’s more to it, though.
“On Linux, Mac and other UNIX platforms, this results in a remote heap overflow as root in the Symantec or Norton process. On Windows, this results in kernel memory corruption, as the scan engine is loaded into the kernel (wtf!!!), making this a remote ring0 memory corruption vulnerability – this is about as bad as it can possibly get,” Ormandy explained.
“On Windows with Symantec Endpoint Antivirus, this vulnerability permits code execution as NT AUTHORITY\SYSTEM in the ccSvcHost.exe process. On Norton Antivirus for Windows, this code is loaded into the kernel and results kernel pool corruption.”
The flaw can be triggered without any user interaction. It’s enough that the user receives a malformed portable-executable (PE) header file via email or downloads it (intentionally or unintentionally) from a website, and Symantec software will start scanning it for malware and trigger the exploit.
There is no indication that the flaw is currently being exploited in the wild.
Ormandy said that aside from this Anti-Virus Engine bug, he discovered and notified the company about other (7 or 8) critical RCE vulnerabilities in their products. To fix these, users will have to download a patch (when made available).