One stolen credential is all it takes to compromise everything
Attackers often gain access through routine workflows like email logins, browser sessions, and SaaS integrations. A single stolen credential can give them a quick path to move across systems when access permissions are broad and visibility is fragmented.
That pattern appears across more than 750 incident response engagements covered in Unit 42’s Global Incident Response Report 2026. In 87% of cases, attacker activity crossed multiple attack surfaces, meaning investigators had to trace behavior across endpoints, identity systems, networks, and cloud services within the same intrusion.
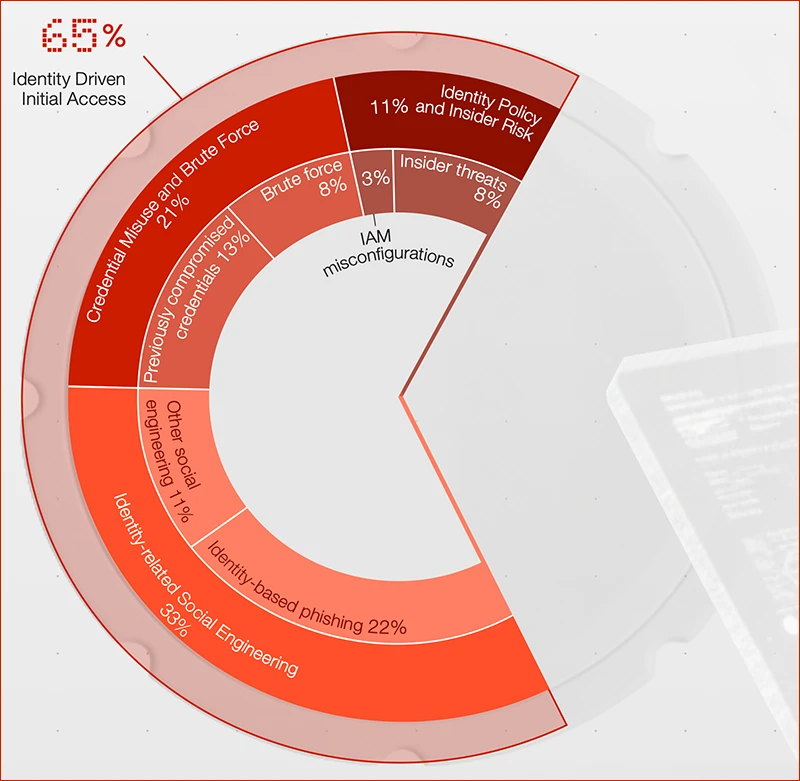
The data highlights identity as the dominant driver of initial access in modern intrusions (Source: Palo Alto Networks)
Identity is driving most intrusions
Identity-based compromise dominated incident response activity in 2025. Identity weaknesses played a material role in almost 90% of investigations. Initial access was driven by identity-based techniques in 65% of cases, including phishing, stolen credentials, brute force attempts, and insider activity.
“In our investigations, we’ve seen a wide range of identity security challenges that attackers are looking to exploit including: excessive permissions; lack of MFA or MFA that is not phishing resistant (relying on session tokens that can be captured via AitM); use of default passwords, re-used credentials or credentials that aren’t routinely rotated; Identity and Access Management misconfigurations; unmanaged or unmonitored OAuth grants; not disabling stale or initiative accounts; shared accounts with too many people using the same credentials; Shadow IT or unmanaged local identities,” Sam Rubin, SVP of Consulting and Threat Intelligence at Unit 42, Palo Alto Networks, told Help Net Security.
Phishing and vulnerability exploitation tied as the top initial access vectors at 22% each. Credential misuse and brute force remained significant, with previously compromised credentials at 13% and brute force at 8%. Social engineering beyond phishing continued to grow, reaching 11%.
Session hijacking and token theft increasingly allow attackers to bypass MFA. OAuth misuse and long-lived access tokens support persistence inside SaaS platforms without repeated authentication prompts. Trust relationships between applications also create lateral movement paths.
Rubin said the growing dominance of identity attacks reflects how enterprise environments have changed over the past few years, creating more opportunities for adversaries to quietly slip in through legitimate access pathways.
