ShiftLeft: Fully automated runtime security solution for cloud applications
When talking about data loss prevention, the first thing that comes to mind are solutions aimed at stopping users from moving sensitive documents/data out of a network.
But there is a different type of data loss that app developers should be conscious and worry about: cloud applications inadvertently sending critical data to unencrypted/public databases/services.
Fuelled by the adoption of microservices and short software development cycles, this is the fastest growing problem in application security today. Recent data leakage incidents experienced by Uber (when 57 million records were breached because developer credentials were accidentally leaked into GitHub) or Wag Labs (when the dog walking service publicly leaked customer’s addresses and lockbox key codes to their corporate website) prove this point.
So how can you prevent such an incident from happening to you?
ShiftLeft is a relatively new offering that provides fully automated secure development and runtime protection for cloud applications.
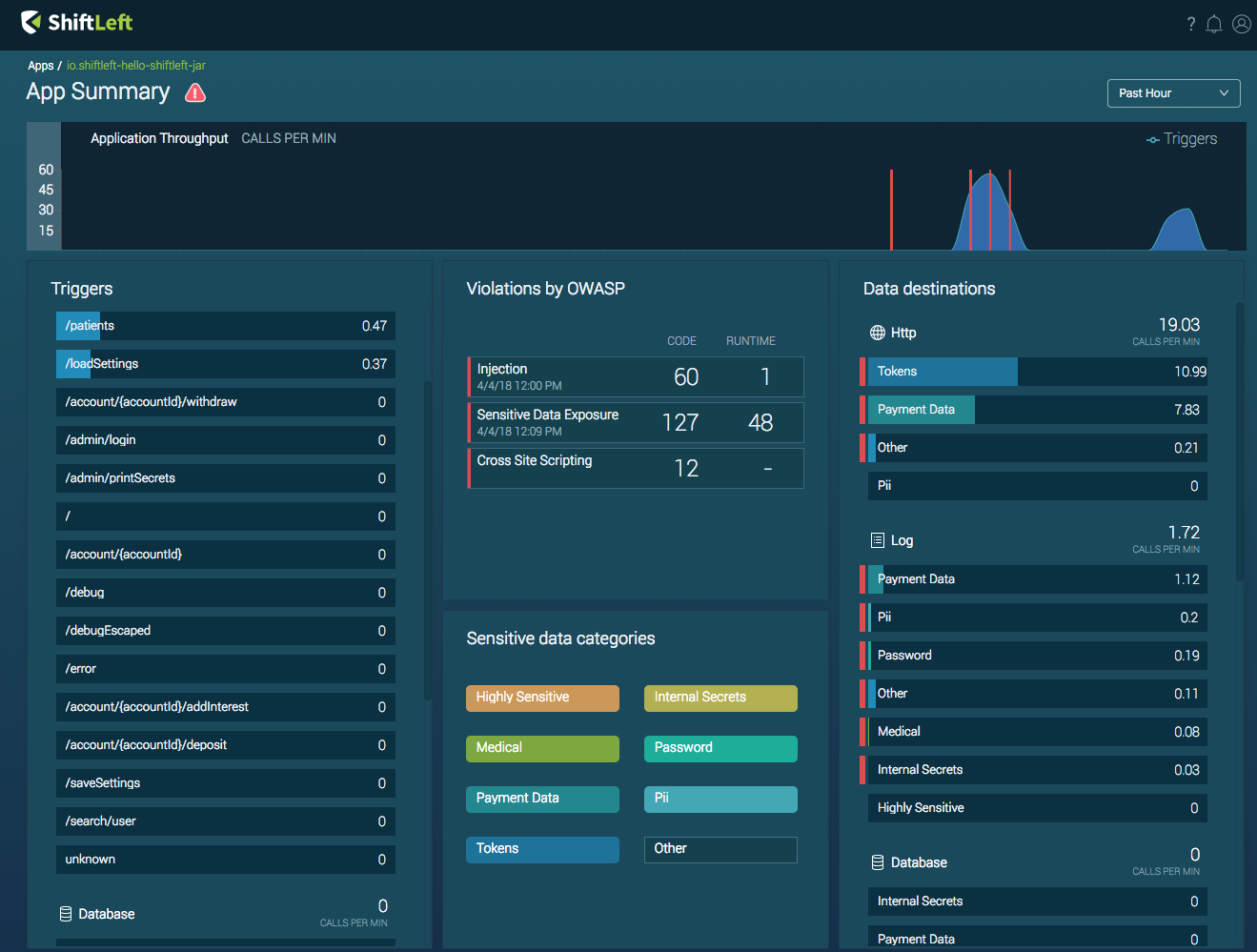
Main dashboard
It extracts “Security DNA” from applications, maps how sensitive data is flowing from applications to data sinks and shows you how that flow is being handled, and shows potential problems: data leaks, but also unknown vulnerabilities in the customer’s proprietary code and know (CVEs associated) vulnerabilities in open source code that the app takes advantage of.
