Fixing silent failures in security controls with adversarial exposure validation
Organizations often operate as if their security controls are fully effective simply because they’re deployed, configured, and monitored. Firewalls are in place, endpoints are protected, and SIEM rules are running. All good, right? Not so fast. Appearances can be deceiving. And deception can be devastating.
Picus Security’s Blue Report 2025 shows that even well-configured environments continue to miss a substantial portion of attacks. In fact, across more than 160 million attack simulations, Picus Labs found that organizations are detecting only 1 out of 7 attacks, exposing a serious gap between perceived and actual security effectiveness.
This gap creates a false sense of security. Teams may believe they’re fully protected, yet attackers can move laterally within the organization’s networks, escalate privileges, and exfiltrate sensitive data, all without triggering alerts. This potentially catastrophic state of affairs highlights the need for a validation-first approach, where security controls are continuously tested to ensure they’re actually preventing real-world attacks.
Why security controls silently fail
Security controls are not set-and-forget tools. Even systems that perform perfectly in lab tests, some even scoring 100% in MITRE ATT&CK Evaluations, often fail in operational environments. Why? Several factors contribute to these silent failures:
- Configuration drift: Over time, firewall rules, endpoint policies, and detection thresholds often deviate from their original configurations due to updates, changes in business processes, or human error.
- Integration gaps: Security tools rarely operate in isolation. Misalignments and miscommunication between SIEMs, EDR platforms, network monitoring, and cloud security controls can leave blind spots, allowing attacks to bypass detection.
- Evolving threats: Attackers are continuously developing new tactics, techniques, and procedures (TTPs). A rule that successfully detected a threat six months ago may be blind to today’s stealthier version.
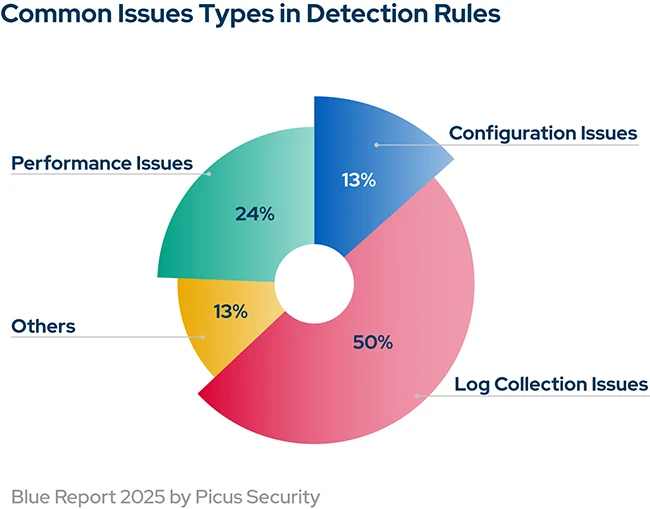
The Blue Report 2025 highlights the magnitude of these failures. A stunning 50% of detection rule failures stemmed from log collection issues alone, while misconfigurations caused 13% and performance bottlenecks accounted for 24%. These findings mean that security controls can fail undetected while giving the illusion of security, masking real vulnerabilities.
Adversarial Exposure Validation to the rescue
This is where Adversarial Exposure Validation (AEV) steps in to close the gap. Instead of assuming that security controls are working simply because they’re in place, AEV actually tests them against real-world attack behaviors. By simulating tactics that attackers actually use, ranging from credential theft to lateral movement and data exfiltration, AEV exposes the gaps that often go unnoticed in daily operations before they’re actually used against you.
Validation doesn’t just highlight problems; it also provides clear, actionable insights that you can actually use to solve problems and plug gaps. It shows which SIEM rules, firewalls, endpoint protections, and policies are genuinely effective and which need adjusting. For example, a firewall might appear fully configured, but testing may reveal a path that allows lateral movement or sensitive data to escape. With these insights, security teams can tune their controls with confidence, knowing they are truly protecting the organization.
Adapting controls for real-world effectiveness
Once they’ve identified their weaknesses, organizations must fine-tune their security stack. SIEM rules need threshold adjustments, refined correlation logic, and optimized filters to reduce noise and improve alert accuracy. Endpoint protections should cover high-risk behaviors such as lateral movement, privilege escalation, and exfiltration. Firewalls and network segmentation must be regularly tested and tuned to block unauthorized activity without disrupting business operations.
By definition, this process needs to be iterative. To combat a perpetually changing threat landscape, teams must always test to detect new and existing weaknesses, apply fixes, and continuously monitor their results. Continuous Threat Exposure Management (CTEM) formalizes this cycle, ensuring that validation and tuning are ongoing, adaptive, and tied to measurable improvements in detection and prevention. By repeatedly testing and refining controls against real-world adversary behaviors, organizations can maintain a resilient security posture even against evolving threats.
Practical benefits of validation for security teams
Implementing AEV and CTEM provides tangible, measurable benefits. Validation ensures that controls detect actual attacks, not just theoretical vulnerabilities, and by simulating adversary behaviors, teams uncover hidden gaps across their endpoints, networks, and cloud environments. With validated alerts and properly tuned rules, security teams can respond faster, reduce attacker dwell time, and dramatically improve their overall incident response.
Insights from AEV, combined with the Blue Report 2025’s findings, allow teams to prioritize remediation based on real risk, focusing on the most impactful gaps rather than chasing low-risk issues and hypothetical problems. For example, the report shows that many organizations fail to detect credential-based attacks and lateral movement despite deploying advanced tools to do so. Validation allows teams to confirm which controls are working, which aren’t, to prioritize security improvements, and mitigate the risks that matter the most.
Real-world implications: Lessons from the Blue Report 2025
This year’s Blue Report provides concrete evidence of silent failures in enterprise defenses:
- Detection gaps: Organizations detected only 1 out of 7 simulated attacks, showing that nominally active SIEM rules often fail silently.
- Credentials at risk: Password cracking is 46% successful in tested environments, and Valid Accounts (T1078) remain a top-exploited technique, with a 98% success rate in simulated attacks.
- Lateral movement: Many controls are bypassed during lateral movement, enabling attackers to access sensitive systems undetected.
- Performance and configuration issues: Misconfigured or inefficient SIEM rules, coupled with incomplete log collection, significantly reduce your alert and detection effectiveness.
Picus Security’s findings reinforce that your security controls cannot be assumed to be effective based on configuration or lab scores alone. Continuous validation ensures that teams are working with valid, real-world, actionable intelligence.
Ensuring your controls actually work
The Blue Report 2025 shows that unchecked assumptions about control effectiveness create real risk. By validating continuously with adversarial methods and embedding that practice into CTEM, organizations can focus resources on the gaps that matter most. The result is not just stronger detection and prevention, but measurable risk reduction where it counts.
See where your defenses are working and where they might be silently failing. Download the Blue Report 2025 for concrete, actionable insights and practical recommendations for validating and optimizing your security controls.