“The increasing role of identity as the main attack vector is a result of a fundamental change in the enterprise environment,” Rubin said. “This dynamic is driven by two key factors.”
He said the first driver is the rapid expansion of SaaS adoption, cloud infrastructure, and machine identities, which in many organizations now outnumber human accounts. That shift has created what he described as a “massive, unmanaged shadow estate,” where each integration represents “a new, potentially unmonitored, path into the network.”
Cloud environments amplify the risk. Unit 42 analysis of over 680,000 cloud identities found that 99% of cloud users, roles, and services had excessive permissions, including access that had gone unused for 60 days or longer. Over-permissioned identities create predictable escalation paths once an attacker gains a foothold.
The second driver, Rubin said, is that adversaries have adapted their playbooks to take advantage of this sprawling identity footprint, leaning heavily on stolen credentials that allow them to blend into legitimate activity.
“They are not breaking in; they are logging in,” Rubin said. “This activity, which often blends seamlessly into normal enterprise traffic, severely challenges the detection capabilities of even mature security defenders.”
Browser activity is a growing entry point
Browser-based activity played a role in 48% of investigations, up from 44% the prior year. Many attacks began with users visiting malicious sites through search engine results, clicking sponsored links, or downloading tampered tools.
Unit 42 described incidents where attackers used SEO poisoning to redirect users to spoofed sites. In one case, an employee searching for a restaurant was redirected to a malicious page that prompted them to execute copied code. In another case, a spoofed administrative tool was shared internally, leading to ransomware deployment after a privileged user executed the software.
These cases show how common web browsing can become the starting point for memory-resident malware, credential theft, and broader compromise.
AI is accelerating intrusion timelines
Attack speed continued to increase in 2025, and AI was part of that shift. Researchers observed threat actors using AI to speed up reconnaissance, write social engineering messages, and generate scripts used during ransomware deployment.
The time window for defenders is shrinking. The fastest 25% of intrusions reached data exfiltration in 72 minutes in 2025. The same metric was 285 minutes in 2024. A separate simulation described an AI-assisted attack that reached exfiltration in 25 minutes.
Threat actors also began automating extortion operations. Unit 42 negotiators observed consistent tone and cadence in ransom communications, suggesting partial automation or AI-assisted negotiation messaging.
AI-enabled tradecraft is expanding into new territory. Researchers described “living off the AI land” activity, where attackers misuse legitimate enterprise AI platforms. Compromised credentials can turn internal AI assistants into a reconnaissance tool, allowing adversaries to query internal documentation, system guides, or operational runbooks at scale.
Supply chain exposure keeps expanding
Supply chain risk continues to shift beyond vulnerable software packages. SaaS integrations, remote management tools, and vendor platforms increasingly provide paths for downstream compromise.
SaaS application data played a role in 23% of cases in 2025, up from 18% in 2024 and 6% in 2022. OAuth apps and API integrations often hold broad permissions that remain active even after employees leave or workflows change. Dormant connectors create hidden access paths that many organizations fail to monitor.
Vendor remote monitoring and management tools also remain attractive. Unit 42 found that 39% of command-and-control techniques were related to remote access tools.
Open source dependency sprawl continues to increase risk in build pipelines. Researchers stated that more than 60% of vulnerabilities in cloud-native applications reside in transitive dependencies. Attackers have also injected malicious code into upstream packages that execute during installation, giving them access to build environments before deployment.
Extortion tactics are shifting
Encryption appeared in 78% of extortion incidents in 2025, down from above 90% in prior years. Data theft remained steady, appearing in more than half of cases year over year.
Median ransom demands increased from $1.25 million in 2024 to $1.5 million in 2025. Median payments increased from $267,500 to $500,000. Organizations that negotiated achieved a median reduction of 61% between the initial demand and final payment.
Backup recovery remained a major factor in resilience. About 41% of victims restored systems from backups. Attackers impacted backups in 26% of extortion cases, creating additional downtime and pressure during recovery.

Download: Tines Voice of Security 2026 report