A new approach
Traditional technologies for protecting sensitive data – Data Loss Prevention solutions, Cloud Access Security Brokers, Web Application Firewalls – are widely used by enterprises and they are typically deployed between users and the Internet to monitor and prevent data leakage.
But they have their limitations. For example, they may not identify all sensitive data and can be defeated by encryption and obfuscation. An application can also leak sensitive data by accidentally writing secrets to an API that is not monitored by DLP. And let’s not forget that there are ways to get data outside of the organization without going through the Internet.
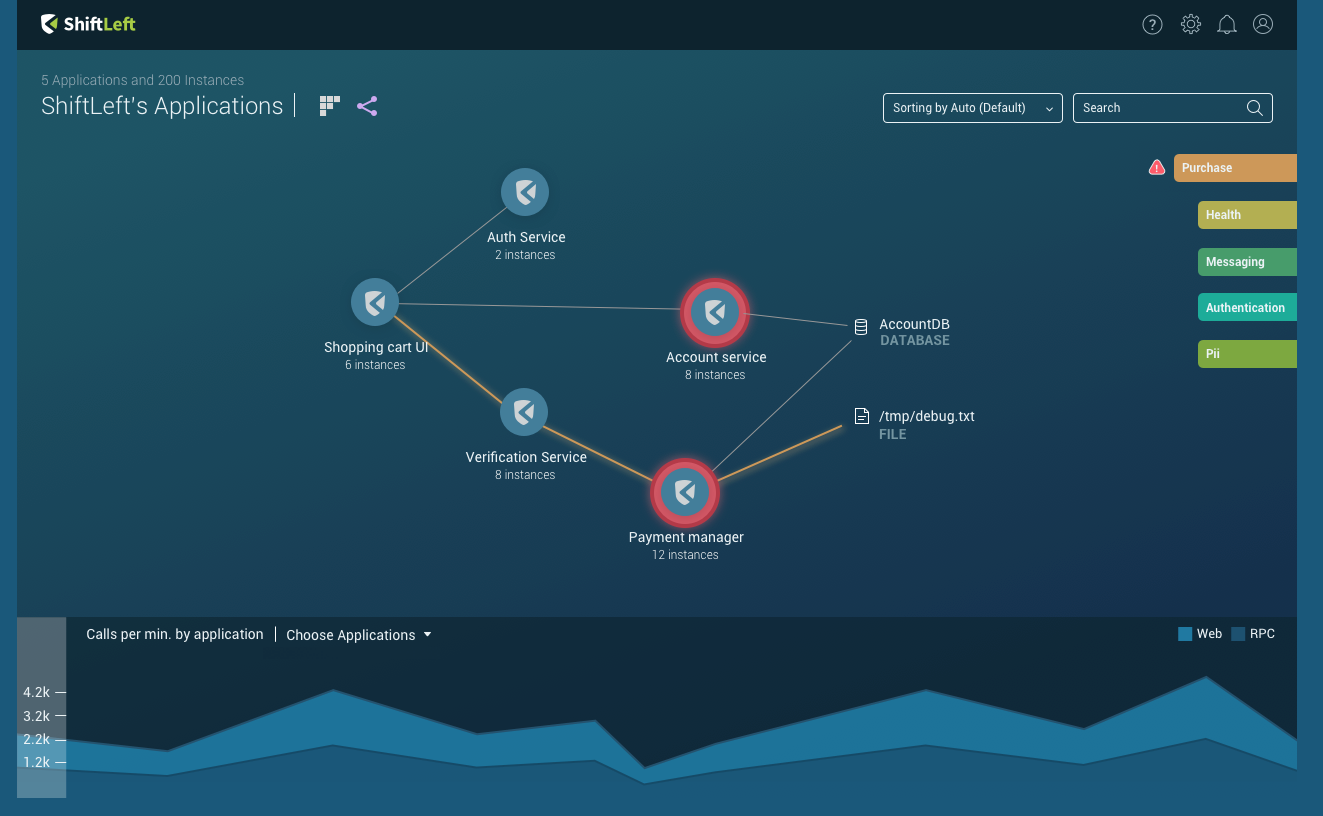
ShiftLeft approaches the problem from another vantage point: it starts tracking the data between an application (where the sensitive data originates and is processed) and its outputs (where it’s stored/published/delivered).
