New image signature can survive cropping, stop deepfakes from hijacking trust
Deepfake images can distort public debate, fuel harassment, or shift a news cycle before anyone checks the source. A new study from researchers at the University of Pisa examines one specific part of this problem. They introduced a way to keep image signatures intact even after cropping.
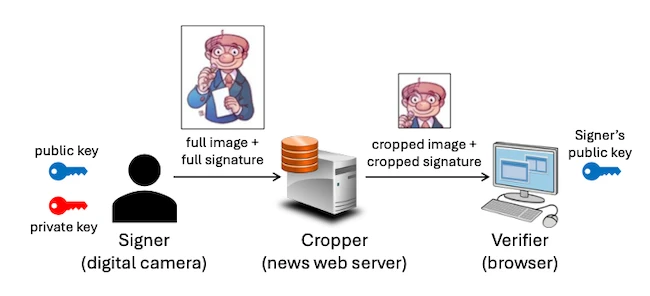
System model
Cropping remains a weak spot in image verification
Most authentication tools fail the moment a photo is altered. Even small changes like trimming edges turn a signed image into one that fails verification. That creates trouble for newsrooms and other groups that crop images as part of normal editing.
The research team writes that common signature schemes “are made less practical by the fact that images are often edited in legitimate ways before being published on the web, for example they are cropped or reduced in resolution.” Their goal was to protect this routine adjustment while still preventing altered scenes from passing verification.
In the system described by the researchers, the signer is the device or software that creates the original image, such as a camera or a newsroom tool. The cropper is any publisher or server that trims the image for layout. The verifier is the tool or browser that checks the signature on the cropped result. Only the signer holds a private key, a secret code that gives the source sole control over creating the signature.
A signature that survives a cut
The team built a system that applies their signing method to an image and keeps the signature valid even after cropping. Each piece corresponds to a block of the original photo. When someone crops the image, the verifier checks only the blocks that remain inside the cropped area. Any attempt to alter content inside these blocks or replace them with blocks from another image fails verification.
The researchers describe the core idea as keeping the signature “valid after image cropping, but invalidated in all the other types of manipulation.” The signature on the cropped image stays constant in size rather than expanding with the dimensions of the photo. This is important because the cropped version is the one that users download most often.
One detail worth noting is that block size affects how precise this process can be. Smaller blocks allow more precise verification of the cropped region. Larger reduce overhead but cover broader regions at once.
Stopping deepfakes from borrowing trusted signatures
The research team explains that the cropper “does not have to know the private key of the signer, nor to have his own private key.” The server cannot sign new content and cannot make altered images appear authentic. It can only pass along a cropped signature that comes from the original data.
The report uses the example of a digital camera that signs each photo. A newsroom or other publisher can crop that picture, but it cannot change what the camera captured. The system does not stop anyone from creating a deepfake, but it prevents a deepfake from carrying a signature that claims authenticity for the cropped region.
JPEG compatibility
Compatibility is a major concern for any authentication system. The authors adapted their approach to fit inside the JPEG format. They placed signatures in a standard comments section that common viewers ignore. As a result, regular software displays the picture without changes.
The study explains that JPEG compression introduces dependencies between blocks, which prevents direct signing of the compressed form. To work around this, the researchers use block data from the image before compression, then store the signature inside the JPEG file. This lets verification happen without changing how the image looks or works in standard software.