Brutus: Open-source credential testing tool for offensive security
Brutus is an open-source, multi-protocol credential testing tool written in pure Go. Designed to replace legacy tools that have long frustrated penetration testers with dependency headaches and integration gaps, Brutus ships as a single binary with zero external dependencies and native support for the JSON-based reconnaissance pipelines that define offensive security.
Solving a real workflow problem
Credential testing should be straightforward: you have a list of services and a set of credentials, and you need to find out what works. In practice, operators spend more time wrangling dependencies, parsing inconsistent output, and writing glue scripts than actually testing credentials. Tools like THC Hydra and Medusa have served the security community for years, but they carry significant friction: complex dependency chains that break across platforms, compilation issues on every new jump box, and no native integration with the structured recon workflows that teams rely on.
Brutus was purpose-built to close that gap. Reconnaissance flows through tools like naabu for port scanning and fingerprintx for service identification, with everything structured as JSON streams. Credential testing was the broken link in that chain. With Brutus, operators can pipe discovered services directly into credential testing and get structured results back, with no format conversion, no manual parsing, no platform-specific workarounds.
What Brutus brings to the table
Brutus supports 22 protocols out of the box:
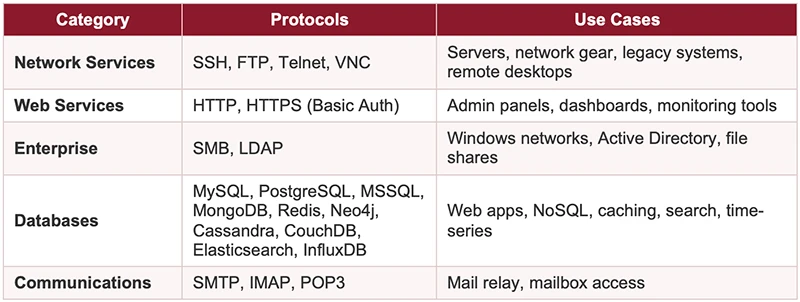
All of this ships in a single binary that runs identically on Linux, macOS, and Windows with no external libraries or compilation required.
One feature that consistently draws attention from practitioners is the embedded SSH bad key testing. Brutus carries the Rapid7 ssh-badkeys and HashiCorp Vagrant key collections compiled directly into the binary, with no external key files to manage. Every SSH service is automatically tested against known-compromised keys from vendors including F5 BIG-IP, ExaGrid, Barracuda, Ceragon, and Array Networks, each paired with its default username and tracked by CVE where applicable.
On internal assessments, operators know there are Vagrant boxes or appliances running factory keys somewhere in the environment, but testing for them comprehensively has always been tedious enough to get deprioritized. With Brutus, it happens automatically as part of the normal workflow, and what used to be a half-day side project now comes for free. The embedded key collection is a starting point, and the team is hoping the community will contribute additional bad keys encountered in the wild.
Beyond the CLI, Brutus also functions as a Go library, allowing developers to import it directly into custom security automation tools without shelling out to external processes.
AI-powered credential discovery
Perhaps the most ambitious feature is the experimental AI integration. Using Claude’s vision capabilities paired with headless browser control, Brutus tackles a problem that has never had a good automated solution: unidentified web admin panels. On any internal assessment, operators encounter dozens of login pages on non-standard ports, including switches, storage appliances, IPMI consoles, and monitoring tools. Traditionally, that means a manual process of screenshotting each page, identifying the product, searching for default credentials, and testing one at a time.
Brutus automates the entire cycle. It renders the page in a headless browser, uses AI vision to identify the appliance or application, researches likely default credentials, then controls the browser to fill in the login form and test them. The approach handles JavaScript-rendered forms, CSRF tokens, and multi-step logins, all the things that break traditional form-filling tools. For HTTP Basic Auth targets, Brutus captures HTTP headers, identifies the device from server information and authentication realm data, and tests suggested credential pairs automatically.
What is next
On the AI front, the team is focused on optimizing the agentic features for scale. Per-target credential discovery works well, but across hundreds of HTTP services the latency and cost of LLM calls add up. Smarter batching, device identification caching, and reducing redundant API calls are all in development. The team believes that embedding agentic AI into security tooling will shift from experimental to expected as inference costs continue to fall.
A key initiative is building a community-driven templating system, similar in spirit to Nuclei templates, that lets practitioners define default credentials for specific appliances and devices. The vision is that AI becomes the fallback for targets not covered by existing templates, and better yet, the AI can develop new templates on the fly as it identifies uncatalogued appliances, making the tool self-improving over time.
On the protocol side, RDP remains the top priority. The team built an RDP implementation once using Rust FFI but pulled it because it was not reliable enough to ship. The path forward includes NLA detection and testing for common findings like Sticky Keys backdoors on internal assessments. Rather than ship a broken protocol, the team chose to maintain the core promise: everything in the tool just works.
Brutus is open source and available now on GitHub. The team welcomes community contributions, particularly additional SSH bad keys from appliances and vendor products encountered in the wild.

Must read:
- 40 open-source tools redefining how security teams secure the stack
- Firmware scanning time, cost, and where teams run EMBA

Subscribe to the Help Net Security ad-free monthly newsletter to stay informed on the essential open-source cybersecurity tools. Subscribe here!
