Why boards must prioritize non-human identity governance
Boards of Directors (BoDs) do three things exceptionally well when cyber is framed correctly. They set risk appetite, they allocate capital, and they demand evidence that the business can withstand disruption without losing momentum.
Why cyber keeps becoming a board topic
Boards typically address cybersecurity reactively. When material incidents occur, cyber becomes their top priority as disclosure requirements, customer impact, and financial exposure collapse into one event.
For example, U.S. public companies are required by the SEC’s cybersecurity disclosure rules to disclose material cybersecurity incidents under Item 1.05 of Form 8-K, generally within four business days of determining materiality. They must also describe governance and oversight, including the board’s role, in annual disclosures.
Oversight expectations are also rising. Deloitte’s Audit Committee Practices reporting shows that cyber sits squarely in audit committee priorities, with 50% of respondents identifying cybersecurity as the number one area of focus for their audit committee over the next 12 months. That same report found that 62% said audit committees have primary oversight of cybersecurity risk.
BDO’s 2025 Board Survey summary highlights that 63% of directors plan to increase strategic investment in cybersecurity in the year ahead.
Operational resilience is the bridge between board priorities and security reality
Operational resilience (the ability to keep delivering strategy through disruption) bridges board priorities with security reality. This means preventing incidents, reducing fragility, shrinking blast radius, and maintaining delivery speed under imperfect conditions.
According to PwC’s Global Digital Trust Insights, only 24% of organizations report spending significantly more on proactive measures than reactive measures, while 67% report spending is roughly even across both categories. PwC explicitly frames proactive investment as the healthier posture, and warns that reactive costs are often underestimated because they are dispersed across the business.
The identity layer is now the operations layer, especially for non-human identities
When boards discuss identity, they often default to human-focused initiatives like MFA and privileged access reviews. But modern businesses run on non-human identities, such as service accounts, CD/CD pipeline workers, microservices, and other workload identities that power integrations, automation, and cloud workloads.
CyberArk has reported that machine identities outnumber human identities by more than 80-to-1. Other estimates across the industry think we have crossed the 100-to-1 threshold as automation accelerates.
Most secrets exist because legacy systems are traditionally connected through password-based mechanisms. We reached for API keys and tokens as access mechanisms. These long-lived credentials, often over-privileged, have sprawled by the millions, making “secrets sprawl” really a symptom of non-human identity sprawl.
Making the business case with Gitguardian’s insights
GitGuardian’s “Hidden Cost of Secrets Sprawl” report is useful precisely because it quantifies what boards tend to suspect: credential chaos is a productivity tax.
Industry research quantifies credential chaos as a productivity tax. Manual secrets management costs organizations $172,000+ annually per 10 developers, based on three hours per week at $120 per hour fully loaded cost. These costs appear across engineering throughput, security bandwidth, onboarding timelines, incident response delays, and audit preparation, consuming the exact capacity needed to improve resilience.
Image from the Hidden Cost of Secrets Sprawl report
The board question to anchor the conversation
If you want to boil it down to one board-level question that forces clarity without dragging the room into technical weeds, it is this:
How are we governing non-human identities and their access, and what is our confidence in the inventory?
That single question ties to everything boards already care about:
- Risk appetite – unknown access creates unknowable exposure
- Continuity – fragile access breaks operations during change
- Accountability – “no owner” means “no control”
- Cost – manual access work is a measurable operational drag
- Crisis Response – containment speed depends on visibility and ownership
Don’t wait for them to ask this specific question; the goal is to answer it proactively before they know what to ask. Framing security, DevOps, and IAM work as a unified front that can speed innovation while limiting risks sets you up for wider success than focusing on a single tool choice or team-siloed initiative ever could.
Move toward full NHI Governance with GitGuardian
Moving from long-lived secrets to identity-based authentication requires genuine modernization, involving refactoring authentication patterns, adjusting CI pipelines, and building new governance capabilities. These programs often stall because feature work competes with reliability work.
GitGuardian can help you move towards true NHI Governance because our platform starts where the pain is most visible and measurable, then expands into where the long-term control must exist.
GitGuardian is likely best known for the State of Secrets Sprawl, our annual report on finding millions of publicly leaked credentials. That is indeed where we started our journey as an organization, focused on secrets. Along the way, we realized that secrets don’t exist in a vacuum, and what we have really been tracking all along is access mechanisms for identities, in particular, non-human identities.
