Storm-2603 spotted deploying ransomware on exploited SharePoint servers
One of the groups that, in the past few weeks, has been exploiting vulnerabilities in on-prem SharePoint installation has been observed deploying Warlock ransomware, Microsoft shared on Wednesday.
First attack spotted on July 7th
On Saturday, Microsoft announced that attackers have been spotted exploiting a zero-day variant (CVE-2025-53770) of a SharePoint vulnerability (CVE-2025-49706) that the company partially addressed with updates released on July 8th, 2025.
In the intervening days, some things have become clearer but other murkier.
For example, despite still saying it’s CVE-2025-53770 that is being exploited, the company’s blog post that pins the attacks on various Chinese threat actors says that the vulnerabilities being exploited are CVE-2025-49706, a spoofing vulnerability, and CVE-2025-49704, a remote code execution vulnerability. (Both partially patched in early July.)
Microsoft recently also cleared up the confusion on which new vulnerability was a variant (i.e., a patch bypass) of an older one:
- CVE-2025-53770 (insecure deserialization vulnerability allowing unauthenticated attackers to execute code over a network, i.e., remotely execute code) is related to CVE-2025-49704 (code injection flaw allowing authorized attackers to execute code over a network)
- CVE-2025-53771 (path traversal flaw that allows an unauthorized attacker to perform spoofing over a network) is related to CVE-2025-49706 (improper authentication vulnerability that allows authorized attackers to perform spoofing over a network and may allow them to to view sensitive information and make some changes to disclosed information).
While CVE-2025-53771 is the only one of the four that Microsoft’s security advisory and CISA have yet to mark/confirm as being exploited, other security companies say that it is.
Whatever the case may be, Microsoft has stated that attackers have been attempting to exploit CVE-2025-49704 and CVE-2025-49706 to gain initial access to target organizations since at least July 7h.
Check Point Research also said that the first exploitation attempts they detected happened on the same date, and that the target was a major Western government. Since then, more specific targets, both in the US and around the world, have been confirmed.
Storm-2603 exploits SharePoint vulnerabilities, deploys ransomware
“The TTPs employed in these exploit attacks align with previously observed activities of these threat actors,” Microsoft’s threat intelligence analysts say.
The threat actors in question are Chinese state-sponsored groups Linen Typhoon and Violet Typhoon, which concentrate on stealing intellectual property and espionage (respectively), and Storm-2603, another suspected China-based threat actor that seems primarily focused on deploying ransomware.
In past attacks, Storm-2603 deployed Warlock and Lockbit ransomware – this time around they reportedly stuck to using the former.
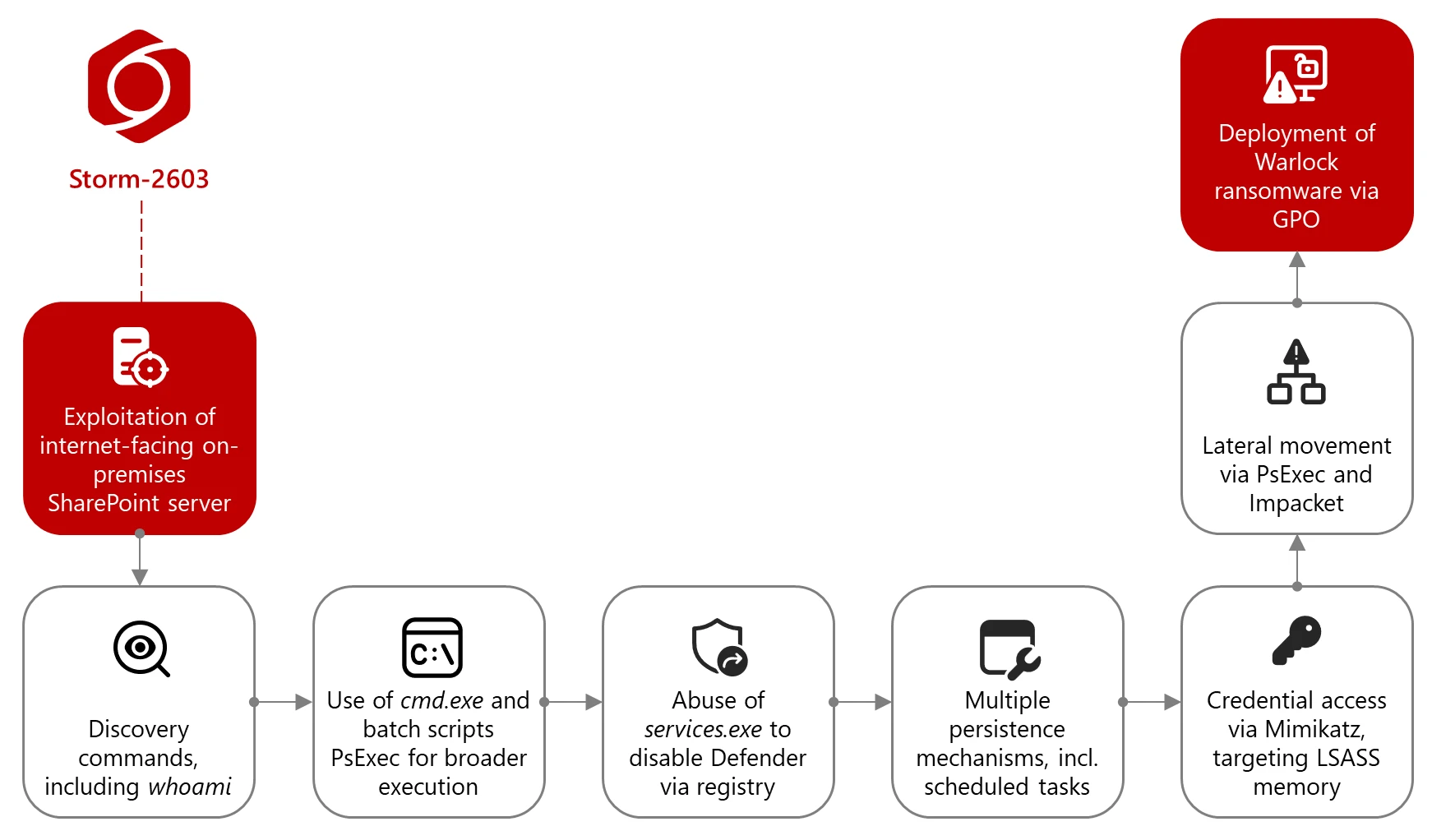
Storm-2603’s attack chain (Source: Microsoft Threat Intelligence)
In these latest attacks, Storm-2603 has been:
- Gaining access to vulnerable on-prem SharePoint servers by exploiting the aforementioned vulnerabilities
- Performing reconnaissance (i.e., enumerating user context and validating privilege levels)
- Disabling Microsoft Defender protections through direct registry modifications
- Establishing persistence by installing a web shell, creating scheduled tasks and manipulating Internet Information Services (IIS) components to load suspicious .NET assemblies
- Extracting plaintext credentials from Local Security Authority Subsystem Service (LSASS) memory with Mimikatz
- Moving laterally using PsExec (to escalate privileges), Impacket toolkit, and Windows Management Instrumentation (WMI)
- Modifying Group Policy Objects (GPO) to distribute Warlock ransomware in compromised environments.
More attacks by different groups are expected
The attacks witnessed so far are likely just the beginning.
With technical details on the original ToolShell attack chain (CVE-2025-49706 + CVE-2025-49704) having been made public, and CVE-2025-53770 PoC exploits being published on GitHub, other skilled attackers are likely to join the rush to take advantage of the (too slowly shrinking) pool of still vulnerable internet-facing on-prem SharePoint servers.
“SharePoint exploitation has now entered the parasitic phase,” SANS Internet Storm Center noted.
“We are seeing hits to more then 100 distinct possible web shell URLs. Some of them may just be guesses, but a good part of them are likely webshells created by the Toolshell exploit over the last couple days.”
All organizations’ whose on-prem SharePoint servers were internet-facing in the last month should operate under the assumption they’ve been compromised and proceed to investigate, install updates / mitigations, and rotate the ASP.NET machine keys.
UPDATE (July 25, 2025, 06:00 a.m. ET):
Kaspersky researchers have released a technical analysis of the exploits used and explained how Microsoft did an incomplete job with the CVE-2025-49704 and CVE-2025-49706 fixes.
They also pointed out the similarity between CVE-2020-1147, an old NET Framework, SharePoint Server, and Visual Studio RCE vulnerability, and CVE-2025-49704/CVE-2025-53770.
“In fact, if we compare the exploit for CVE-2020-1147 and an exploit for CVE-2025-49704/CVE-2025-53770, we can see that they are almost identical. This makes CVE-2025-53770 an updated fix for CVE-2020-1147,” they said.
Finally, they warned that despited complete patches now being available, they believe this chain of exploits will continue being used by attackers for a long time.
“We have been observing the same situation with other notorious vulnerabilities, such as ProxyLogon, PrintNightmare, or EternalBlue. While they have been known for years, many threat actors still continue leveraging them in their attacks to compromise unpatched systems. We expect the ToolShell vulnerabilities to follow the same fate, as they can be exploited with extremely low effort and allow full control over the vulnerable server.”
UPDATE (August 4, 2025, 08:45 a.m. ET):
Palo Alto Networks researchers have spotted ToolShell exploitation attempts leading to the deployment of 4L4MD4R ransomware.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!