Review: Code42 Incydr – SaaS data risk detection and response
Incydr is Code42’s new SaaS data risk detection and response solution, which enables security teams to mitigate file exposure and exfiltration risk without disrupting legitimate collaboration.
Code42 focuses on the problems related to the massive “work from home” shift, i.e., the fact that many different collaboration tools are being used within global enterprises. While those tools allow people to collaborate more efficiently, they also allow them to share sensitive company data. Unfortunately, traditional security tools are not capable of minimizing (or eliminating) the risk of insiders using that capability for ill ends.
What does Incydr do?
Incydr keeps an eye on all file-associated events that happen across the company’s environment and shortens the time it takes to detect and respond to data risk caused by an insider threat.
It does that through (Windows, macOS, and Linux) endpoint agents, which detect the creation, modification, deletion, sharing, etc. of files. The associated data is collected centrally and classified according to several dimensions of data risk: file information, vector information (information about where, when and how it’s being moved), and user information.
Incydr tries to investigate and preserve as much metadata as possible for each dimension:
- File dimension: Monitors all files, keeps metadata as filename, owner, size, path, hash, etc.
- Vector dimension: Web browser (domain name, active browser title URL, etc.), cloud syncs (Google, Microsoft, Dropbox, etc.), file sharing (FTP, curl, etc.), removable media (vendor, model, volume name and size, serial number, part ID), and so on
- User dimension: Identifies behavioral patterns (remote activity, off hours file events, attempts of concealed exfiltration), offers additional focus on monitoring users with higher level of risk factors (third-party contractors or departing employees), keeps up to 90 days of user activity, etc.
The Incydr engine uses artificial intelligence (AI) and machine learning (ML) to get answers to questions such as “When does this user normally do their job?” or “Did the user access these files in the past or is this the first time and it’s being sent to their personal Gmail?”
