Money is still the root of most breaches
Verizon has released its annual Data Breach Investigations Report (DBIR), which offers an overview of the cyber security incidents and data breaches that happened in/were discovered in the past year.
Based on an analysis of incident and breach reports by 81 contributing organizations – companies, CERTs, law enforcement agencies and cybercrime units, etc. – from around the world, the DBIR offers insight into current cyber attack trends and the threats organizations in various industry verticals and parts of the world face.
2019 cyber attack trends: the “WHO”
The researchers analyzed 32,002 security incidents that resulted in the compromise of an information asset. Of those, 3,950 were data breaches, i.e., incidents that resulted in the confirmed disclosure of data to an unauthorized party.
The report is massive, so we’ll highlight some interesting tidbits and findings:
- 70% of breaches perpetrated by external actors (except in the healthcare vertical, where it’s 51% external, 48% internal)
- 86% of breaches were financially motivated
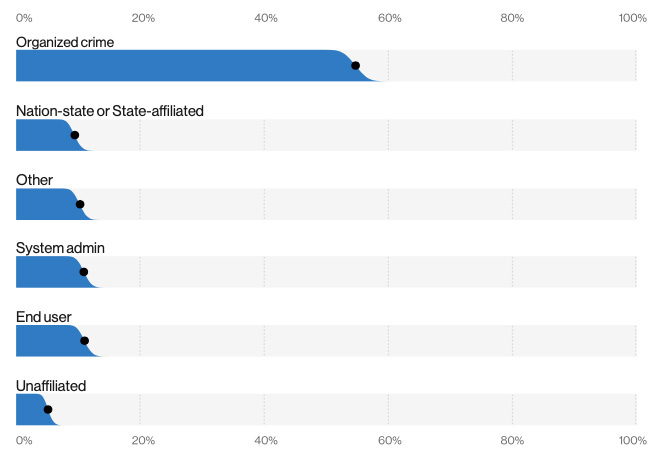
- Organized criminal groups were behind 55% of breaches
- 72% of breaches involved large business victims
“This year’s DBIR has once again highlighted the principal motive for the vast majority of malicious data breaches: the pursuit of profit. This is surprising to some, given the extensive media coverage of national security-related breaches. However, it should not be. Most malicious cyber actors are not motivated by national security or geopolitical objectives, but rather by simple greed,” the data scientists who compiled the report noted.
“Financially motivated breaches are more common than Espionage by a wide margin, which itself is more common than all other motives (including Fun, Ideology and Grudge, the traditional ‘go to’ motives for movie hackers).”
2019 cyber attack trends: the “HOW”
The majority of data breaches (67% or more) are caused by credential theft, social attacks (phishing, business email compromise, pretexting) and errors (mostly misconfiguration and misdelivery of documents and email).
“These tactics prove effective for attackers, so they return to them time and again. For most organizations, these three tactics should be the focus of the bulk of security efforts,” they advised.
Another interesting finding is that attacks on web apps were a part of 43% of breaches, which is more than double the results from last year. The researchers put this down to more workflows moving to cloud services and attackers adjusting to the shift.
“The most common methods of attacking web apps are using stolen or brute-forced credentials (over 80%) or exploiting vulnerabilities (less than 20%) in the web application to gain access to sensitive information,” they shared.
Less than 5% of breaches involved exploitation of a vulnerability, and it seems that most organizations are doing a good job at patching – at least at patching the assets they know about.
“Most organizations we see have internet-facing assets spread across five or more networks. It’s the forgotten assets that never get patched that can create dangerous holes in your defenses,” the authors pointed out.
Most malware is still delivered by email and the rest via web services. Attackers have mostly given up on cryptocurrency mining malware, RAM scrapers and malware with vulnerability exploits, but love password dumpers, malware that captures app data, ransomware and downloaders.
Even though it is a small percentage of all incidents, financially motivated social engineering is on the rise – and attackers have largely stopped asking for W-2 data of employees and switched to asking for the cash directly.
Cloud assets were involved in about 22% of breaches this year, while the rest were on-premises assets.
“Cloud breaches involved an email or web application server 73% of the time. Additionally, 77% of those cloud breaches also involved breached credentials. This is not so much an indictment of cloud security as it is an illustration of the trend of cybercriminals finding the quickest and easiest route to their victims,” they noted.
Use the information to improve defenses
An interesting finding that can be used by defenders to their advantage is that attackers prefer short paths to a data breach. Throwing things in their way to increase the number of actions they have to take is likely to decrease their chance of making off with the data.
Knowing which actions happen at the beginning, middle and end of incidents and breaches can also help defenders react quickly and with purpose.
“Malware is rarely the first action in a breach because it obviously has to come from somewhere. Conversely, Social actions almost never end an attack. In the middle, we can see Hacking and Malware providing the glue that holds the breach together. And so, [another] defensive opportunity is to guess what you haven’t seen based on what you have,” the authors noted.
“For example, if you see malware, you need to look back in time for what you may have missed, but if you see a social action, look for where the attacker is going, not where they are. All in all, paths can be hard to wrap your head around, but once you do, they offer a valuable opportunity not just for understanding the attackers, but for planning your own defenses.”
What should organizations do to bolster their cyber security posture?
DBIR report author and Information Security Data Scientist Gabe Bassett advises organizations to keep doing what they are doing: anti-virus at the host, network, and proxy level plus patching and filtering (e.g., with firewalls) will help push the attackers towards other attacks.
“Address the human element. The top actions (phishing, use of stolen credentials, misconfiguration, misdelivery, and misuse) all involve people. No-one is perfect so find ways to set people up for success and be prepared to handle their mistakes,” he noted, and added that all organizations should have some level of security operations.
“You can’t make the defenses high enough, wide enough, deep enough, or long enough to keep an attacker out if you don’t have someone watching the wall. For large organizations this means having a dedicated security operations center. For smaller ones it may mean taking advantage of economies of scale, either by acquiring managed security services directly, or by using services (payment systems, cloud services, and other managed services that have security operations incorporated).
Finally, to add extra steps to attackers’ path and to deter all but the most persistent ones, they should use two factor authentication whenever possible.