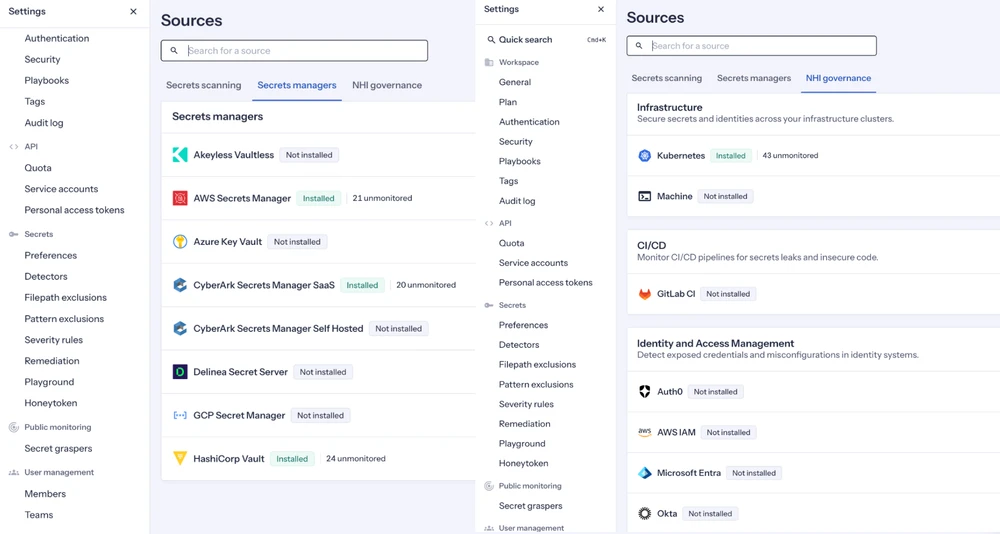
This shift might seem subtle at first, but the sea change is evident in the platform’s recent release notes, where we talk about expanding NHI Governance with integrations that discover and enumerate NHIs tied to platforms like Airbyte, Anthropic, N8n, OpenAI, CyberArk Secrets Manager Self Hosted, and Slack. The emphasis is on identity context, permissions, accessed resources, and an identity-first inventory view, not on new types of detectors.
GitGuardian Sources menu, showing identity providers and vaults
And right before we ended 2025, GitGuardian expanded NHI Governance coverage into additional critical platforms, including Datadog, Snowflake, Okta, and Auth0. We are now helping teams close blind spots and enabling unified identity risk assessment.
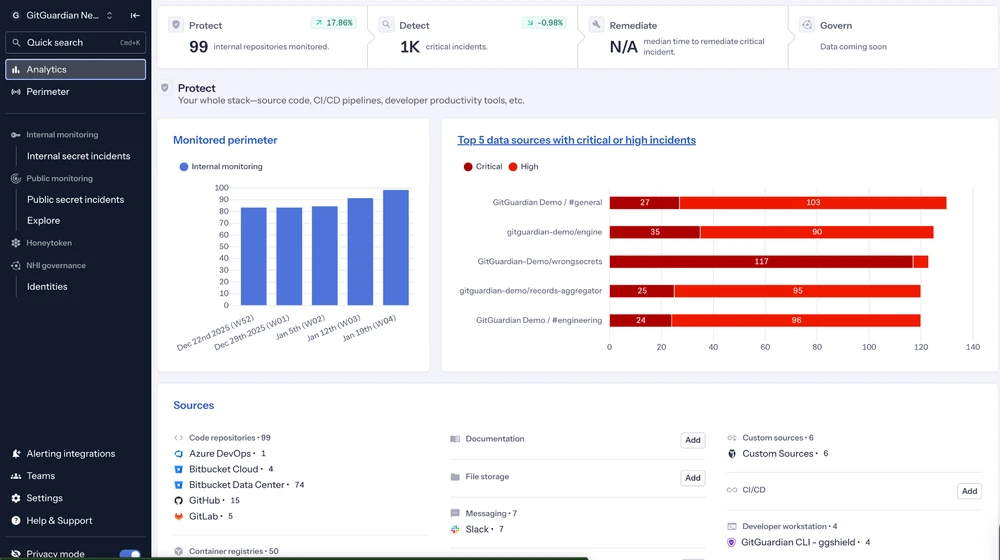
GitGuardian’s Analytics views give you the right information in real time
This aligns well with BoDs’ mindsets. It begins with exposure and operational friction that is already costing money, then builds toward a durable identity governance layer that scales with the business.
Partnering with GitGuardian can help you report periodically on NHI governance with trend lines, not just point-in-time snapshots. This includes progress on your modernization path away from long-lived credentials. Our platform will help you treat incident readiness as a control, including containment speed and the ability to rotate or revoke access without downtime.
We would be happy to set up a demo and help you align your next board of directors conversations with your operational realities and needs.