Incydr offers support for integration with various systems: Gmail DLP, Office365 DLP, HR systems, Jira issue tracking systems, and pretty much any identity service (i.e., LDAP, SAML).
Working with Incydr
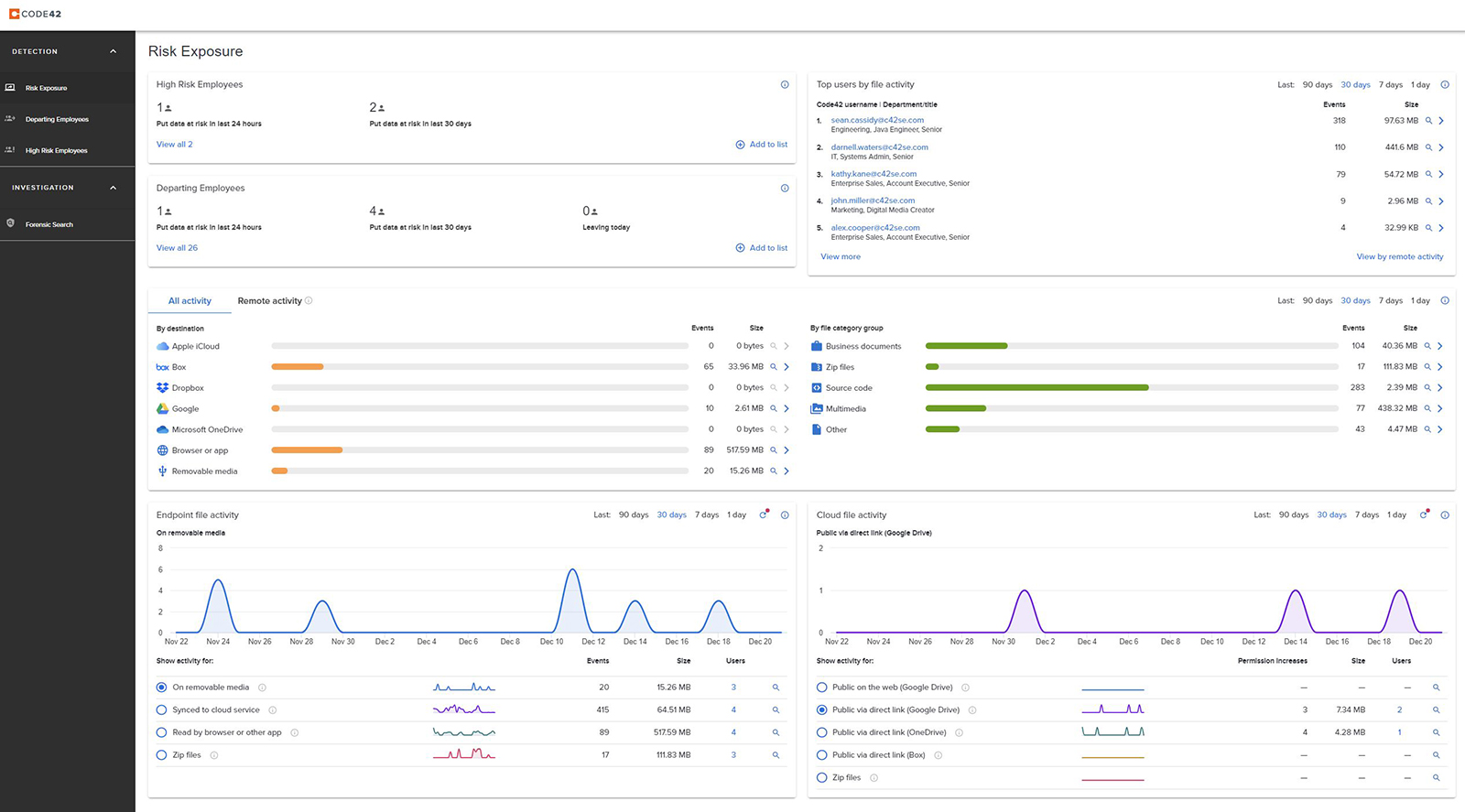
Incydr presents a simple interface divided into two main categories: DETECTION and INVESTIGATION (Forensic Search). The default view is the (DETECTION) Risk Exposure board, where the most important information is grouped and presented. The Risk Exposure dashboard offers an overview of several activity aspects/lenses:
Figure 1. – The Risk Exposure dashboard
The “Departing Employees” lens shows the latest risky file-related activities of users who have either told the company that they are leaving or have been told by the company that they are being let go.
Most users will take data with them when they leave a company. And even though they’ve been given a company computer and instructed not to use it for personal things, most (if not all) employees will sometimes use it to check their personal email account or social media account just because it’s quicker than switching to a personal device.
Incydr allows the company to differentiate between innocuous use of private accounts (e.g., a user sending/uploading personal photos) and malicious use (e.g., a user trying to take company data with them as they leave).
Figure 2. – The Departing Employees lens sorted by File events
Let’s explore the width of data collected by Incydr. In the above example, a user (Sean) – who’s part of an engineering team handling sensitive intellectual property and has accepted a position with a competitor – has been responsible for 962 file events in the last 90 days. A closer look is definitely warranted.
The user profile shows four broad categories:
- File activity by destination
- File activity by file category group
- Endpoint file activity
- Cloud file activity
Figure 3. – The user profile
From the above, it’s obvious that Incydr detects connections to many cloud providers and recognizes different types of files, as well as detects different types of endpoint and cloud file activities.
You can further explore every single event or investigate the last 90 days trough Forensic Search, but for now let’s delve into one of Incydr’s early access features: “Risk indicators observed”.
