Popular code formatting sites are exposing credentials and other secrets
Widely used code formatting sites JSONFormatter and CodeBeautify are exposing sensitive credentials, API keys, private keys, configuration files and other secrets, watchTowr researchers discovered.
The findings
JSONFormatter and CodeBeautify are free, web-based tools/services used by developers to make messy code easily readable, to validate it, or convert it.
Users can also save the output code, so they can share it with others. (If you use JSON Formatter without logging in and save the output, it will automatically become public, according to the site’s FAQ section).
Both sites have a Recent Links section, where links to saved, public outputs can be accessed by anyone. Unfortunately, even those links that have been saved but not made public can be accessed because, as it turns out, the created shareable links follow a predictable URL format.
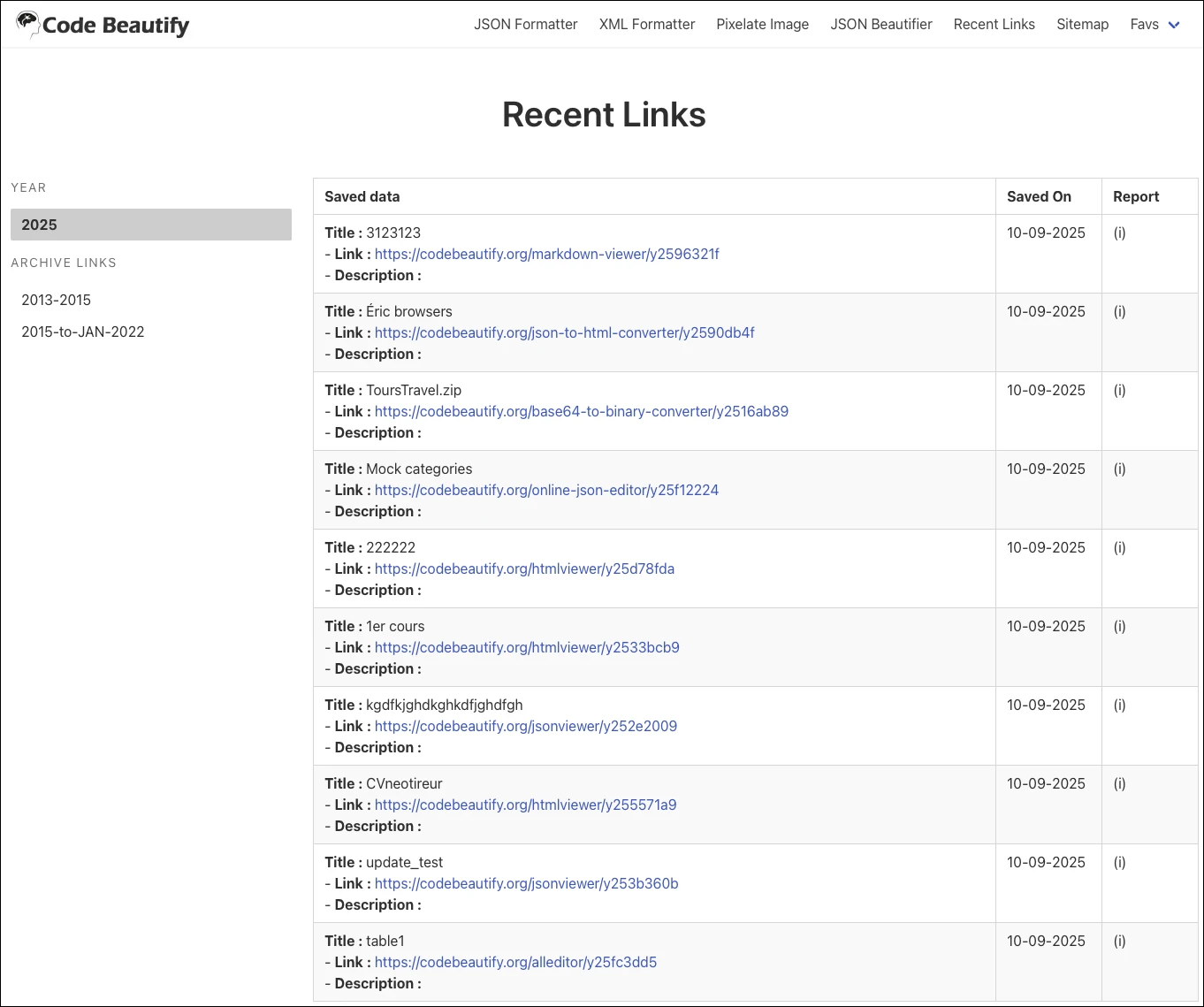
This allowed WatchTowr researchers to find and scrape more than 80,000 saved JSON entries, and they found an alarming amount of sensitive information: Active Directory credentials, GitHub tokens, cloud environment keys, private keys, CI/CD pipeline credentials, API keys, configuration information, SSH session recordings, personally identifiable information, and more.
Even more concerning was who these leaked secrets belonged to. The exposed data came from organizations across critical and highly regulated sectors, including government, finance (banking), healthcare, telecoms, retail, aerospace, education, and even cybersecurity.
