Researchers uncover ClickFix-themed phishing kit
Palo Alto Networks researchers have discovered and analyzed “IUAM ClickFix Generator”, a phishing kit that allows less skilled attackers to infect unsuspecting users with malware by using the increasingly popular ClickFix social engineering technique.
“This tool allows threat actors to create highly customizable phishing pages that mimic the challenge-response behavior of a browser verification page commonly deployed by Content Delivery Networks (CDNs) and cloud security providers to defend against automated threats. The spoofed interface is designed to appear legitimate to victims, increasing the effectiveness of the lure,” the researchers noted.
The IUAM ClickFix Generator
The IUAM ClickFix Generator is a web application, and the iteration the researchers discovered was accessible on a specific IP address from mid-July to early October 2025.
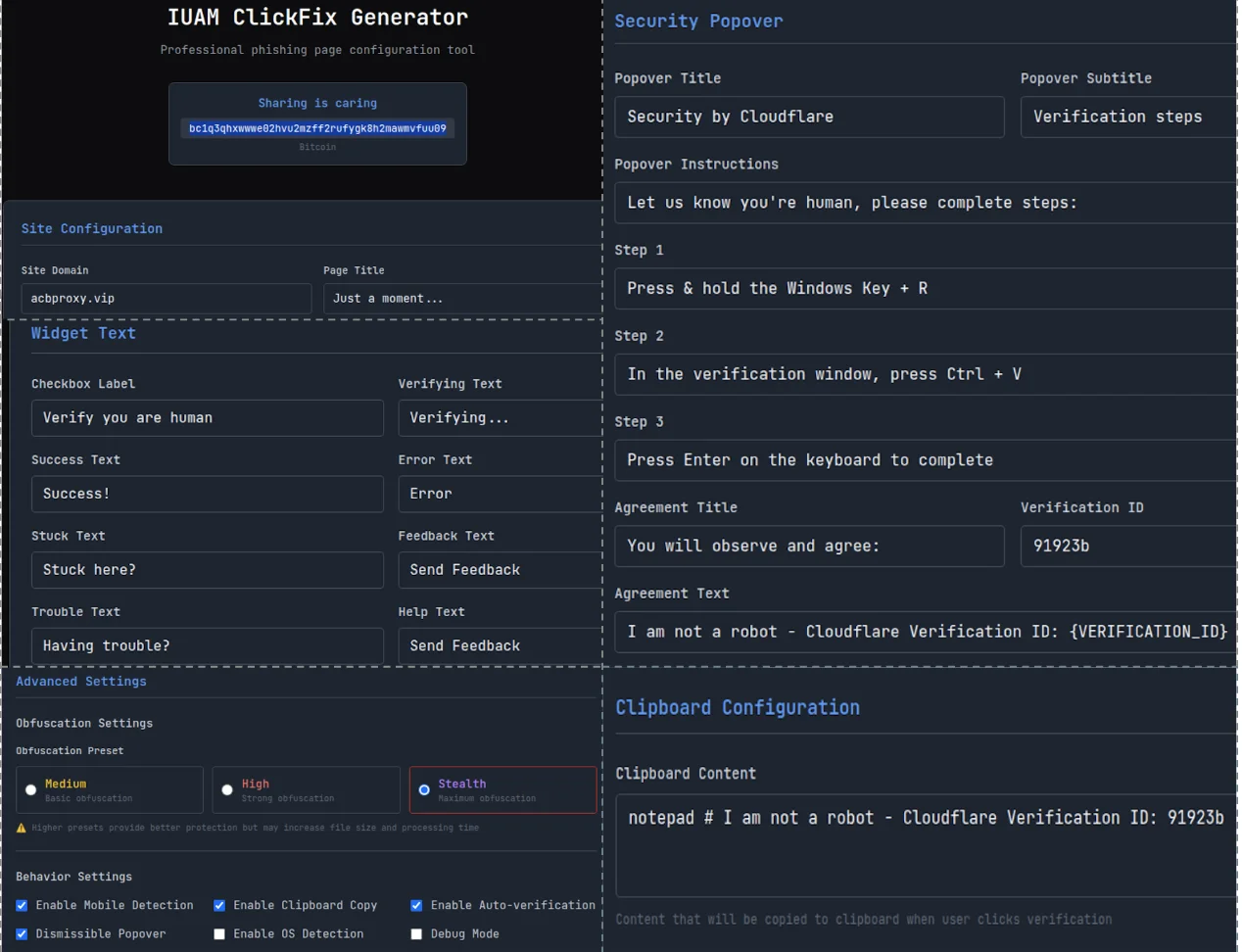
It showed a simple user interface that allowed malicious users to:
- Customize the title, domain, content and prompts shown by the phishing page
- Customize the content (i.e., malicious command) that will be copied to the victim’s clipboard if they click on the verification prompts
- Make the page detect whether the potential victim is using a mobile device, a Windows or a macOS machine to access it, and to show a prompt requiring them to switch to a desktop browser and tailor the malicious command to the specific desktop OS
- Enable obfuscation techniques and automatic clipboard-copy JavaScript injection
The IUAM ClickFix Generator user inerface (Source: Palo Alto Networks)
The researchers have unearthed several ClickFix-themed phishing pages created by the IUAM ClickFix Generator or a variant of it. The pages were made to target Windows or macOS users and deliver infostealers.
One of the spotted campaigns was tied to the Odyssey malware-as-a-service (MaaS) offering and its creator, and the variations in the phishing pages used may “reflect customized deployments of a base toolkit distributed by the malware operator or their affiliates.”
“According to posts published by the actor who advertises and operates the Odyssey MaaS, the actor has allegedly supplied ClickFix-style lure pages to affiliates upon request. This further supports the theory that these variants originate from a common generator tool but are tailored per affiliate, campaign or individual preferences,” the researchers added.
“The commoditization of [the ClickFix] technique follows the trend of phishing-as-a-service, lowering the skill and effort required to conduct successful attacks.”

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!