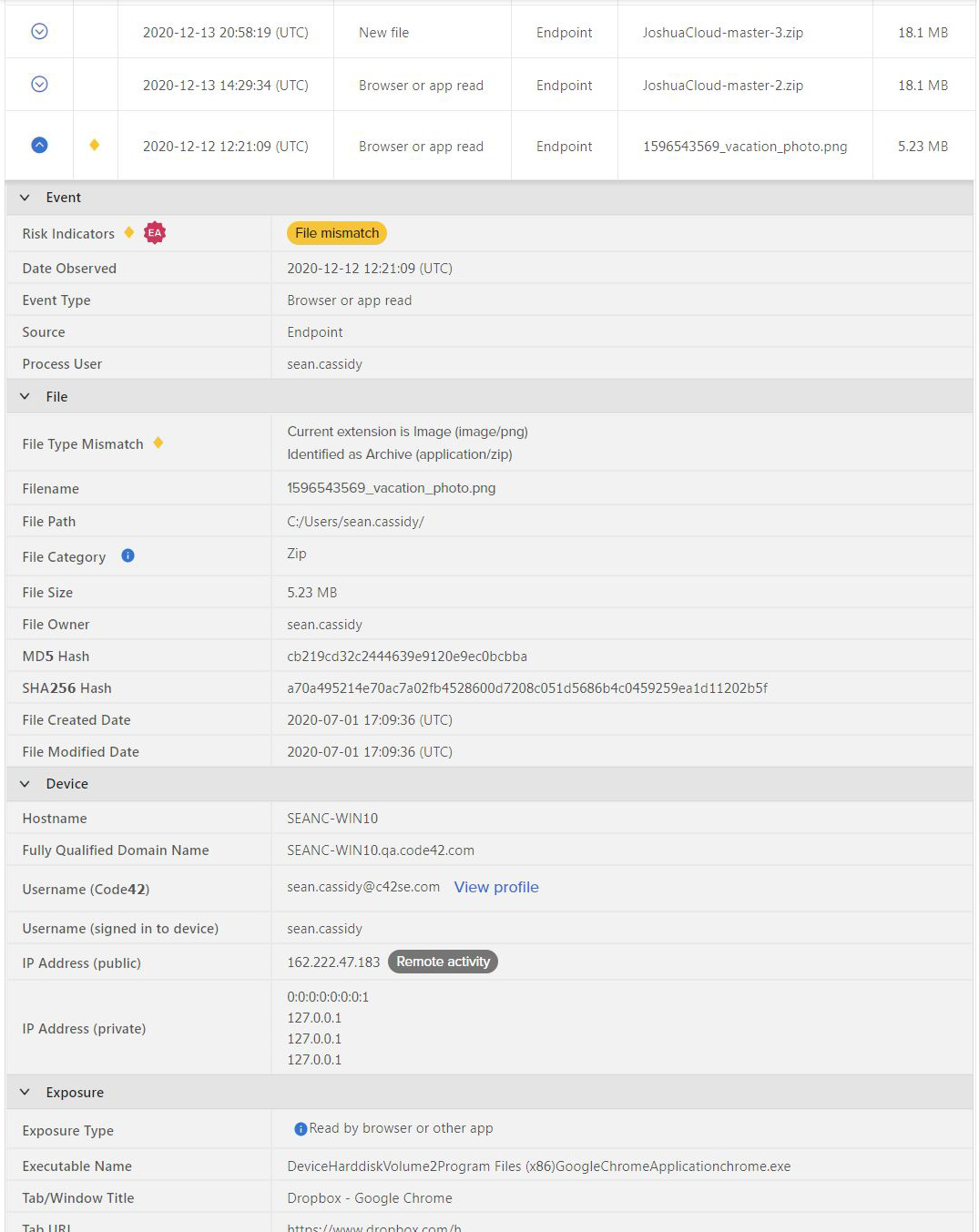
Figure 4. – Departing employee user profile with emphasis on “Risk indicators observed”
While on the surface Sean might seem to lead a normal corporate life, he has been busy renaming some archive files to make it look like they are vacation photos and uploading them to Dropbox (the company uses Google Drive) via the Chrome browser:
Figure 5. – Risk indicators
Incydr discovers and flags the “file mismatch” after reading the file headers and “seeing” that the file is an archive file but has an image-related extension.
Is there a legitimate reason for making a ZIP file look like a PNG file? I can’t really think of one. In this scenario, this indicator should be enough to trigger a visit/call from the company’s HR and legal personnel to Sean.
It’s good to note here that during the monitoring all files are hashed and encrypted with a unique AES256 user key, so the actual files are accessible in their raw format only to security administrator-type of personnel with delegated access in Incydr and to the users themselves (if they need it for backup or restore purposes).
