A clever phishing campaign is targeting Office 365 users
Microsoft is warning about an ongoing, “sneakier than usual” phishing campaign aimed at Office 365 users.
An active phishing campaign is using a crafty combination of legitimate-looking original sender email addresses, spoofed display sender addresses that contain the target usernames and domains, and display names that mimic legitimate services to try and slip through email filters.
— Microsoft Security Intelligence (@MsftSecIntel) July 30, 2021
The phishing emails
The phishers are using various themes as lures, and the emails are sent from email addresses from various top-level domains.
The sender addresses contain variations of the word “referral” – e.g., zreffertalt.com.com, refferal.net, irefferal.com, and similar. The emails are made to look like they point to a shared document stored on Microsoft SharePoint, a web-based collaborative platform that integrates with Microsoft Office, and they include Microsoft branding.
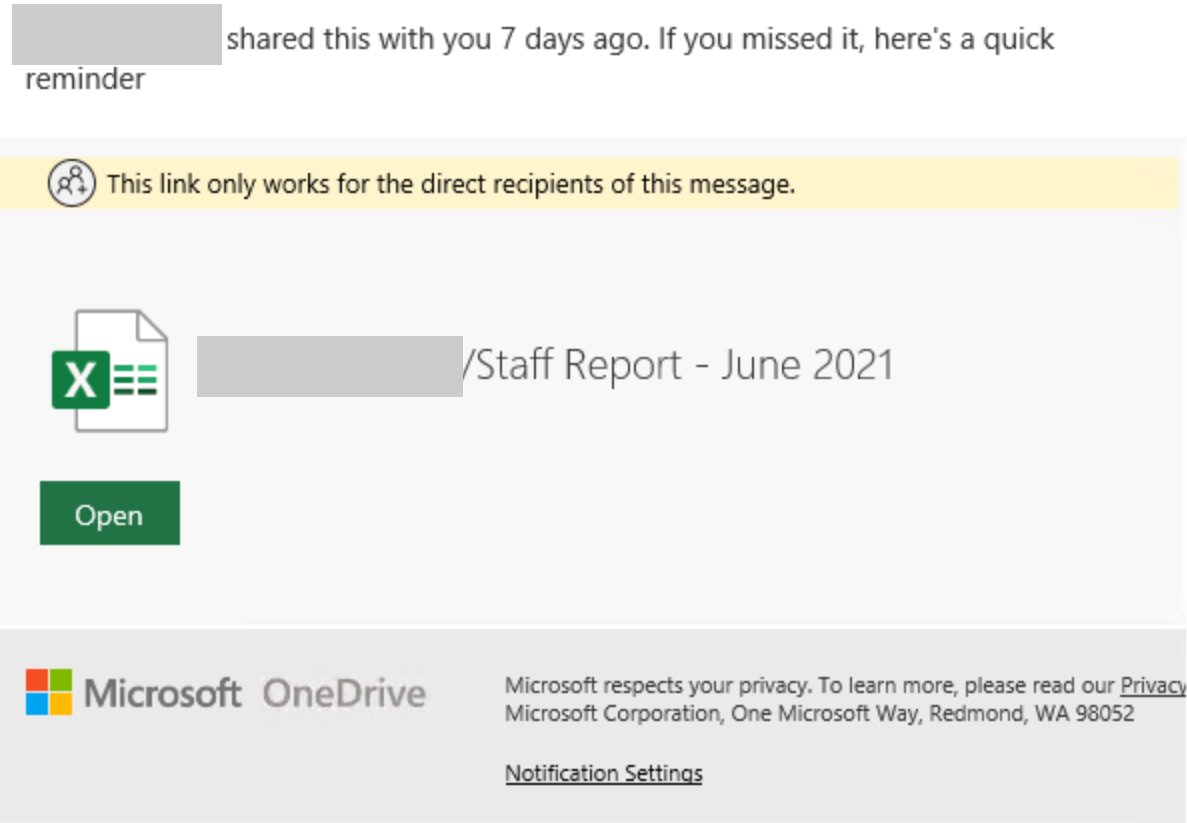
The fake documents are purportedly staff reports, “pricebook changes,” contain information about bonuses, and so on. But clicking on the link will take users to an Office 365-themed phishing page.
“The emails contain two URLs that have malformed HTTP headers. The primary phishing URL is a Google storage resource that points to an AppSpot domain that requires the user to sign in before finally serving another Google User Content domain with an Office 365 phishing page,” Microsoft noted.
“The second URL is located within the notification settings and leads to a compromised SharePoint site that the attackers use to add legitimacy to the attack. Both URLs require sign-in to continue to the final page, bypassing many sandboxes.”
The use of Google’s and Microsoft’s cloud infrastructure host phishing pages is just one of the ways phishers are trying to evade gateways and email security solutions. This campaign apparently use other tricks, but Microsoft did not specify which.
The company has shared an advanced hunting query defenders can use to block the emails from being delivered.