Attackers are exploiting Gladinet CentreStack, Triofox vulnerability with no patch (CVE-2025-11371)
CVE-2025-11371, an unauthenticated Local File Inclusion vulnerability in Gladinet CentreStack and Triofox file-sharing and remote access platforms, is being exploited by attackers in the wild.
While Gladinet is aware of the vulnerability and of its exploitation, a patch is still in the works. In the meantime, users can and should mitigate the flaw by disabling a handler within their installation’s Web.config file.
“We have observed in-the-wild exploitation of this vulnerability impacting three customers so far,” Huntress researchers warned, and advised organizations using Gladinet’s solutions to implement the mitigation as soon as possible.
CVE-2025-11371 exploited
CentreStack is a file-sharing, sync, and remote access platform aimed at managed service providers and small businesses. Triofox is a secure file-access/gateway solution for medium and large businesses, which allows users to access files without having to use a VPN.
Both solutions can be self-hosted, on-premises or in the organization’s cloud, or hosted in Gladinet’s cloud.
According to its CVE entry, CVE-2025-11371 affects the default installation and configuration of Gladinet CentreStack and TrioFox in the latest available version – 16.7.10368.56560 – as well as all earlier version.
Huntress observed CVE-2025-11371 exploitation on September 27, 2025, on a customer’s CentreStack instance that was running a version later that version 16.4.10315.56368, i.e., a version with a fix for CVE-2025-30406, a previously exploited and patched ViewState deserialization vulnerability.
Huntress’ investigators say that CVE-2025-11371 allowed threat actors to retrieve the machine key from vulnerable applications’ Web.config file, use it to forge ASP.NET ViewState payloads that will pass the solution’s integrity checks, and trigger remote code execution by causing unsafe server-side deserialization (CVE-2025-30406) of the forged payload.
“Attackers are able to access any file on the file system remotely without authentication as a result of [CVE-2025-11371],” Jamie Levy, director of adversary tactics at Huntress, told Help Net Security.
Waiting for a fix
“During our investigation, we saw evidence that Gladinet had engaged with a mutual customer to implement a mitigation,” Huntress researchers noted.
“Huntress reached out to Gladinet shortly after this discovery to disclose the flaw, per our standard vulnerability disclosure policy; Gladinet confirmed that it was aware of the vulnerability and was in the process of notifying customers of an immediate workaround.”
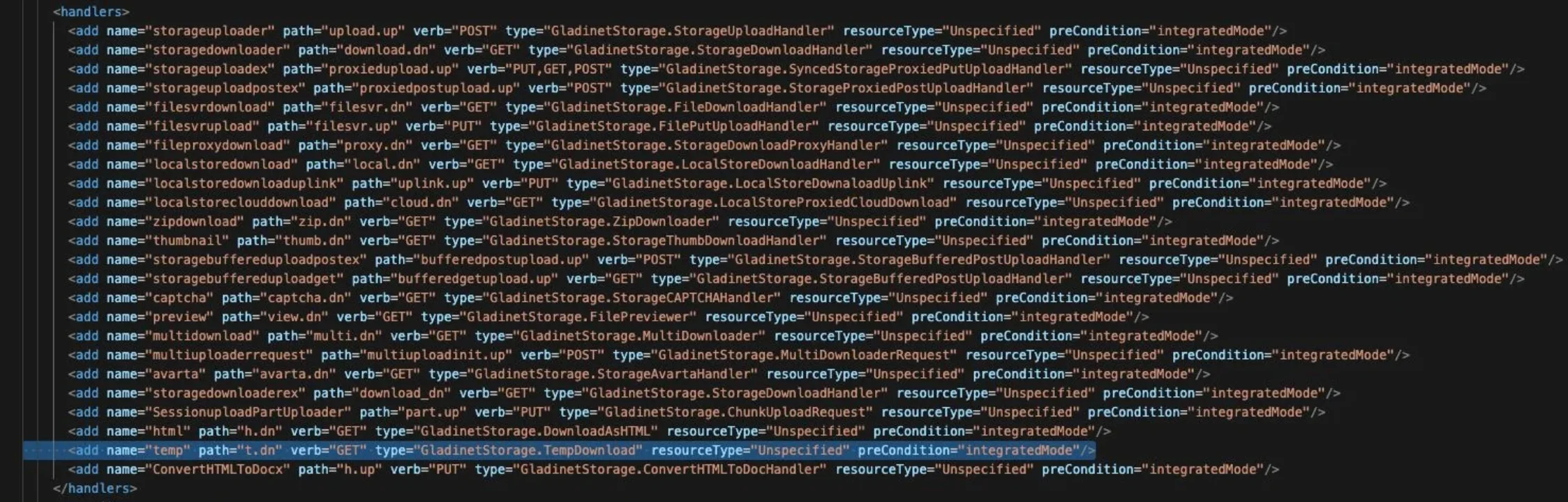
The mitigation for this in-the-wild exploited issue is to remove a specific line within the Web.config file located at C:\Program Files (x86)\Gladinet Cloud Enterprise\UploadDownloadProxy\Web.config.
The line that should be removed (Source: Huntress)
“This will impact some functionality of the platform; however, it will ensure that this vulnerability cannot be exploited until it is patched,” the researchers added.
There are still many unknowns
Huntress has blocked the attack before they could see what further malicious activity the attackers were planning.
In the attacks exploiting CVE-2025-30406 earlier this year, the attackers tried to download a malicious executable file, install a remote access tool, and perform lateral movement.
Help Net Security has reached out to Gladinet for more information about the issue and about the attacks and we will update this article if we hear back from them.
UPDATE (October 10, 2025, 05:45 p.m. ET):
Based on additional information provided by Huntress’ director of adversary tactics, this article has been updated to make the exploitation process clearer.
UPDATE (October 17, 2025, 04:05 a.m. ET):
Gladinet has patched CVE-2025-11371 and users should either upgrade to the fixed CentreStack version 16.10.10408.56683, or implement the mitigation outlined by Huntress’ researchers.
The researchers have also shared some technical details about the LPI vulnerability and have released a proof-of-concept PowerShell request that retrieves the Web.config file via the discovered unauthenticated endpoint (but does not perform the remote code execution).

Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!