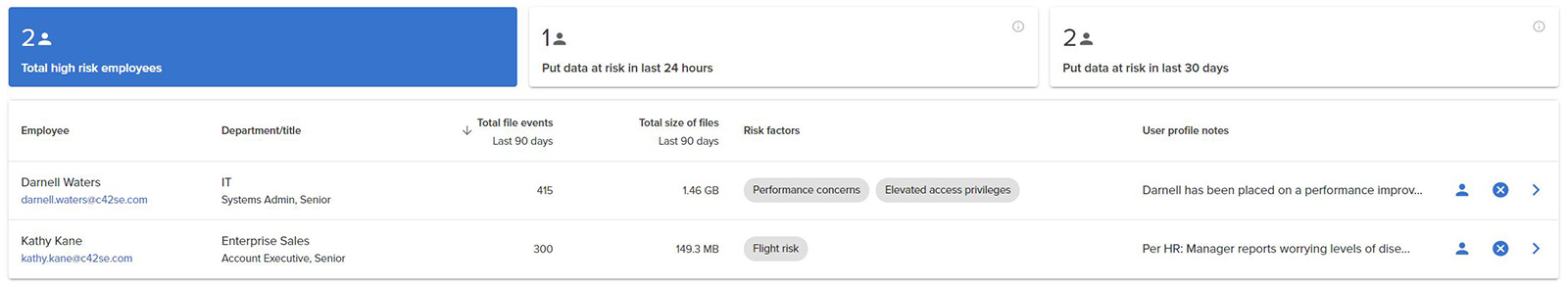
Figure 6. – The High Risk Employees lens sorted by File events
The High Risk Employees lens is similar to the Departing Employees lens, but has one additional category: “Risk factors”. These are:
- High impact employee – e.g., VP of the engineering department
- Elevated access privileges – e.g., system administrators
- Performance concerns – e.g., the employee has been placed on a performance improvement plan
- Flight risk – e.g., the employee is in line for a promotion, but is not fully satisfied
- Suspicious system activity – e.g., the employee has previously been a victim of a phishing attack
- Contracted employee
The greater the number of risk factors associated with an employee, the greater the “weight” of Incydr’s scrutiny of that specific employee will be.
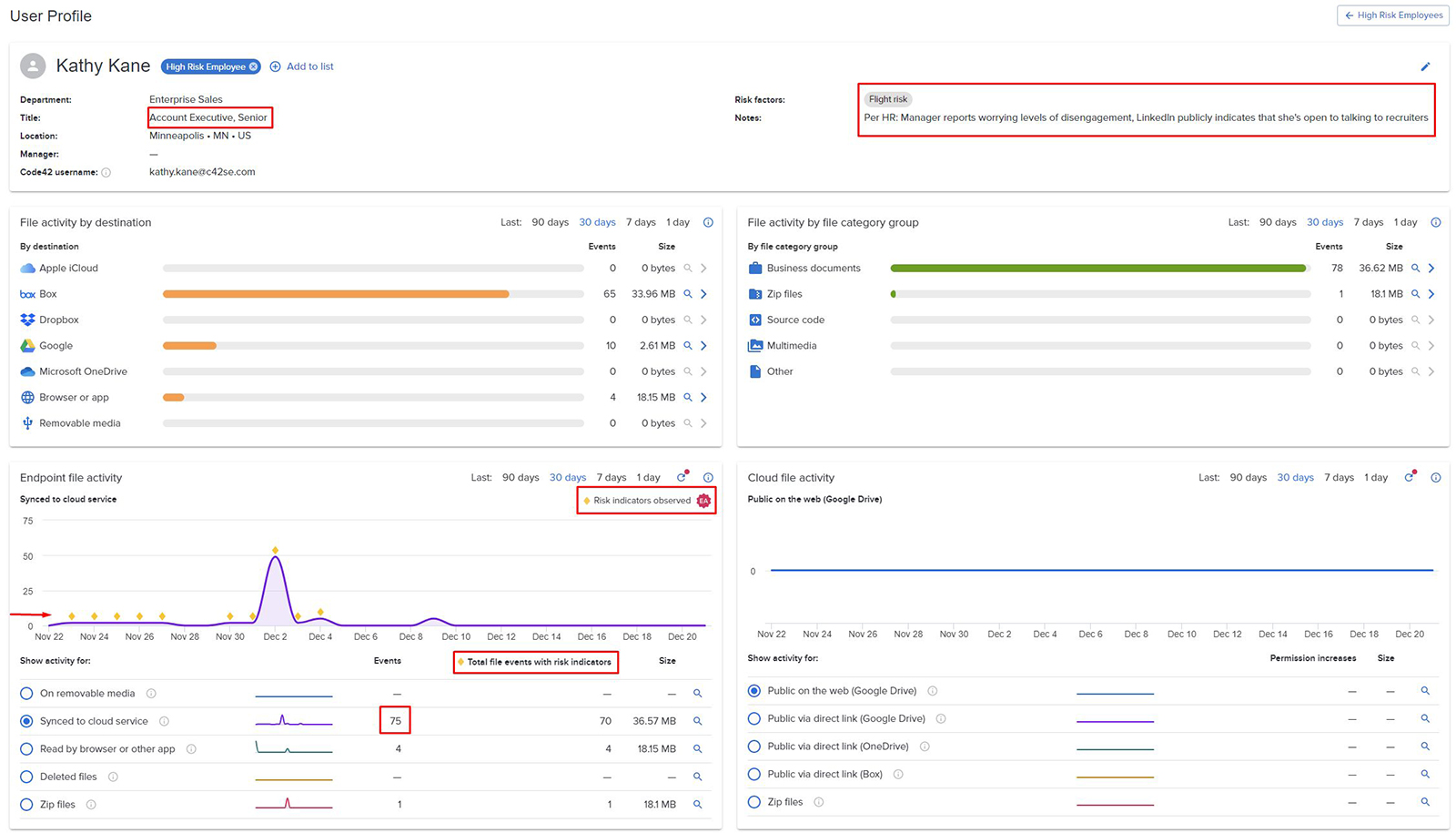
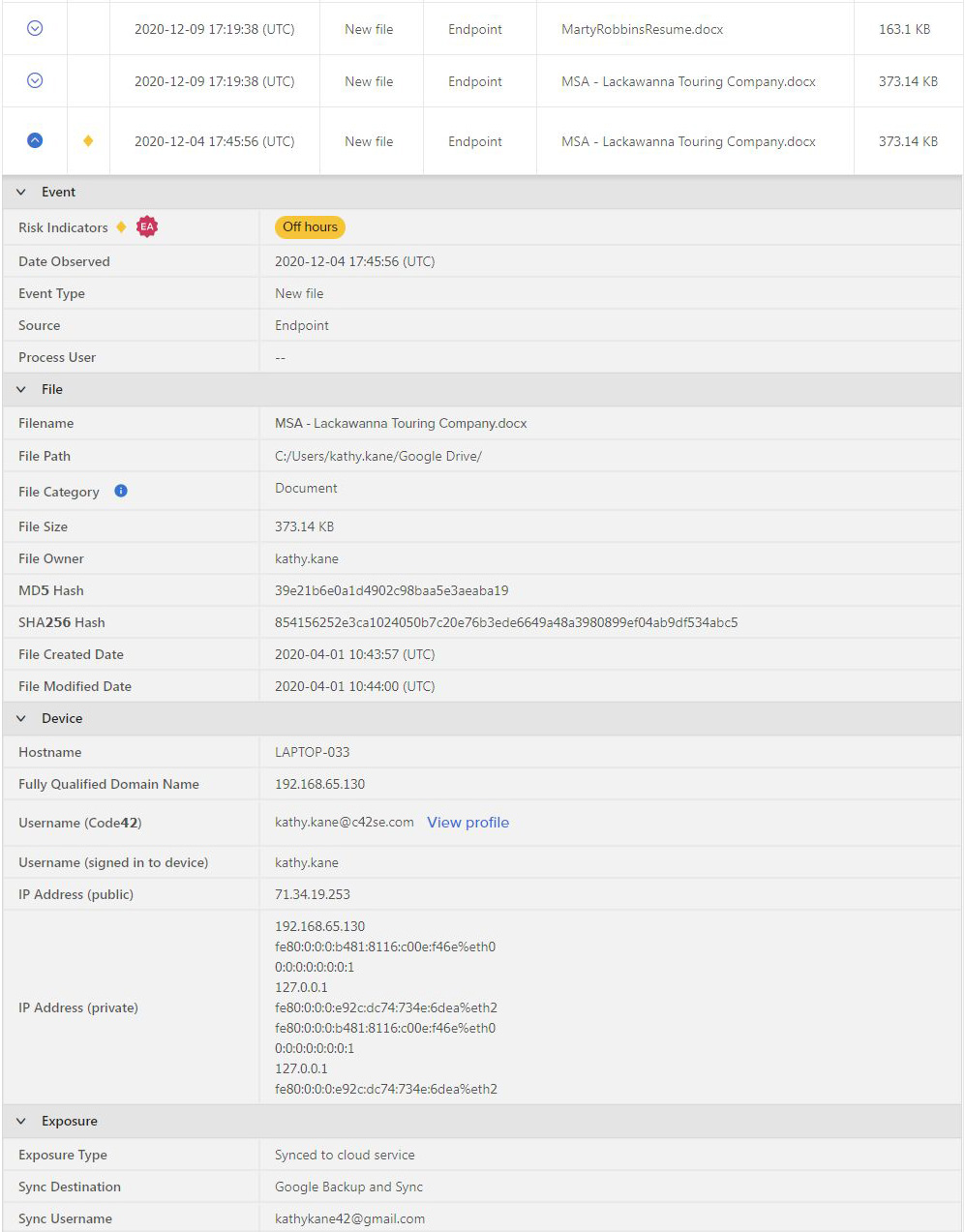
In this hypothetical scenario, let’s look at the risk indicators observed for Kathy Kane, a sales account executive with the company, who’s in a high-risk, senior position, and has been labeled a “Flight Risk” after the HR department noticed certain online activities.
Figure 7. – High risk employee user profile with emphasis on “Risk indicators observed”
Figure 8. – Risk indicators