Finally, the researchers decided to see whether malicious actors have thought about doing the same thing and whether they are trying to use thusly discovered secrets.
So, they created a number of canary tokens, pasted them into JSONFormatter and CodeBeautify, and waited. They didn’t have to wait long: 48 hours after their initial upload and save, someone attempted to use one of the exposed canary AWS keys.
“We’re not alone – someone else is already scraping these sources for credentials, and actively testing them,” the researchers noted, and decided to go public with their findings.
Before doing that, though, they tried to warn many of the organizations whose secrets were exposed on these sites, but only few acknowledged their heads-up.
A widespread problem
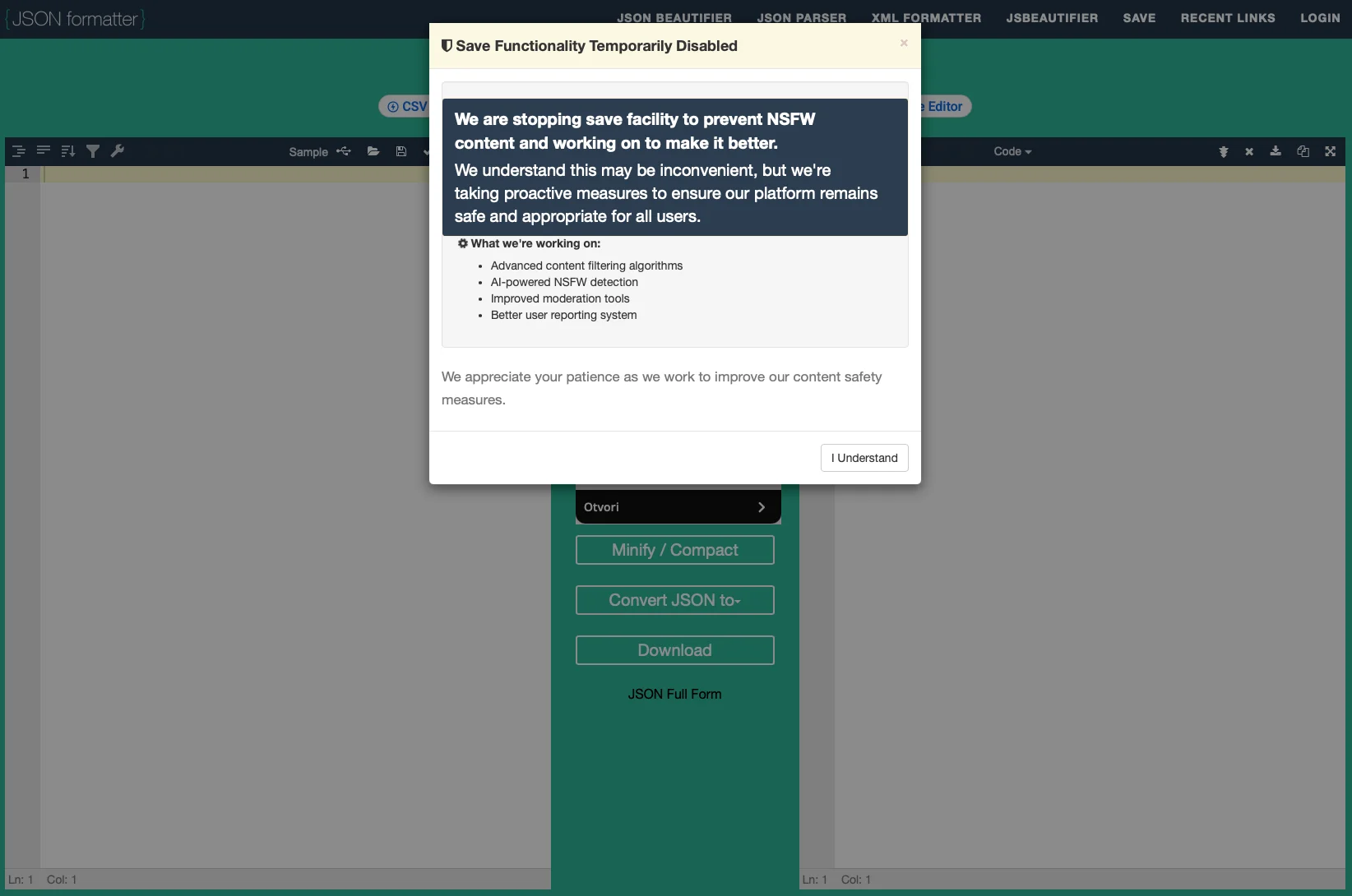
While the Recent Links section on JSONFormatter is currently impossible to reach and the site says its “Save” functionality has been temporarily disabled “to prevent NSFW content”, CodeBeautify’s Recent Links section can still be accessed.
But, as both watchTower and security researcher Kevin Beaumont pointed out, there are many other code formatter and beautifier websites out there, and it’s likely that some of them are leaking inputted secrets in the same way.
“We don’t need more AI-driven agentic agent platforms; we need fewer critical organizations pasting credentials into random websites,” the researchers concluded.
These sites may be convenient, but because they run entirely online, you should know that anything you paste into them can potentially be stored and exposed.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!