Losses due to BEC scams are escalating
Despite falling down on the list of most often reported Internet-facilitated crimes, Business Email Compromise/Email Account Compromise is still the type of crime that results in the biggest losses.
In fact, according to the numbers released by the FBI’s Internet Crime Complaint Center (IC3), the victims of those crimes lost over $676 million in 2017. Compared to the 2016 numbers (over $360 million), that’s an increase of nearly 88%.
“Business Email Compromise (BEC) is a scam targeting businesses working with foreign suppliers and/or businesses regularly performing wire transfer payments. Email Account Compromise (EAC) is a similar scam that targets individuals,” the IC3 explains the difference between the two.
But, since these scams are carried out by fraudsters compromising email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfer of funds, and the techniques used in the BEC and EAC scams have become increasingly similar, the organization tracks these scams as a single crime type.
$1.42 billion of reported losses
Non-payment/non-delivery scams are still the ones that reported most often, followed by scams fueled by a personal data breach.
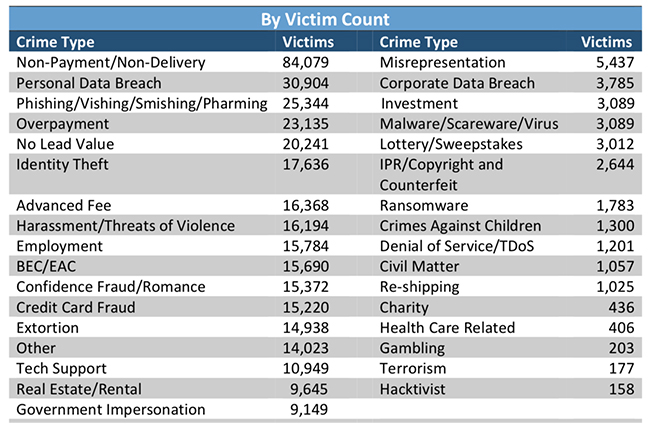
“In non-payment situations, goods and services are shipped, but payment is never rendered. In non-delivery situations, payment is sent, but goods and services are never received,” the IC3 explains.
Personal data breach fraud is the result of the leak/theft and unauthorized use of the victim’s personal data.
The number of reported corporate data breaches has risen slightly since last year (3,785 in 2017 vs 3,403 in 2016), but the total amount of monetary loss due to this type of crime has fallen ($60.9 million in 2017 vs $95.9 million in 2016).

The number of reported tech support scam incidents is pretty much the same (10,949 in 2017 vs 10,850 in 2016), but losses have risen ($14.8 million in 2017 vs $7.8 million in 2016).
There are many variations of this scam, and criminals are constantly changing their tactics to continue the fraud, the IC3 warns.
“For example, in addition to telephone calls, pop-up and locked screens, search engine advertising, and URL hijacking/typosquatting, criminals now use phishing emails with malicious links or fraudulent account charges to lure their victims. Criminals also pose as a variety of different security, customer, or technical support representatives and offer to resolve any number of issues, including compromised email, bank accounts, computer viruses, or offer to assist with software license renewal,” they explain.
“Some recent complaints involve criminals posing as technical support representatives for income tax assistance, GPS, printer, or cable companies, or support for virtual currency exchanges. In some variations, criminals pose as government agents, who offer to recover losses related to tech support fraud schemes or request financial assistance with ‘apprehending’ criminals. The ‘fake refund’ variation of tech support fraud is increasing in reports and losses.”
The added danger when it comes to tech support scams is that the scammers usually convince victims to install a remote access tool, allowing them to rifle through the victim’s devices and steal sensitive information that can be used to further defraud the victim and to target the victim’s contacts.
Finally, it’s interesting to note that the number of reported instances of ransomware-fueled attacks has fallen: in 2016 there were 2,673, in 2017 were 1,783.