Let’s look at one of the risk indicators: the report/alert was triggered by an “Off hours” event that happened on company-assigned equipment (network info included), which involved syncing data to a cloud service with personal credentials.
Can you think of a legitimate reason for an employee uploading a client’s Master Service Agreement to their personal cloud storage account? Neither can I. Again, this is where HR and legal personnel might get involved.
Forensic Search
The reports you’ve previously seen (shown via the two employee lenses) were automatically generated by Forensic Search but were created based on the criteria provided by the lenses.
Forensic Search allows you to query the Incydr database by applying approximately 50 different filters (partly shown in the following screenshot):
Figure 9. – Forensic Search
But even with all the AI and ML power, there will always be situations where human input/ judgment is irreplaceable, because sometimes you need a human to beat human logic.
How is Incydr different?
Similar data risk detection products might show that a file was accessed by a web browser, but they won’t tell you where the file was actually sent/uploaded.
Incydr is able to tell you, for example, that a file has actually been uploaded to a GitHub repository through a web browser and that the destination is a source code repository because it’s used in the production environment.
In another example, Incydr is able to tell you that a user has uploaded a whole bunch of stuff to a social media account (e.g., Reddit) through a web browser. The security team sees where the files ended up and can check which files those were.
Conclusion
Licensing packages start at 500 users, meaning Incydr is perfect for bigger corporate entities as their endpoint border consists of thousands (if not tens of thousands) of devices operated by employees, most of which are now working from home and might do things that they otherwise wouldn’t be doing from an office.
I’m sure most system administrators and IT managers will like this product, but some employees might raise objections about “spying” and “surveillance”. The latter objection might be countered by the fact that Incydr is GDPR-compliant and fully compliant with German privacy laws, which are even stricter than EU laws.
To counter employees’ “we’re being spied on” remarks, companies need a set of clearly defined procedures, roles and permissions, as Incydr may be used by those in technical, support, and even legal roles inside the company.
I’ve always been proponent of solutions that do one thing and do it well, and I find Incydr to be exactly that. It detects data manipulation and exfiltration on the endpoints by users, and it may be an efficient way to keep your company’s employees honest.