Data flow topology view
How ShiftLeft works
ShiftLeft uses a two-pronged approach for monitoring an application:
- It uses semantic graphing to understand how an application works and extract its Security DNA for each of its iterations/builds, and
- Runtime monitoring, which leverages that graph, is used to understand which parts of the application instruments in real time.
The Security DNA is used to create a custom microagent to be installed in the runtime environment. It will provide runtime protection by blocking sessions that may lead to security issues and/or by providing precise and actionable information for developers so they can quickly fix vulnerabilities and leaks.
“In addition to the runtime protection, because we have the insights from production, we help the developers prioritize which vulnerabilities to fix first with low MTTR, and even provide the exact lines of code in question. By understanding both the dev and production environments, we can definitely conclude when a vulnerability is real,” ShiftLeft CTO Chetan Conikee explained to Help Net Security.
If that in itself is not enough to make you interested, also consider this information:
ShiftLeft can quickly scan each version of the application that’s been pushed into production and automatically extract all security relevant aspects but does not impact continuous application delivery.
New issues can be detected in seconds or minutes (depending on the complexity of the application) but the app’s runtime in not heavily affected because the solution does not instrument the entire surface of the app, just the areas where data is leaking or an attacker can take control of the application.
Also, the solution provides no false positives. “Because we understand how the application works and we know which variables names are sensitive, we can track how they flow across each microservice. Hence we can map their journey and see how they are handled (i.e. encrypted vs. decrypted) and all of their entry and exit points,” Conikee told us.
Example of a data leakage, with the exact line of code that needs to be updated
Good to know
ShiftLeft is aimed primarily at securing cloud-based workloads (cloud applications and microservices).
“The hard limitations are more about language support,” Conikee pointed out. At the moment, ShiftLest supports Java. .Net support is coming in Q2 2018, and that for Python, Go and Javascript will follow shortly thereafter.
“We find that web applications are more likely to have fully embraced modern development practices (agile, cloud, CI/CD, microservices, etc.),” he noted.
“While these practices unlock tremendous innovation in the software development life cycle, they also make security more complex and decrease the time in which security teams have to find and fix vulnerabilities as the pace of releases increase from quarterly to monthly to weekly or even daily. While many other aspects of software development have become automated, security predominantly still relies on manual processes. Hence, it is falling further and further behind.”
DevOps or operations are usually the primary users of the solution – they are the ones who will regularly monitor the application and be on the receiving end of alerts. The developers are on the receiving end of tickets created by the former, but the task of fixing the underlying vulnerabilities in the code is made much easier because the production data weeds out the false positives and the developer knows exactly which line of code needs to be updated.
The security team is involved in the process inasmuch as they are involved in setting the policy that determines the thresholds they are confortable with for various security problems.
Conclusion
Increasingly shorter software development cycles often mean less time to spot and fix potentially dangerous changes that are introduced in the code. Automated discovery is, therefore, a must and each new build has to be subjected to it.
The process has to be quick and the results have to be granular, to allow for helpful insights and speedy remediation. ShiftLeft can provide all of that.