Downloads of known vulnerable open source components increase 120%
Sonatype today released its fourth annual State of the Software Supply Chain Report, which reveals the widespread use of vulnerable software components by businesses around the world.

While open source continues to be a key driver of innovation – with software developers downloading more than 300 billion open source components in the past 12 months – hackers are exploiting this growing trend, and even beginning to inject vulnerabilities directly into open source projects. The findings show that use of vulnerable components has increased by 120%, leaving organisations that lack proper governance wide open to attacks.
However against this backdrop, the report reveals the critical role automation plays in mitigating risk and supporting innovation, with automated software supply chains 2X more efficient and 2X more secure than manual parsing.
Other key analysis includes examination of critical issues in the open source software environment and ecosystem, with 62% of businesses admitting to not having proper knowledge about the OSS components in their applications. Currently over 1.3 million vulnerabilities in OSS components do not have a corresponding CVE advisory in the public NVD database.
“As open source accelerates to its zenith of value, the underlying fundamentals of the ecosystem and the infrastructure supporting it, are increasingly at risk,” says Wayne Jackson, CEO of Sonatype. “A series of high profile and devastating cyber attacks last year demonstrated the intent and ability to exploit security vulnerabilities in software supply chains. This year’s report proves, however, that secure software development isn’t out of reach. The application economy can grow and prosper in regulated, secure environments, if managed properly.”
The comprehensive report incorporates a combination of public and proprietary data to examine patterns and practices underpinning open source software development and modern software supply chains. Additional findings include:
Supply, and demand for, open source shows no sign of slowing down:
- More than 15,000 new or updated open source releases are made available to developers every day
- The average enterprise downloaded 170,000 Java components in 2017, up 36% year over year.
Managed software supply chains are 2X more efficient and 2X more secure:
- Automated OSS security practices reduce the presence of vulnerabilities by 50%
- DevOps teams are 90% more likely to comply with open source governance when security policies are automated.
Hackers are beginning to assault software supply chains:
- Over the last 18 months, a series of no less than 11 events triangulate a serious escalation of attacks on the software supply chain
- These assaults, which include hackers injecting vulnerabilities directly into open source projects, represent a new front in the battle to secure software applications.
The window to respond to vulnerabilities is shrinking rapidly:
- Over the past decade, the meantime to exploit open source defects in the wild has compressed four-fold, going from an average of 45 days to just 3.
Governments are stepping in, as enterprises struggle to self-regulate:
- 19 different governmental organisations around the world have called for improved OSS security and governance.
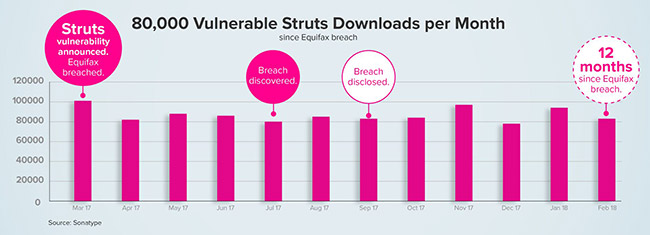
“We are seeing more breaches in open source software because of the gravitational force that pulls features, complexity, and technical debt towards a software system over time, which make it very difficult to patch in a timely fashion Unfortunately, that hasn’t changed the consumption rate of open source software by developers. This is consistent with what I believe is a growing concern… that developers may have surrendered to the idea that all software is vulnerable and have known vulnerabilities. We must give developers better supply chain options where quality and security are intrinsically designed-in,” said Kevin E. Greene, Principal Software Assurance Engineer, The MITRE Corporation.